 Dear Customers: Please be aware that a crew of Russian malware distributors are circulating a spam message which looks like a subscription renewal confirmation from Best Buy, allegedly for one of our products.
Dear Customers: Please be aware that a crew of Russian malware distributors are circulating a spam message which looks like a subscription renewal confirmation from Best Buy, allegedly for one of our products.
The linked text in the message, however, leads to a Web site which performs a drive-by download. Please don’t click the links in the message; If you have any questions about your subscription, please contact support.
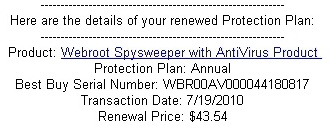
The spammers appear to have done some homework. Some, but not enough. Best Buy currently sells our products through their online software subscription service. Note to spammers: If you’re going to try to hijack our trademark, the least you could do is get the name right. Best Buy doesn’t sell anything called Webroot Spysweeper with Antivirus Product. Nor do we.
The email message claims it is a notice that your subscription has been renewed, and includes a serial number (which doesn’t work) and a transaction date of July 17.
The link in the message leads to the Web site of a small bed and breakfast in New Zealand, which has been compromised. We’ve informed the owners of that Web site of the spam campaign and asked them to take down the page referenced in the spam message.
I guess we struck a nerve, hurt some sensitive malware author’s pwetty widdle feewings, and ended up a target for attack, one that falls down. Too bad, so sad.
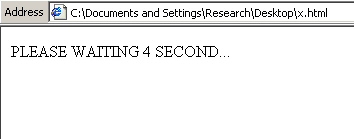
If you were to click a link, you’d end up seeing a page that looks like this one.
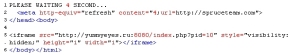
The page attempts to do two things: It loads a script that originates from the yummyeyes.ru domain, and it also forces the browser to open one of those fake Canadian Pharmacy pill-vendor pages, hosted on spruceteam.com.
The yummyeyes script is doing some bad stuff, although for the moment it appears not to be working. It attempts to exploit various vulnerabilities, targeting the Java VM and Adobe Reader. The page pushes down a lot of obfuscated Javascript, as well as a malicious PDF and another page which tries to get Java to load an applet that isn’t present on the server.
The Javascript, once deobfuscated, reveals how goofy the attackers are. They set a variable with the value of “3.13.37” — seriously.
While we must admit that this is ever so ‘l33t, it also invokes an ID-10T error, chumps.
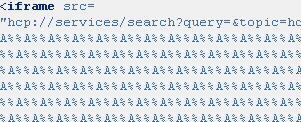
We also saw this oddball use of the “hcp://” protocol vulnerability. It’s not much to look at in its raw state:
But the lower part of the script cleans up nicely, once you chop out all the double-hex-encoded punctuation marks. Oh, and what’s that embedded in the script? A URL that’s been mirror-flipped so it’s backwards?
Nobody would have ever spotted that one, pointing to blockoctopus.ru in a million years. And by nobody, I mean everybody. Just another example of elite coding skills wasted on halfwitted attempts at crime.
We’re in the process of retrieving samples, which appear to be your typical rogue antivirus product. Our next definition update will block the domains involved in the attack and their payloads.




















fuck you
Haters gotta hate.