 For the past couple of weeks, owners of Web sites have been hit with a wave of attacks that surreptitiously infect unsuspecting visitors with a wide variety of malware types. The first wave inflicted rogue antivirus on unlucky victims, but late last week victims who visited infectious sites were redirected into a drive-by download site that pushes clickers onto a vulnerable visitor’s computer.
For the past couple of weeks, owners of Web sites have been hit with a wave of attacks that surreptitiously infect unsuspecting visitors with a wide variety of malware types. The first wave inflicted rogue antivirus on unlucky victims, but late last week victims who visited infectious sites were redirected into a drive-by download site that pushes clickers onto a vulnerable visitor’s computer.
The affected web sites have been modified to add malicious, obfuscated Javascript code to the footer of each page. Some Web hosts are trying to notify customers or fix the problems. At first, the problem affected sites that run the open-source WordPress publishing system, but the attack has broadened into non-Wordpress (and non-blog) Web sites. The gobbledygook Javascript opens an iframe hosted from a different Web site, and the code that loads inside that iframe redirects the victim’s browser to yet another site, which loads the infection and executes it.
I’m going to name (domain) names in this post, so please, for your own sake, use this information only to block the domains at your gateway or in your Hosts file — don’t go visiting them just to see what happens. I guarantee you won’t like what happens.
In the earlier attacks that began the week of April 5th, the malicious script directed victims to a page hosting the Eleonor exploit kit; The kit uses several well-worn methods to try to push executable malware (typically the Tacticlol downloader, which malware distributors have been using of late to push down rogue antivirus programs) at susceptible browsers, or computers running vulnerable versions of Adobe Acrobat or the Java Runtime Engine.
Those attacks originated from several domains, including corpadsinc.com, mainnetsoll.com, and networkads.net — all of which are hosted on the same IP address in Turkey, and are still live and hosting the exploit page.
 But last week the script began directing users into a page on the domain name yahoo-statistic.com, a site which, despite its name, has nothing at all to do with the giant portal. That page, which loads in an iframe, opens other malicious sites which push the infection.
But last week the script began directing users into a page on the domain name yahoo-statistic.com, a site which, despite its name, has nothing at all to do with the giant portal. That page, which loads in an iframe, opens other malicious sites which push the infection.
The list of affected sites is global, including a newspaper in Florida; the English-language page of a government’s Ministry of Women’s Affairs Web site; the Web site of a Spanish lawyer’s association; and a car dealership Web site in Indonesia. And as of today, visitors to this growing list of Web sites are still getting hit with Trojans.
I’m sure a lawyer for Yahoo would love to have some words with anyone connected to this latest attack, which has been going strong for at least six days now. Unfortunately, the site is hosted in Russia, and it appears to have been put together by the same people who use the name “Hilary Kneber“ to register the Web domains they use for malicious purposes. In February, we and others noticed that the same cadre of goons had been actively spreading the Trojan-Backdoor-Zbot password stealer from Web sites supposedly registered to this same pseudonym.
In the case of our attacker, the infection progresses this way: A victim unwittingly visits a page that has been modified to amend the bad Javascript code. The Javascript redirects the browser to various pages hosted on hnarmettis.com, mnuyetsgrr.com, or nuvolokijj.com. The sites share an IP address assigned to a Latvian hosting provider, and were registered with Russian WHOIS information using BIZCN, a domain registrar based in China.

The sequence of events that the drive-by exploit kit follows always includes a malicious PDF and two malicious Java JAR files.
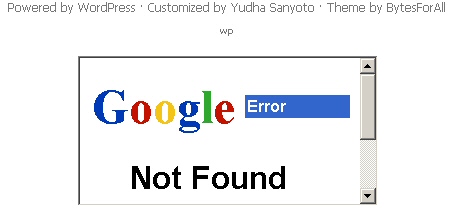
Each of the sites attempt to exploit various security vulnerabilities (one Adobe PDF, two separate Java vulnerabilities, and a hackneyed attack against older versions of Internet Explorer called the MDAC exploit) in order to push malware (shown above as a file called setup.exe) at a visitor. When the infection is complete, the iframe then redirects the page to Google‘s “404” (page not found) page, as shown below.
If one or more exploits are successful, the victim’s machine pulls down the clicker executables and then contacts one of at least three different Web domains: itotolo.com, totoship.com, and iprototo.com, which serve as command-and-control for the clickers. I don’t know why the malware distributor seems to have an obsession with a scruffy mutt from a famous movie, but I don’t need to understand the machinations of an unhinged mind to be able to deal with the consequences of its actions.
Clickers are an odd sort of adware in that they don’t actually display the ads they load on the infected computer. Selling you junk you don’t need is not in the business plan. Instead, a clicker simply loads dozens to hundreds of Web pages per minute silently, in the background, in an attempt to manufacture fraudulent “clicks” on online ads. Criminals can make money for themselves by signing up as advertising affiliates, then using the clickers to drive infected machines to load their pay-per-click ads. Unscrupulous companies also can use clickers to load the ads from a competitor company, which can prematurely expend the victim company’s pay-per-click ad budget.
Initially, the site pushes down a dropper we classify to the definition Trojan-Backdoor-failst0rm (aka Win32.Decay by other vendors), and that dropper delivers the clicker payload, which we call Trojan-Clicker-Dawg. Because the dropper portion of the infection won’t run in a virtual environment, we play with this stuff on real hardware.
There’s good reason to get rid of clickers quickly: They have a nasty habit of “casually” visiting Web sites hosting other drive-by download exploits, which can force even more malware onto an already infected computer. They also consume a tremendous amount of bandwidth in the furtherance of their activities, which can slow to a crawl an infected PC’s ability to surf the Web.
In addition to removing the Trojans, we’re currently blocking these domains in our desktop products (and others registered by the same registrants), and you should do the same.