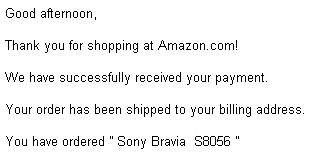
 An ongoing campaign where malware distributors use email spam to deliver dangerous programs to unwitting victims has begun to change its tune, switching the scam to incorporate different brands. In the latest scam, the message appears to be an order confirmation from Amazon.com for the purchase of an expensive consumer electronics item, or a contract (spelled, tellingly, “conract“) for expensive home improvement work, purportedly to be done on the recipient’s home.
An ongoing campaign where malware distributors use email spam to deliver dangerous programs to unwitting victims has begun to change its tune, switching the scam to incorporate different brands. In the latest scam, the message appears to be an order confirmation from Amazon.com for the purchase of an expensive consumer electronics item, or a contract (spelled, tellingly, “conract“) for expensive home improvement work, purportedly to be done on the recipient’s home.
A few weeks ago, the emails switched from a “shipping confirmation” hook to one which claims the contents of the attachment include a code worth $50 on Apple’s iTunes online store.
The spam messages for several months have included a .Zip compressed attachment. The file inside the .Zip, which looks like a Microsoft Word document, is a malicious program we classify to the definition Trojan-Downloader-Tacticlol.
An extremely dangerous downloader, the Web sites and domains from which Tacticlol (aka Oficla or Sasfis) retrieves its payloads have been remaining online longer than normal. Typically the download site is shut down within a few days, effectively neutralizing the downloader and preventing it from retrieving anything. Recent variants, however, have use Web domains that remain online for weeks or even months.
Malicious sites that remain active only increase the danger that someone who inadvertently opens the attachment a few weeks after the message arrives will still infect their computer.
In addition, the payloads delivered by the download site Tacticlol contacts are being rotated as the days go on. In the initial infection period, within about 36 hours after the spam messages arrive, the download sites deliver a number of different payloads, including the Trojan-Backdoor-Zbot keylogger, the Trojan-Pushu (aka Pushdo) spam bot, and rogue antivirus installers. After a week, the payloads switch to the installers for botnets, which zombify the infected machines and turn them into longer-term hacker workhorses. Recent payloads have included a “dead man switch” which can render the infected computer unbootable.
I’ll discuss the ramifications of opening attachments such as these in an upcoming blog post. Nevertheless, it should be second nature that you avoid opening any attachment that arrives through email unless you can confirm — by telephone, or some other method — that the attached document is legitimate and was deliberately sent to you. Also, train yourself to avoid opening any attachment with an .exe file extension, regardless of its appearance or origin.



















Amazon.com, my favourite shopping place O(∩_∩)O~
I’m getting these emails but now there are no attachment, there are hyperlinks that are taking me to a site with a virus.
Please send a note to the blog [at] webroot [dot] com email address with any links you get. We’d be happy to add detection for them if they’re doing bad things. Thanks.
my co-worker received the fake amazon confirmation today. on mouse-over, looks like destination links go to:
tcecnupk.info and the sender is:
(deleted -ed.)