A spammed link campaign that spread through Facebook rapidly over the weekend delivered a malicious payload designed to take control of the Facebook account of any infected user, steal passwords, and hijack clicks in the victim’s browser. The messages appear as links sent by a friend, accompanied by the brain-damaged text “You? I find it on Google.”
A spammed link campaign that spread through Facebook rapidly over the weekend delivered a malicious payload designed to take control of the Facebook account of any infected user, steal passwords, and hijack clicks in the victim’s browser. The messages appear as links sent by a friend, accompanied by the brain-damaged text “You? I find it on Google.”
Clicking the link directs recipients to a page on online-photo-albums.org which, at the time, pointed to malware hosted on a server (now offline) based in Bosnia and Herzegovina.
This installer drops no fewer than six payloads, including the “clickjacker” Trojan-Bamital, which redirects the browser to a different site when a user on an infected machine clicks a linked result in a very specific subset of search engine Web sites (such as, for example, results on the South Korean version of Google, Google.kr, but not the main Google.com site itself).
In addition, album.exe file also drops Trojan-Downloader-Suurch, which can download and install additional payloads, and leads hapless Web surfers into the abyss by hijacking searches on a broader set of search engines, and injecting its own code into the search results page. The album.exe installer also drops a DLL which captures passwords and other data entered into Web forms in Internet Explorer, and forwards that data on to a different Web domain (which happens to be hosted at the same IP address in Bosnia that was used for the album.exe download — and remains online as I publish this).
The link points to a URL in the form of online-photo-albums.org/Firstname_Lastname (with the first and last name of the recipient plugged into the link). That page features a number of photos of what appear to be the variety of bored models with stupefied, drug-addled expressions on their faces that are always packaged in new picture frames. A link in the center of the page, customized with the victim’s name, leads to a malware installer named Album.exe.
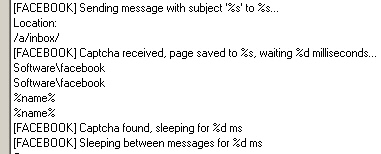
In addition, the component which captures data in Internet Explorer also hijacks any Facebook account previously accessed on the infected system to spread itself, very much in the style of Koobface, but without any of the other characteristics of a Koobface infection. I suppose it makes sense that the domain used in this attack is named spmfb3309.com (as in spam facebook, get it?), and the IP address was also used to host the previously-seen spmfb2299.com, which shares a similar reputation for shenanigans the newer domain appears to exhibit.
Once again, this highlights the need for anyone who uses a social network to be extremely careful about clicking random links, especially when those links appear to come from someone you know. Just because a URL gets posted on Facebook doesn’t confer to it some sort of magical protective ability.
Most of the payloads remain undetected by competitor AV engines at the time we did the research. The album.exe installer and all of its dropped payloads will be detected in the next release of our definitions.