 A novel and pretty sneaky Trojan designed to steal financial data appeared on our radar screen last week. The Trojan, once installed on a victim’s computer, rootkits itself to prevent detection, then watches the victim’s browser for any attempt to connect to the secured, HTTPS login page of several online banks. When the victim visits the login page the Trojan has been waiting for, the Trojan generates a form that “hovers” over the login page asking for additional verification information.
A novel and pretty sneaky Trojan designed to steal financial data appeared on our radar screen last week. The Trojan, once installed on a victim’s computer, rootkits itself to prevent detection, then watches the victim’s browser for any attempt to connect to the secured, HTTPS login page of several online banks. When the victim visits the login page the Trojan has been waiting for, the Trojan generates a form that “hovers” over the login page asking for additional verification information.
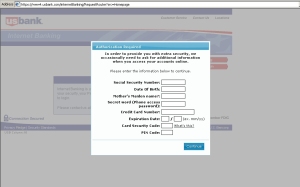
“In order to provide you with extra security, we occasionally need to ask for additional information when you access your accounts online,” reads the popup window. Everybody needs extra security, right?
Of course, the additional information that the bank appears to be asking for is all information the bank already should have if you have an account there: The number on your credit and debit cards; a Social Security number; your date of birth and mother’s maiden name; The PIN code for your debit card and the security code printed on the front of any credit card issued by the bank.
The problem is, the form completely blocks the full page, preventing you from logging in — until you fill in all the fields in the form it displays. Then it sends that information (encrypted with SSL, mind you) to a server at the IP address 121.101.216.234, part of the address space allocated to Beijing Telecom.
Your bank may outsource some of its customer service tasks, but stealing your financial identity isn’t part of the normal services your bank provides.
The Web domains hosted at that IP address — cavemonsterfromhell.net, festivaloffire.net, and stratus35.net — share some interesting characteristics in common, other than the hosting location: All were registered by the same person, and two of them (at the time I write this) are on various blacklists for hosting malware files for acting as command and control servers for Zbot Trojans.
The Trojan, named buildxxxxx.exe, effectively hides from sight by making a duplicate copy of itself and rootkitting the destination folder, which is C:buildxxxxx.exe. Inside that folder, the Trojan pulls down a file called config.bin — behavior similar to that of Zbot, though the file is dissimilar from Zbot in several other important ways. It also adds a key named buildxxxx.exe to the HKCU “Run” path in the Registry so it can start up with a reboot, and rootkits that registry key, as well.
Several large banks, including Bank of America, Wells Fargo, and USBank are all targeted by the Trojan in the attack. There’s one detail the Trojan’s creator didn’t anticipate: Dropdown menus on the login page. In the screenshot above, you can see how the Well Fargo login page’s dropdown menu actually peeks through the popup dialog, messing up the nearly perfect illusion.
Meanwhile, we’ve got bulk detection in place that can punch through this Trojan as easily as poking a hole in wet tissue paper. But this raises a point worth repeating: Your bank shouldn’t ask you for information they already have, and if they do (at least, on the Web), you should be very suspicious.




















In this day and age, the advancements in technology have helped to make life easier and convenient. From online banking, to booking vacations, to filing taxes online via computer software…but it seems that it also just creates more and opportunity for criminals to exploit others…
I personally don’t do any online banking anymore. Even with virus protection/firewalls etc. It just seems to risky, and although it takes longer driving and standing in line, I’d rather be more secure when dealing with my finances.
Great info, but how do we get rid of it? None of my programs have been working.
Which programs have you been using?
I’ve run a full Microsoft Essentials scan & full scan using Malwarebytes, and the virus is still present. Any help would be very much appreciated!
I’m facing this issue now when I login to my BOA account. Does any one have any idea of how to get rid of this virus? I have used SUPER ANTI SPYWARE, MALWARE BYTES tools and still having this issue.
So what do I do if I am getting this screen on my BoA?