A new form of ransomware has hit the scene, and although this one has a playful nickname it is no fun at all. The bad news is that “Locky” ransomware will encrypt virtually every commonly used file-type and targets not only local drives, but any networked drives it can find, even if they are unmapped. The good news is that Locky is easily preventable because it relies on MS Word Macros to download and execute the actual malware. The only way to infect a computer with Locky ransomware is to open the attached document from a spam e-mail and allow the Word Macro script to run. (For a general overview of this type of execution, see our blog post about Microsoft Word & Excel Macros.)
Locky is most commonly distributed through spam e-mails that have similar subjects and messages. The subject is typically something like “ATTN: Invoice J-123456748” and the message is usually “Please see the attached invoice (Microsoft Word Document) and remit payment according to the terms listed at the bottom of the invoice”. If the victim follows the instructions to enable Macros, the script will download the Locky payload from a remote server and execute it.
The Locky executable will be stored and run from the %Temp% folder and it will immediately create and assign a unique 16-character Hexadecimal name to the victim (something like “A8678FDE2634DB5F”) which is then sent to the remote server for tracking and identification purposes. Once the Locky executable has launched and assigned the victim a unique ID, it will immediately begin scanning drives for files to encrypt. Not only will it encrypt local files, but it will search for any remote drives it can find (even unmapped network shares) and will encrypt their files as well.
Locky will use the AES encryption algorithm to encrypt all files with the following extensions:
.mid, .wma, .flv, .mkv, .mov, .avi, .asf, .mpeg, .vob, .mpg, .wmv, .fla, .swf, .wav, .qcow2, .vdi, .vmdk, .vmx, .gpg, .aes, .ARC, .PAQ, .tar.bz2, .tbk, .bak, .tar, .tgz, .rar, .zip, .djv, .djvu, .svg, .bmp, .png, .gif, .raw, .cgm, .jpeg, .jpg, .tif, .tiff, .NEF, .psd, .cmd, .bat, .class, .jar, .java, .asp, .brd, .sch, .dch, .dip, .vbs, .asm, .pas, .cpp, .php, .ldf, .mdf, .ibd, .MYI, .MYD, .frm, .odb, .dbf, .mdb, .sql, .SQLITEDB, .SQLITE3, .asc, .lay6, .lay, .ms11 (Security copy), .sldm, .sldx, .ppsm, .ppsx, .ppam, .docb, .mml, .sxm, .otg, .odg, .uop, .potx, .potm, .pptx, .pptm, .std, .sxd, .pot, .pps, .sti, .sxi, .otp, .odp, .wks, .xltx, .xltm, .xlsx, .xlsm, .xlsb, .slk, .xlw, .xlt, .xlm, .xlc, .dif, .stc, .sxc, .ots, .ods, .hwp, .dotm, .dotx, .docm, .docx, .DOT, .max, .xml, .txt, .CSV, .uot, .RTF, .pdf, .XLS, .PPT, .stw, .sxw, .ott, .odt, .DOC, .pem, .csr, .crt, .key, wallet.dat
However, Locky will not encrypt any files where the full Pathname and Filename contain one of the following strings:
tmp, winnt, Application Data, AppData, Program Files (x86), Program Files, temp, thumbs.db, $Recycle.Bin, System Volume Information, Boot, Windows
Like the CryptoWall ransomware that has been seen in the past year, Locky also changes the names of the encrypted files in order to make it more difficult for victims to restore the correct data. Locky uses the naming format of “[unique_id][identifier].locky” for encrypted files. For example, if Locky assigns the victim a unique name of “A8678FDE2634DB5F” and it encrypts a file like “example.doc”, the file may be renamed something like “A8678FDE2634DB5F0123456789ABCDEF.locky” . In addition to obscuring the original file names, Locky takes the extra step of deleting all Shadow Volume copies on the machine in order to prevent the victim from simply rolling back or restoring their files.
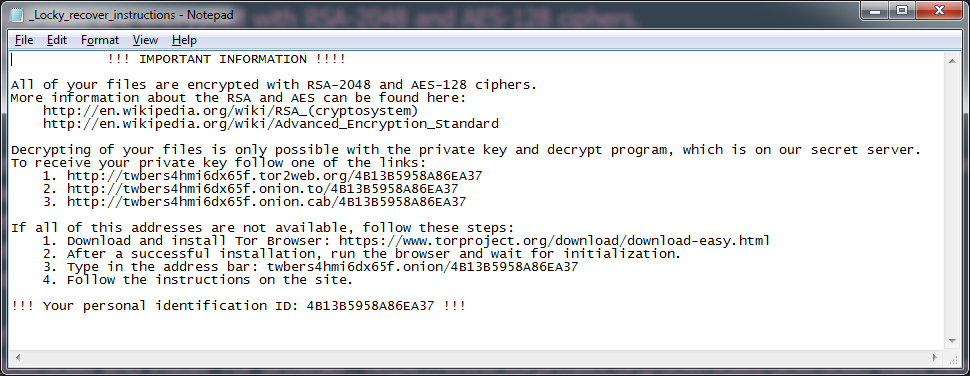
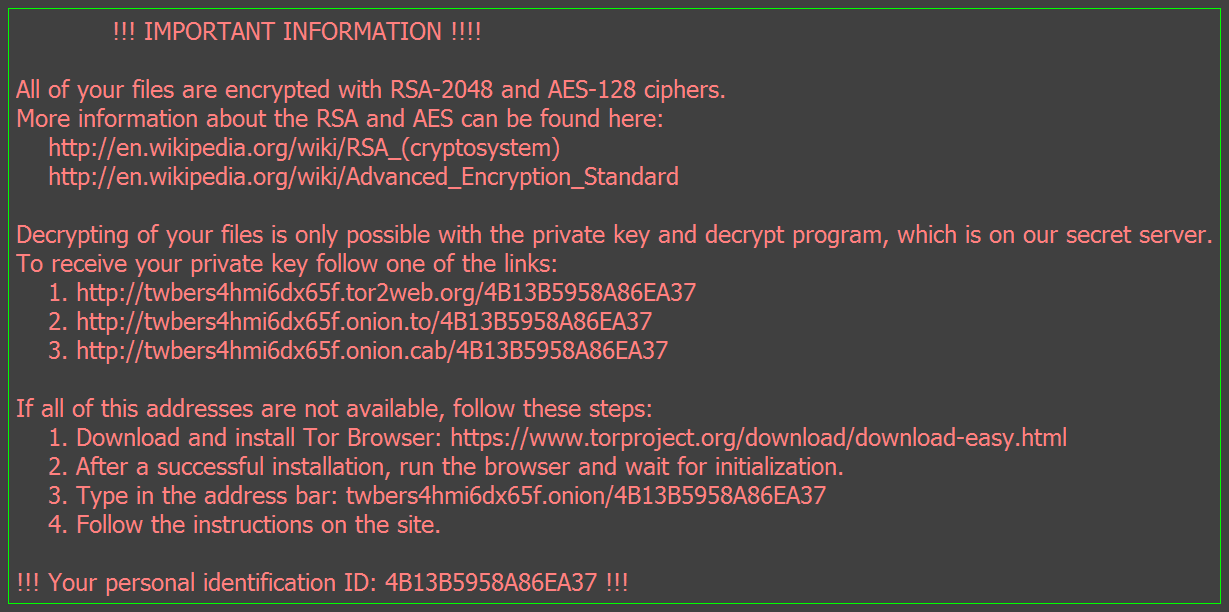
Since the main purpose of Locky is to coerce the victim into paying a ransom to retrieve/decrypt their data, Locky helpfully places recovery instructions in several places on the victim’s drive. Text files named “_Locky_recover_instructions.txt” will be dropped in every folder where files have been encrypted, and the Windows Wallpaper will be changed to “%UserpProfile%\Desktop\_Locky_recover_instructions.bmp”, which contains the same instructions as the text files.
The instructions that Locky provides contain links to a Tor site called the Locky Decrypter Page. The URL for this site is “6dtxgqam4crv6rr6.onion” , and it walks the the victim through the process of paying the ransom and retrieving their data. Details included: the amount of Bitcoins to send as payment, how to purchase Bitcoins, the Bitcoin address to submit payment, and a link to the Decrypter once payment is made.
Text Instructions
Desktop Background Instructions
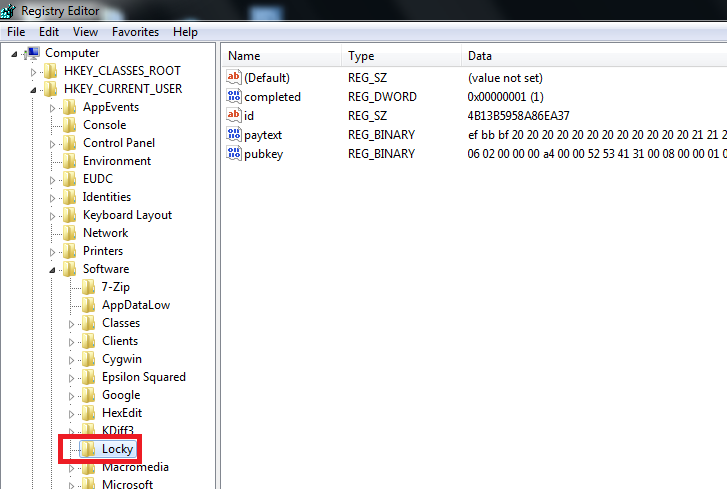
Locky will also store various information in the Windows Registry under these keys:
HKCU\Software\Locky\id – Unique ID assigned to the victim
HKCU\Software\Locky\pubkey – RSA Public Key
HKCU\Software\Locky\paytext – Ransom Note Text
HKCU\Software\Locky\completed – Whether or not the ransomware finished encrypting all available files
HKCU\Control Panel\Desktop\Wallpaper (“%UserProfile%\Desktop\_Locky_recover_instructions.bmp”)
Because the Locky ransomware can encrypt all network drives, it is critically important to lock down the permissions on any available network shares. As always, it is also important to perform regularly scheduled backups of all important data, and to have the backup drive stored off-network when not in use. At this time, there is no known way to decrypt files encrypted by Locky (unless ransom is paid), and its deletion of the Shadow Volume copies makes this even harder to circumvent. It has been reported that Locky victims have been successful in retrieving their data after payment is made, but it is never advisable to pay cyber-criminals their requested ransom. With due diligence and good security habits, everyone should be able to avoid being infected by Locky.







Does webroot protect against Locky?
Tom,
Yes we protect against this ransomware. If we compose a blog about a threat we have already reviewed it and created rules to protect our customers from it.
but i have webroot and i just turned the reception pc on and it is infected.
Craig, any issues involving threats need to be addressed by our Technical Support Team directly. Please feel free to reach out to them at your own convenience.
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send us a Support Ticket: https://detail.webrootanywhere.com/servicewelcome.asp
Warm Regards,
Josh P.
Webroot Community Support
I just purchased webroot (thought it would remove the loky files) but it did not removed the locky files. what can I do
Chances are that any active infection associated to the Locky Ransomware infection has already been removed. This does not mean we can unencrypt your files. The strongest way to prevent against any type of Ransomware Infection is to Always have Backups.
https://community.webroot.com/t5/Webroot-SecureAnywhere-Antivirus/How-does-Webroot-stop-ransomware/td-p/256844
Team, I had a recent infection on my clients site. It spread through map drives and encrypted shares and subsequent folders/files. Is there a reason why the server side protection did not detect the encryption process? Is there a way to ensure when this happens that WR can detect and quarantine?
Michael, any infection-related inquiries should be handled by our Support Team directly:
Business Technical Support: Call 1-866-254-8400
Open a Support Ticket: http://mysupport.webrootanywhere.com/supportwelcome.aspx?SOURCE=ENTERPRISEWSA
They can address any concerns and also any your question about the Threat you experienced.
Warm Regards,
Josh P.
Social Media Coordinator
Just install an Anti-Malware like MalwareFox to remove the ransomware and a data restoration program to restore your files, it’s not so hard is it?
I delight in the details on your web sites. Thanks a ton!