The list of monetization tactics a cybercriminal can take advantage of, once they manage to hijack a huge portion of Web traffic, is virtually limitless and is entirely based on his experience within the cybercrime ecosystem.
Through the utilization of blackhat SEO (search engine optimization), RFI (Remote File Inclusion), DNS cache poisoning, or direct impersonation of popular brands in spam/phishing campaigns tactics, on a daily basis, traffic is sold and resold for achieving a customer’s or a seller’s fraudulent/malicious objectives, and is then most commonly converted to malware-infected hosts.
In this post, I’ll profile two cybercrime-friendly iFrame traffic exchanges, with the second ‘vertically integrating’ by also offering spamming services, as well as services violating YouTube’s ToS (Terms of Service) such as likes, comments, views, favorites and subscribers on demand, with an emphasis on the most common ways through which a potential cybercriminal can abuse any such traffic exchange network.
More details:
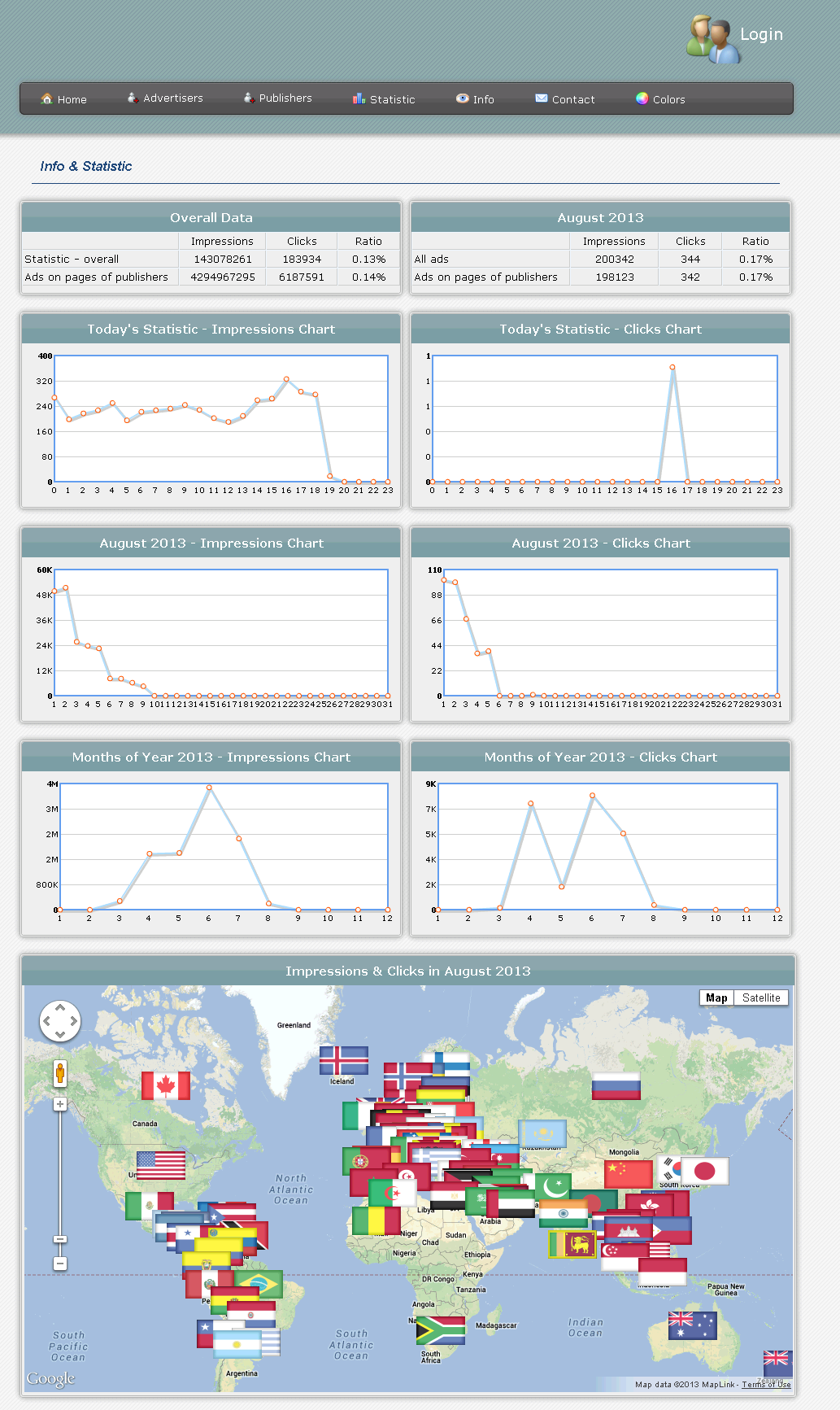
Sample screenshot of the statistics for the cybercrime-friendly iFrame traffic exchange:
The sudden peaks of traffic activity clearly indicate that this OPSEC-aware — lack of advertising, doesn’t list the participating sites, has no ToS, etc. — traffic exchange is failing to achieve a scalable and efficient approach for the acquisition of new publishers.
The second service not only offers a variety of traffic purchasing methods, but also, has a ToS (Terms of Service) explicitly prohibiting the use of malware and exploits. Now, what could go wrong with that? Historically, cybercriminals are known to have been mixing both legitimate and purely malicious infrastructure to achieve their objectives. With this in mind, it shouldn’t be surprising that a potential cybercriminal could easily abuse the massive traffic — based on their business pitch — aggregated by the second service, largely thanks to its lack of skills, experience and technical know-how when enforcing its ToS (Terms of Service).
Moreover, the service is also relying on basic ‘vertical integration’ practices in an attempt to acquire more customers by offering pseudo email marketing service, and services violating YouTube’s ToS.
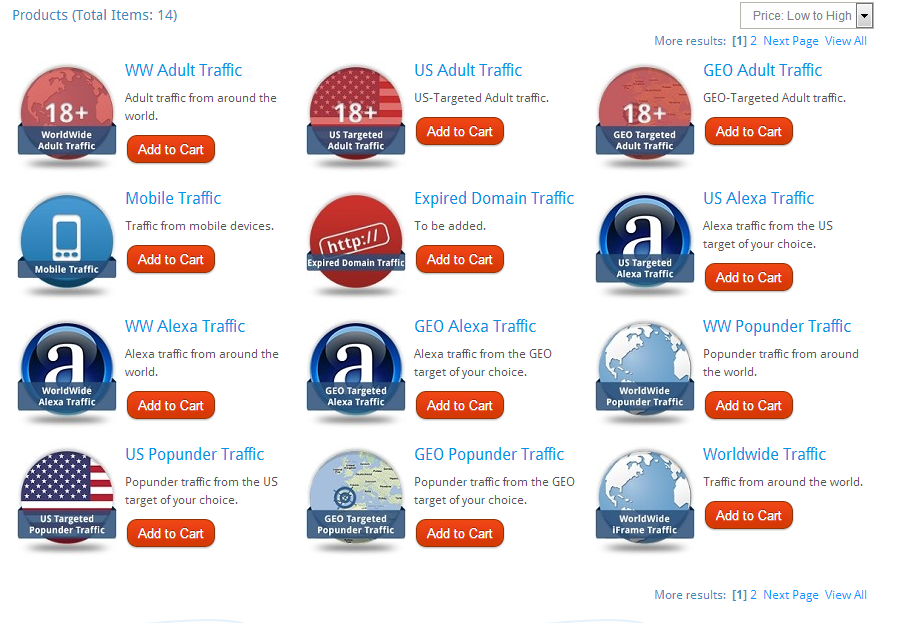
Sample screenshots of the traffic inventory offered for sale:
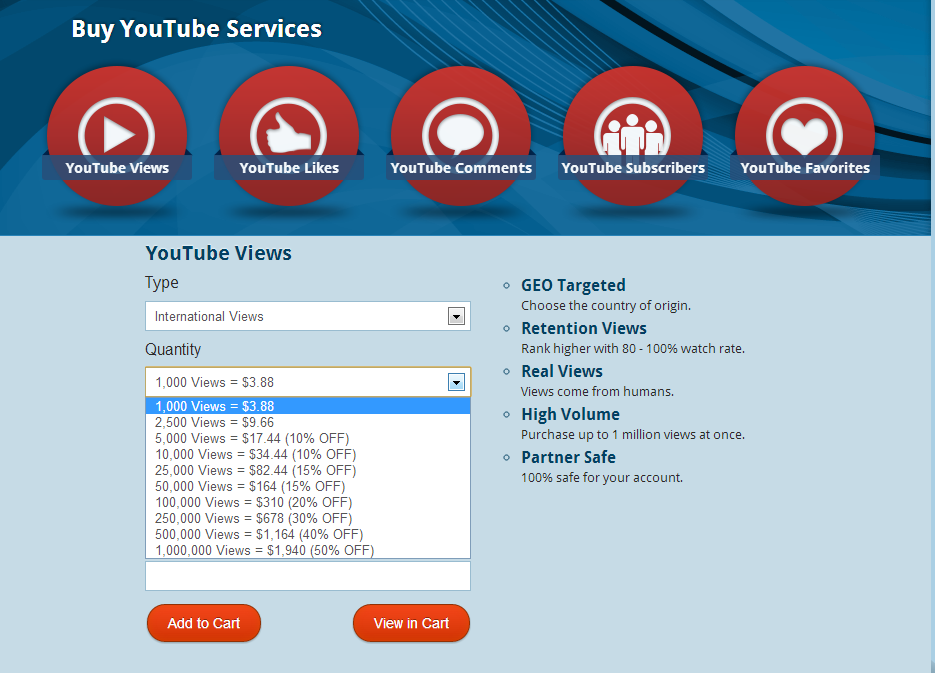
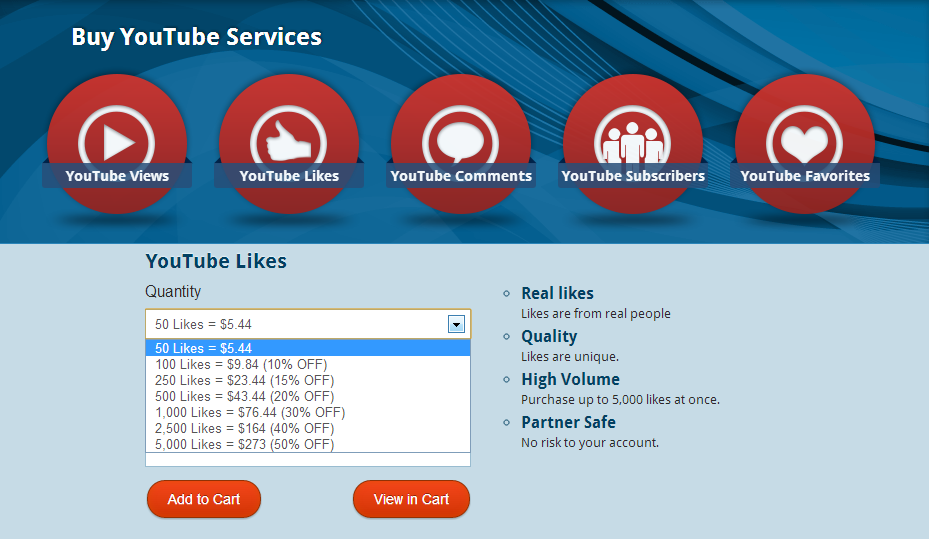
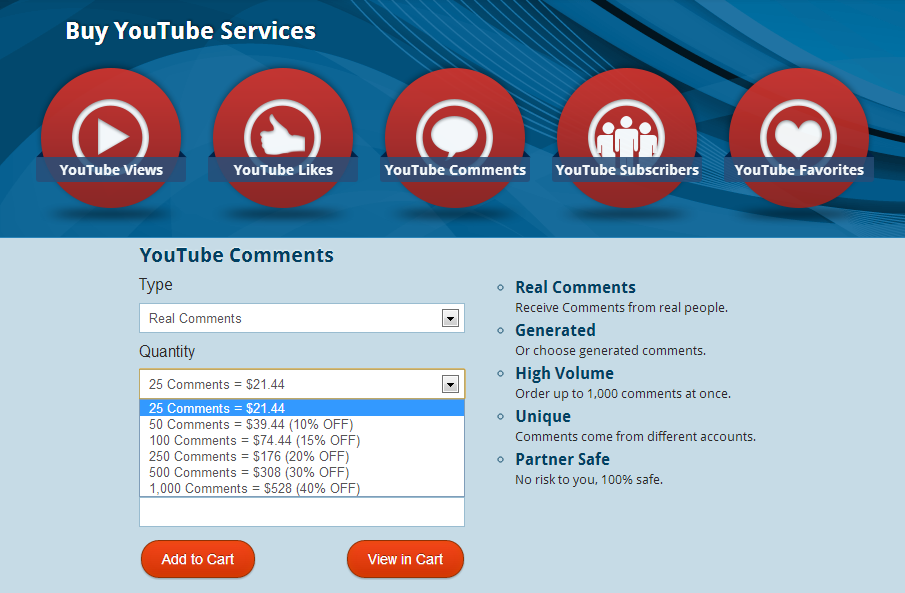
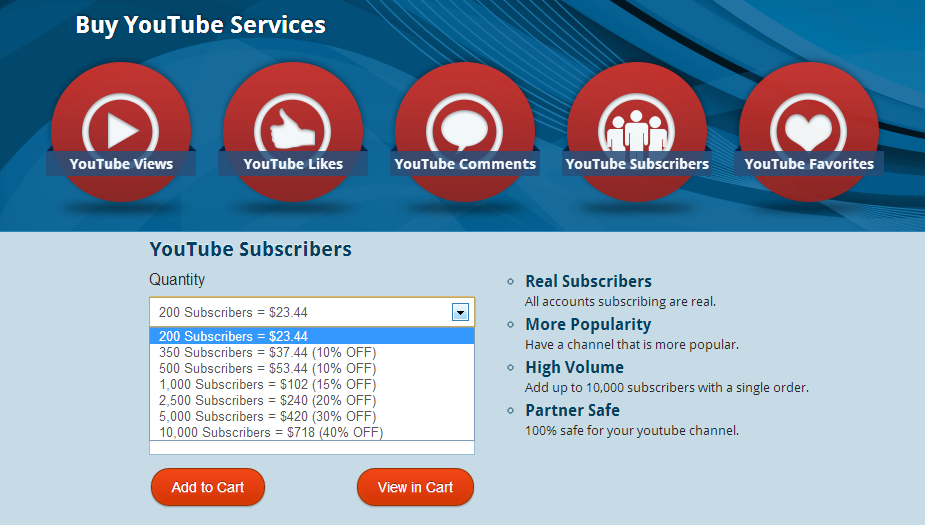
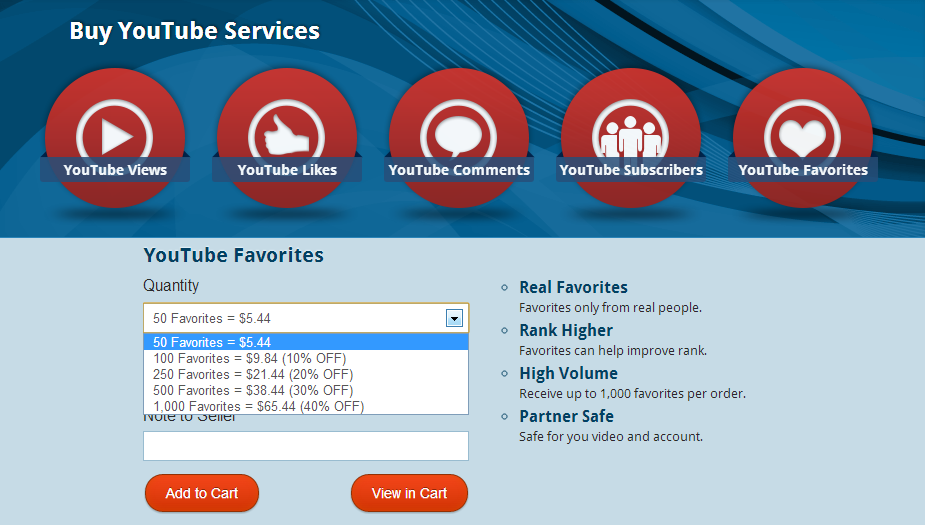
Sample YouTube ToS violating services:
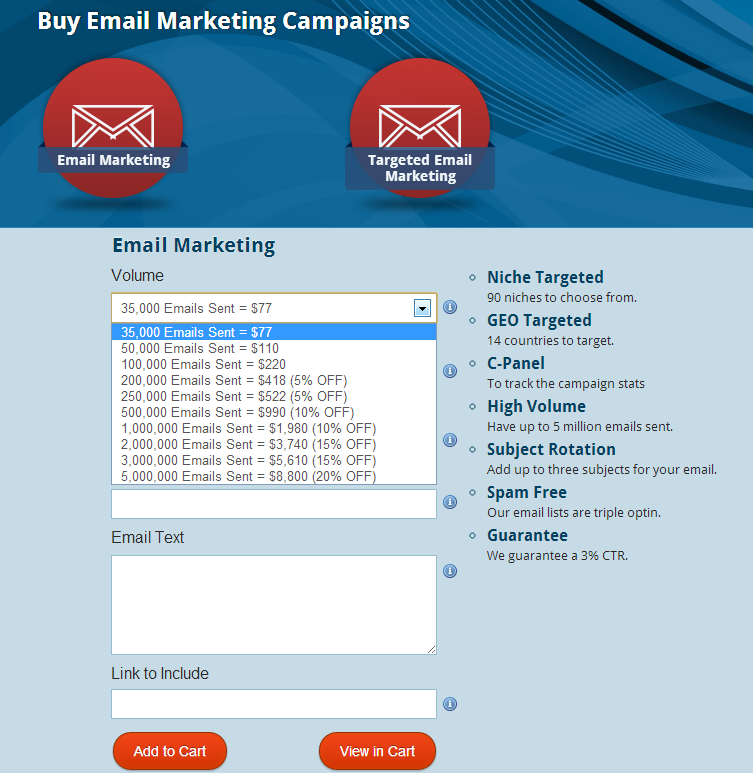
Sample screenshot of the “email marketing” service:
We expect to continue observing more iFrame traffic exchanges popping up on our radar, whose activities we’ll continue profiling in an attempt to put the spotlight on this monetization tactic/direct infection vector.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.








I am HACKED and I have Rebroot but the hacker won’t let me through to them He intercepts the email & code fromthem
Bonnie, please reach out to our Technical Support Team at your earliest convenience to review your Computer.
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send a Support Ticket