 Pretty much since it arrived on the malware scene, Koobface has used the technique of sending messages with Web links — in your name, to your friends — as a method of propagating the infection to others. Using your name is a powerful social engineering trick, and the makers of the worm have tried innumerable ways to mask the danger behind those dangerous links: They’ve used “short link” services like Bit.ly to hide the destination; They build pages on sites normally considered safe, like Blogspot or Google Reader, that simply redirect users to a dangerous page; and they use stolen credentials for the Web servers of legitimate businesses to upload their own malicious content there.
Pretty much since it arrived on the malware scene, Koobface has used the technique of sending messages with Web links — in your name, to your friends — as a method of propagating the infection to others. Using your name is a powerful social engineering trick, and the makers of the worm have tried innumerable ways to mask the danger behind those dangerous links: They’ve used “short link” services like Bit.ly to hide the destination; They build pages on sites normally considered safe, like Blogspot or Google Reader, that simply redirect users to a dangerous page; and they use stolen credentials for the Web servers of legitimate businesses to upload their own malicious content there.
Since February, Koobface has tried another technique: It has used different URL encoding schemes, which many browsers but few humans can interpret. You click an odd-looking link and before you know it, you’re on a site that’s trying to push an infection at your PC.
This “new” trick actually harkens back to 2001, when spammers were using so-called dotless IP address tricks to bypass security features in Internet Explorer. A Windows patch issued in October of that year fixed the bug in IE that gave dotless IP addresses additional security permissions. But the IE, Firefox, and other browsers remain capable of taking a URL in the form of (for example) http://1078900434 and correctly translating to a standard IP address, then loading, the page hosted at the IP address that number represents. (The dotless link above will take you to Webroot’s Web site.)
Dotless IPs are so easy, it’s hard to believe that malware authors haven’t been using it all along. I’m sure we’ll see more of this in the future. Not only is it incredibly simple to obfuscate the destination IP address this way, but you can make additional dotless IPs that point to the same location simply by adding multiples of the number 4294967296 (256 raised to the fourth power) to an existing dotless IP address. (Using the example above, the address http://5373867730 also would take you to Webroot’s front page.)
Similarly, the IP address that points to a Web server can be represented in other formats, such as the base-16 hexadecimal, or base-8 octal formats. These are even easier to do, because there’s no addition or multiplication involved. Each of the four numbers in an (IPv4) IP address can be converted to either “hex” or “oct” using the Windows calculator in Scientific mode.
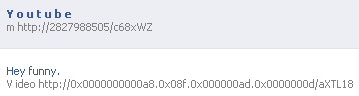
In hexadecimal form, the URLs always have to begin with http://0x (that’s zero-x) — that’s the giveaway. You simply convert each number in the IP address to its hexadecimal equivalent (decimal 64 — the first number in www.webroot.com’s IP address — is “40” in hex, decimal 78 is “4E,” and so on) then run them all together, like http://0x404eb6d2. You can also represent each set of numbers individually with dots, but you have to begin each set with the “zero x” such as: http://0x40.0x4e.0xb6.0xd2 and you can mix it up, for example by just using a single dot to separate the first number from the rest of them, as in http://0x40.0x4eb6d2 (WordPress won’t let me make a link that looks exactly like this one) or virtually any other combination you can imagine. And each of those hexadecimal representations can be preceded by almost any quantity of leading zeroes, so the address could look like http://0x00000000040.0x0000000004e.0x000000000b6.0x000000000d2 and still take you to the same destination as all the others.
Likewise, with Octal-format IP addresses you can just do the conversion in the calculator. All Octal IP addresses are preceded with at least one leading zero, followed by two or three numbers from zero to seven. For example, decimal 64 is “100” in Octal, decimal 78 is “116,” and so on. The Octal IP URL looks like http://0100.0116.0266.0322 but could also be represented as http://000000100.000116.00000266.0322 or in virtually any combination with any number of leading zeroes.
Now things get really tricky when the bad guys mix up Hex, Octal, and dotless into a single URL. You might see something that looks like http://0x40.0116.0xb6d2 or http://00000000000000000100.0x4eb6d2 — it can get silly just trying to imagine all the possible permutations that the malware goofballs might come up with. Needless to say, there are a lot of them, but they are all readily identified on sight, if you know what to look for.
When you see dotless, Hexadecimal, or Octal IP addresses posted to a social network page — in any format, in any permutation — that is an instant red flag. There’s no good reason for anyone to use a dotless IP address except to hide the destination the URL points to. The use of addresses such as these offer no benefit whatsoever to Web surfers. In the meantime, however, the old adage applies: Look before you click, to which I would add the corollary: don’t click these kinds of addresses.




















Thank you for information. Well job..