 A payload file installed along with some variants of the rogue Internet Security 2010 “antivirus” program modifies victims’ networking settings within Windows, inserting itself into the network stack and preventing victims from visiting some of the Web’s most popular Web sites. More than 40 sites have been targeted, including: Microsoft’s live.com and Bing search engine; social networking giants Facebook, Twitter, MySpace, Bebo, LinkedIn, and YouTube; news organizations including Fox News, The New York Times, the Washington Post, and the UK’s Guardian and BBC news sites; and blogs hosted by blogger.com, livejournal.com, and wordpress.com.
A payload file installed along with some variants of the rogue Internet Security 2010 “antivirus” program modifies victims’ networking settings within Windows, inserting itself into the network stack and preventing victims from visiting some of the Web’s most popular Web sites. More than 40 sites have been targeted, including: Microsoft’s live.com and Bing search engine; social networking giants Facebook, Twitter, MySpace, Bebo, LinkedIn, and YouTube; news organizations including Fox News, The New York Times, the Washington Post, and the UK’s Guardian and BBC news sites; and blogs hosted by blogger.com, livejournal.com, and wordpress.com.
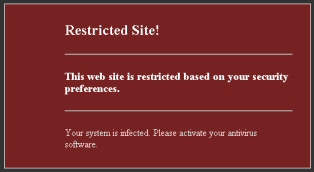
The payload modifies the Layered Service Provider (LSP) so that calls to those Web sites pass through the malicious file, which displays a warning message in the browser instead of the blocked Web site. The message says:
This web site is restricted based on your security preferences
and
Your system is infected. Please activate your antivirus software.
We’ve seen an increase in the number of spies that bollix the LSP chain lately. In cases where this happens, if you simply remove the malicious file that is referenced in the LSP, the computer remains unable to connect to the Internet afterwards. To fully repair the PC, you’ll need to fix that broken chain.
Fortunately, the fix for this spy — which we’re calling Trojan-Annoyinator — is fairly easy. Users of Webroot’s products can simply sweep, and the spy along with its LSP modifications will be removed upon reboot. If you don’t have one of Webroot’s antimalware product installed, you can go through the process manually, which isn’t difficult for someone familiar with Windows tools such as Regedit. The only problem might be getting to Microsoft’s Web site (where the instructions are posted) from an infected computer.
The spy only injects itself into a short list of Internet-capable applications; unfortunately, that list includes every popular browser for Windows: Internet Explorer, Firefox, Opera, Chrome, Safari, and the Flock browser (which runs Firefox as its core engine). In addition to the sites listed above, it also blocks some file-sharing sites (The Pirate Bay, RapidShare), shopping sites (Amazon.com, Craigslist), some porn sites, and a few oddballs, like MapQuest, Monster.com and Wikipedia.
Notably, the spy doesn’t block access to the Web sites of legitimate antivirus companies or other businesses in the computer security industry. Malicious hosts files and IFEO registry keys that disable legitimate security applications become almost a de-facto part of the infection package (especially with Chinese phishing Trojans). But not with this one.
Fixing the LSP chain manually on a Windows XP computer is a relatively straightforward process. If you don’t want to use a freeware tool such as LSP-fix, you have to delete a few registry traces, then reinstall Windows’ TCP/IP protocol over the top of itself; this forces Windows to rebuild the LSP chain from scratch. After a reboot you should be up and running again, as long as the malicious files have been removed from the computer.
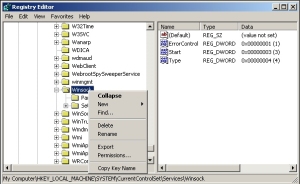
Manual LSP repair instructions
- Click Start, choose Run…, type Regedit in the dialog, then click OK. In the left pane of Regedit, navigate to:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesWinsock
- Right-click the item labeled Winsock in the left pane, and choose Delete, then Yes in the Confirm Key Delete dialog box.
- Repeat the same steps with the item labeled Winsock2, also in the left pane, directly beneath Winsock.
- Close the Regedit program. Next, open the Network Connections control panel (click Start -> Settings -> Control Panel -> Network Connections), then right-click Local Area Connection and choose Properties.
- Click the button labeled “Install…” then select “Protocol” and “Add…”
- In the Select Network Protocol dialog, click the Have Disk… button.
- Type “C:Windowsinf” into the field labeled Copy manufacturer’s files from: and click OK.
- In the Select Network Protocol dialog, select the Internet Protocol (TCP/IP) item and click OK.
After a reboot, Windows will rebuild your LSP and (unless you need to modify any custom TCP/IP settings for your particular setup) you should be able to connect to the Internet.
























Yeah… Have had this crap on my puter as well as my wife’s. Webroot handled mine. Malkwarebytes handled my wifes. They should find and put these bastards in jail
Are you aware of the program? It looked so official being tied into the Microsoft Firewall. The Norton Antivirus program said there were no trojans and malware during this episode. And yes, the installed Norton program was the only thing that would work.
This site locked itself onto the other computer here at home, and held us hostage (so to speak). We could not stop the repeated pop up alerts for this program that linked itself to our Microsoft firewall and kept saying we had malware and trojans and needed to purchase the registration key code to fix these critical threats to our files and internet activities.
We tried ignoring, no such thing. Accepting the notices required purchasing the product for $69.95 or $89.95 for added protection. We could not stop with that, it would not allow any activity on the computer, ie: internet access, file access, system restore, only shut down, start up and purchase of the product. I managed to get an email notice to the support center on their help link. Then I went to view this on my other computer to read the response from the Help link. They sent instructions to uninstall the program, this appeared to remove it, but it continued to send the notices. We performed a System Restore before it locked into the system again. So far, internet access is back to normal with no more notices for the “Personal Security” program.
You saved my butt. Thank you so much. I was SO frustrated! A million times thanks!
Thanks a lot !!!!!!!!!!
Thanks Man!!! YOU SAVE MY LIFE AND MY BROWSER!!! THANX 1000 Times!
Thanks for that. I hope I won’t need it but it’s good to have.