By Ian Moyse
 A decade on from the ILOVEYOU worm, what has changed—apart from ‘we’re older and (supposedly) wiser?’
A decade on from the ILOVEYOU worm, what has changed—apart from ‘we’re older and (supposedly) wiser?’
We have allowed the bad in the real world to progressively infect our online world, giving criminals a way to attack victims that is more dangerous for the victim and, coincidentally, safer for the attacker. As recently as a decade ago, bank robbers had to physically enter the bank premises and overcome its defenses. Today, they simply need to be clever enough to trick you, rather than break the defenses of the bank itself.
In humanizing the Internet we have dehumanized cybercrime.
The individual computer user was, and remains, the weak link. The concept of social engineering still poses the principal online threat affecting everyone.
At last week’s Infosecurity Europe show in the UK, I spoke about the latest threats, and how they clash with the realities of the Internet and the Web 2.0 world we live in today. Attendees who spoke to me afterward, many of whom provide support and IT services to business of all sizes, told me they live with these threats every day.
I asked the people watching my talk who thinks malware is still as much of a threat as it ever was, and the sea of hands that shot up spoke volumes: Ten years on, we face the same problem on an increasingly large scale. The attackers however have gotten smarter, and more malicious. We have seen more malware in the last 18 months than the last 18 years combined — and the attacks which deliver that malware to victims are equally creative, ingenious, and devious.
End users (and by this I mean the business users, not the IT team) are more computer adept than they were ten years ago, but are they any wiser? I don’t see it. Counterintuitively, you could make a compelling point that the average computer user is more susceptible to malware and scams today on the Internet than they were back then. Users with PCs at work and home, accustomed to the rapid convenience of high speed Internet access and instant communication, have become more trusting, more pliable, to the smart attacker.
Recent spam attacks have included, for example, messages disguised as an antispam quarantine alert; The message prompts the recipient to visit a Web page in order to release an important email, but the Web page simply pushes down a password-stealing keylogger at the victim’s browser. Meanwhile, criminals manipulate the results of the world’s dominant search engines, delivering malicious drive-by downloads posing as news about, for example, recent celebrity deaths. Are Internet users so collectively gullible that a bogus come-on about previously unpublished pictures or videos of Patrick Swayze, Brittany Murphy, Farrah Fawcett, Corey Haim, or Michael Jackson serves merely as the click-through carrot that leads to an infection? Apparently, yes, and victims flock to these traps in droves.
Interacting with other people and with businesses over the Web is a part of many people’s everyday lives, whether it’s through social networking sites, Web mail, online travel booking, shopping brick-and-mortar retailers through a Web interface, or banking online. Users have been trained to feel comfortable in this new brave world. It used to be true that, before you could get mugged, you at least needed to venture out. The Web has changed all that. You can be robbed whilst sitting in your own living room. You can be conned from the comfort of your kitchen.
At the office, the problem is just as bad. Small business needs protection from the same threats that target large organizations. An individual in a company with 20 employees is under just as much threat (if not more) as one person in a company with 20,000 employees. After all, attackers simply see their victims as just another email address or IP address, and rarely target a specific person. But it can be a daunting challenge for a smaller company with fewer resources and less security expertise to offer the same high level of Internet security that a large enterprise demands. The problem now is, how do you harden this community to attack; When online commerce is built on a foundation of trust, sewing the seeds of distrust could destroy that foundation.
This is a prime area where SaaS (Software as a Service) security can step in and not only protect against spyware, viruses, phishing, spam, and Web based threats, but also give the highest level of protection at utility based pricing, allowing a small business to get the best security at a price appropriate to their size.
With the increased volume, complexity, and sophistication of attacks, SaaS security is the easiest and most cost effective solution to the majority of business needs for internet protection today and into the future. Certainly the high level of interest we saw at Infosec validate that the time has come for business to move their network security out into the cloud, where the threats reside.



















Just read The Lessons of a ‘Love Bug’ Still Ring True, By Ian Moyse.
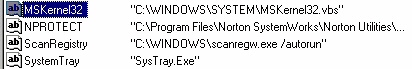
In your example copy & paste, you highlighted “Kernel32” Is this a worm or virus?? I did a search & have a ton of items with this name. Some are photos, some program files/wild tangent/components, and some say Kernel32.dll.
Now I’m worried.
No, the file kernel32.dll is not malicious, but the msKernel32.vbs entry in the registry (shown above) is the Loveletter malware. Kernel32.dll is part of the Windows operating system. You can right click the file and check its digital signature if you’re not sure.
Mr. Moyse’s points are spot-on here–SaaS and cloud services, particularly security, are coming, and I think it’s about time we embrace it. One provider I work
withfor, [company name removed by editor], is already an expert in security systems, and had the bright idea to start providing its whole line, in addition to physical products, as SaaS and cloud services. As a market analyst, I believe this is the current direction of enterprise computing, and the sooner we accept it, the better for us and for the fast development of secure cloud services. Oh yes, and I forgot to mention I’m the worst sockpuppet ever.