 Yesterday, a few of the Threat Research folks and I had a little fun playing with a hack that had, for one day at least, pretty much decimated Google’s Image Search feature. One researcher, who stumbled into the attack purely by chance, found that a Google Images link to a map of the United States was, instead, redirecting hapless Web surfers to pages that deliver an installer of a rogue antivirus in the Security Tool family of fine, fraudulent products.
Yesterday, a few of the Threat Research folks and I had a little fun playing with a hack that had, for one day at least, pretty much decimated Google’s Image Search feature. One researcher, who stumbled into the attack purely by chance, found that a Google Images link to a map of the United States was, instead, redirecting hapless Web surfers to pages that deliver an installer of a rogue antivirus in the Security Tool family of fine, fraudulent products.
What really caught our interest was how the hack behaved, depending on the operating system and browser you used. With each different browser configuration, we were treated to one of several different, specially crafted malware delivery Web pages.
I’m not sure when the attack started, but we started analyzing it at around 10am, Mountain time. By late afternoon, the sites were offline and the attack no longer worked.
To test the extent of the hack, we played around with the manipulated search results using five different browsers: Internet Explorer 6 and 8, Safari 5, Google Chrome, and Firefox. All the browsers were set up with default settings in an otherwise identical installation of Windows XP SP3. We then searched for USA Map and clicked the second result that appeared under the header “Images for usa map.” (All but the first image result that appeared on that first page of results linked to the malicious Web site.)
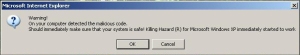
With Internet Explorer (both version 6 and 8), clicking the map image immediately caused the browser window to close, and a dialog box to appear. The text of the dialog read:
Warning!
On your computer detected the malicious code.
Should immediately make sure that your system is safe! Killing Hazard(R) for Microsoft Windows XP immediately started to work
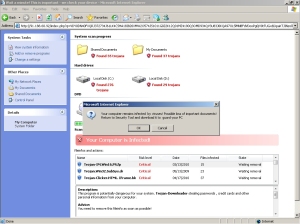
Clicking “OK” leads to your common, typical Javascript fakealert. A browser window opens, and what appears to be some sort of virus scan (but is really just a sophisticated animation) runs. Another dialog composed mainly of hilariously bad grammar warns the user about “Possible loss of important documents!” then prompts you to download the bogus removal tool (filename: inst.exe) when it is finished.
Yeah, yeah, seen it before, yadda yadda yadda. Unintentional bad-grammar humor even extends to the browser title bar, which reads “Wait a minute! This is important – we check your device” like a waitress who’s chasing you out the door when you run out on the check. Funny, but not technically interesting in the slightest.
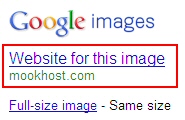
Using Internet Explorer 8, however we were led to an interstitial page on Google which previews the image. Note, however, that the “imgurl” value in the Address Bar shows the source image as coming from www.qsl.net but Google Images reports that the “Website for this image” is mookhost.com — the domain where the page that performs the redirection was hosted.
One would assume that an organization as sophisticated Google would actually be able to tell that the image was hosted at the “imgurl” domain, but I suppose that’s the secret sauce behind the trickery the blackhat SEO goofballs employed.
When you click the same malicious link in Google using Firefox, for example, you’re led to a page that looks like this.
Oddly enough, the page (hosted at update-ff.co.cc) loads both the stylesheet and images from Mozilla’s own Web server, but replaces the content in the center of the screen with an orange box that reads:
You should update Adobe Flash Player right now.
Firefox is up to date, but your current version of Flash Player can cause security and stability issues. Please install the free update as soon as possible.
Of course, both of the linked blobs of text lead to an installer (which, despite claims that it was supposed to be an Adobe Flash update, called itself ff-update.exe). If you don’t click anything, a countdown timer eventually elapses and starts a download of the same installer. Each time we refreshed the page and downloaded the file we received a copy that was the same size but had a unique MD5 hash. That means, something on the server was randomizing each file as it was delivered to the machine.
OK, this was getting a little more interesting. Server-side randomization isn’t exactly new, but it’s not commonly seen with rogues; Distributors of rogues don’t usually go to all the trouble to set up their Web servers with the ability to randomize the payload file because the sites don’t usually remain online for very long anyway. Hash randomization is just one technique the bad guys use to thwart detection by real antivirus products.
How could you know this was a fake page, other than the fact that visitors didn’t actually update Firefox in the course of our little test? Check out that version number in the screenshot of the Web page. Version 3.6.7 is one version lower than the newest version (3.6.8 went live this past July 23rd), but that isn’t the version of Firefox I had running. My testbed has Firefox 2.0 on it. D’oh!
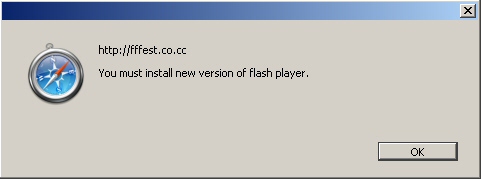
The version of the manipulated page that was customized for Safari was hosted on fffest.co.cc. It pops up a dialog box which reads, simply, “You must install new version of flash player” without any punctuation, capitalization, or use of the definite article.
Oddly enough, the page itself puts an Internet Explorer-like message at the top of the screen which says “You need to install media components. ActiveX: “Adobe Flash Player” from “Adobe Systems Incorporated.” Oops. I guess nobody told them that Safari doesn’t use ActiveX.
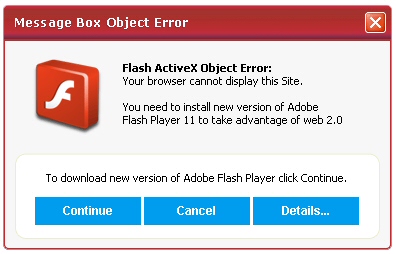
And in Chrome, you get a page that looks almost identical to the Safari page, but instead of a Safari popup, the page displays a graphic that says “Flash ActiveX Object Error” and then prompts you to “install new version of Adobe Flash Player 11 to take advantage of web 2.0.”
Awesome. So, let me get this straight: On Chrome, which also doesn’t use ActiveX as its plug-in architecture, I need the ActiveX version of a nonexistent, future version of Flash in order to view the page? These malware geniuses need to get out of their time machine and look around a bit.
By the way, here is what a real Adobe Flash update dialog looks like. If you are running an older version of Flash, Adobe started pushing out these update notices in June. Can you spot the differences between this one and the others?
Besides the fact that it gives you a lot more information, there’s the little matter of that button labeled Don’t Install. You’ll never find that on a malicious Flash Update dialog.
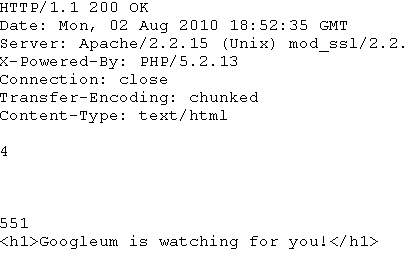
The final piece of our research involved fiddling around with the Web domain to which all these manipulated search results link. After sending a few dozen queries at the server, I started to see this in the result window:
Wow, really? It’s watching for little old me? Not knowing what “Googleum” is supposed to be, I (naturally) Googled it, and here’s what appeared:
Let’s see: “Black SEO Empire” – check. Russian language Web site – check. Domain name ends in .biz – check. Yeah, sounds about right.
We’ll be watching out for you, too, qui no sabe.
























I saw this threat on my Macbook Pro, using Firefox. I was visiting a site I’ve visited before (Freddie Speaks Up), it’s a blog, and that “Wait a Minute” page popped up instead. I just used the BACK button and then ran my iAntiVirus.
Nothing was found and my iAntiVirus was up to date.
Is this “Wait A Minute” bogus security webpage dangerous if I saw it on my Mac? I didn’t stay on the page more than 5 seconds and certainly didn’t download anything.
Thanks!
Mike
Do you mean Frederik Ljungberg’s blog? I haven’t seen the same behavior, but clearly, any legitimate Web site could become compromised, modified to issue redirection commands to your browser. Hate to sound like a broken record, but this is why I use the NoScript plug-in (www.noscript.net) for Firefox, which can prevent virtually all of these kinds of attacks, on any platform that can run Firefox.
Can you get this on a Mac? I’m running Snow Leopard and saw this phony web security page visiting a blog I normally read.
I just canceled the program and pushed the back button to go to my previous page.
I have an up to date version of iAnitVirus and it didn’t find anything.
Could it be that the blog webpage had a problem? I visited it today and saw no problem.
Thanks
I haven’t seen Mac-specific downloads, so it’s likely that you just stumbled into a not-too-smart malicious scripting attack.
I use Firefox 3.6.8 and just downloaded NoScript Sunday night. Works well.
I had a feeling the issue was script re-direct hitting Freddie’s site and not a real issue with my Macbook Pro.
I’m liking NoScript, but after a couple days of reading about Mac security/antivirus/malware threats that are sure to come I went ahead and purchased VirusBarrier X6 from Amazon.com this week.
Given that Macs are becoming more popular every year, it’s seems it’s a matter of time when the virus bug will arrive, so best to be safe.
Thanks Andrew!
Mike G
Thanks so much for the info. I was led here by a google search on the same ‘error’ message but moments ago. Glad I found you guys. =0)
I have windows XP and I am experiencing the same problem. The virus continously redirects my computer to various pages when I try to search anything and the killing hazard malicious code messege keeps popping up. How can I fix it?
You need to use an antivirus product to remove this rogue. In the meantime, you can clear your Temp folder; That may get rid of some of the downloaded components.
Glad you enjoy it and thank you so much for your great feedback, we really appreciate it! 🙂
Hello,
The threat blog seems to load just fine when I pulled this post up on my iPhone, so I’m not sure why it looks weird for you on your device.
I would suggest trying to load it in our SecureWeb Browser for your iPhone first:
https://itunes.apple.com/us/app/webroot-secureweb-browser/id460986853?mt=8
Please let us know if you are still having issues.
Regards,
Josh P.
Webroot Community Support
Thanks for all of your feedback! Glad you enjoy the information ?
If you would like to further participate with us, please join our Webroot Community where you can find solutions to all different kinds of problems and maybe even be able to help someone else yourself! We’d love to have you join.
https://community.webroot.com/
Warm Regards,
Josh P.
Webroot Community Support