PC gamers have a new threat to contend with, one that has your personal information in its crosshairs and you can’t dispatch with a sniper rifle or BFG9000: A Trojan designed to steal game passwords that uses Microsoft’s own graphics engine, DirectX, against you.
PC gamers have a new threat to contend with, one that has your personal information in its crosshairs and you can’t dispatch with a sniper rifle or BFG9000: A Trojan designed to steal game passwords that uses Microsoft’s own graphics engine, DirectX, against you.
The Trojan, which appears to have originated in China, modifies one or more of the DirectX driver files — such as DirectSound, Direct3D, or DirectDraw — so it only loads when Windows fires up the modified DirectX driver. Because DirectX is typically used by games, it means this sleeper cell Trojan activates when you fire up a PC game, then terminates when you stop playing. As a result of using this unusual load point to start itself up, instead of a more typical Run key or Services entry in the Windows Registry, the Trojan is unusually low key.
In our tests, the installer drops one or more randomly named DLLs (the keylogger component) in the c:windowssystem directory, then modifies one or more DirectX files. Each modified DirectX file is used to load one keylogger payload, so if the installer happens to drop four keyloggers, it will also modify four DirectX files. It also adds instructions that call functions from another, unmodified, legitimate system file named mscat32.dll. MSCAT32 is completely benign: Windows uses mscat32.dll to create Microsoft Cabinet .cab files, which are similar to .zip archive files. We’ve named this aide-du-vol Trojan-PWS-Cashcab (though some of our competitors call it Kykymber).
As a result of the modifications, the keylogger component loads whenever any program initializes the modified DirectX driver file. Fortunately, it also loads when you run the DirectX Diagnostics program included with DirectX, DxDiag (click Start, Run, then type dxdiag and click OK to start it up). That’s also the easiest way to determine if your PC is infected.
It appears the Trojan steals not only keystrokes but also takes screenshots of whatever happens to be on the player’s screen at the time the Trojan activates, packages everything up as a .cab, then submits the collection to a server. Strings within the Cashcab keylogger indicate it targets a range of popular MMO titles, including Blizzard’s World of Warcraft and NCSoft’s Aion.
The Cashcab installer appends less than 2000 bytes of malicious code to the DirectX files, which it replaces in both the system32 and dllcache folders, which prevents the System File Checker from replacing the modified version with a clean file. It also, helpfully, keeps copies of the original, unmodified file in both those locations, appending a .bak extension to the filename.
Removing the Trojan is a piece of cake, but even without any antivirus program on your computer anyone can effectively identify if their computer has been affected, and neutralize the threat. DxDiag (from version 9 onward) can check the digital signature of all DirectX drivers and rapidly identifies any component files that have been modified. When you run the DxDiag tool, fill in the little checkbox at the bottom.
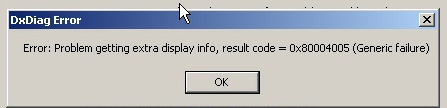
If any of the digital sigs don’t match up, simply reinstalling the latest version of DirectX over the top of any existing installation will restore the modified driver file(s) to their unmolested forms, which prevents the keylogger from activating even if its files are present on the system. DxDiag also, sometimes, reports errors when DirectX files have been modified in this way.
The aftermath of a game phishing attempt is typically that a victimized player logs into the game only to discover that his or her character, dressed only in skivvies, is penniless and weaponless. Criminals use the stolen credentials to loot the player’s character of valuable items or in-game currency, passing it along to an accomplice who then fences the stolen goods on various “Buy Gold Cheap” Web sites. So, yes, it’s all about the money.
Because the grey market for buying gold/credits/ducats not only supports these criminals but motivates the creation of new tools for theft, gamers need to stop buying game-gold on the Web: Keeping the grey market alive just feeds the problem. Just stop now. Please.
Tip of the white hat to Threat Research Analyst Travis Newton for his assistance.