 If you live in the US, you may have played sports, barbequed, or enjoyed the last long weekend of the summer outside doing something fun outdoors. Unfortunately, that wasn’t an option here in Boulder, where a large wildfire generated a thick plume of smoke and ash. So, what’s a malware analyst to do indoors on a beautiful day with toxic smoke outside? Why, spend some quality time with Koobface, of course.
If you live in the US, you may have played sports, barbequed, or enjoyed the last long weekend of the summer outside doing something fun outdoors. Unfortunately, that wasn’t an option here in Boulder, where a large wildfire generated a thick plume of smoke and ash. So, what’s a malware analyst to do indoors on a beautiful day with toxic smoke outside? Why, spend some quality time with Koobface, of course.
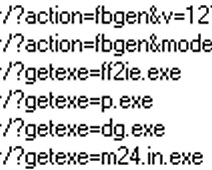
I took a closer look at the worm’s behavior and also noted that, since the Migdal keylogger site went dark for the Koobface crew, they’ve switched to using a new domain as the dead drop for credentials stolen by the Koobface password stealer payload: m24.in, the Web site of some sort of media company based in India. The behavior I saw by the keylogger was virtually identical to that used by the Migdal variant, reported in a previous post. The payload is even named m24.in.exe, just like the Migdal payload was named after the domain where it posted stolen passwords.
It’s been a while since the worm changed its primary method of infection: For nearly its entire existence, Koobface has spread by manipulating the social network accounts of infected users so it appears the user posted a link to a video. Of course, the worm does the posting in the name of the user, and the link points to a page which purports to be some sort of streaming video, but actually pushes the malware on anyone who visits.
And, in order to take on the appearance of a real online video, it uses Flash.
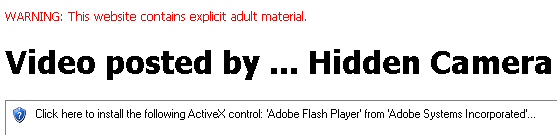
The overall look and feel of the fake video has been static for some time, but the content changes periodically, and the current iteration of the page (which appeared this past April), titled “Video posted by … Hidden Camera,” is still in use and hasn’t been updated since then.
On the video page, a user is encouraged to download and install a file the page claims is Flash Player 10.37 — never mind that Adobe only recently updated Flash to version 10.1 — which happens to be the main Koobface installer. What I didn’t really pay attention to, until this weekend at least, is the fact that the video page actually requires the user to have a previous installation of Adobe Flash installed, otherwise the scam doesn’t work. Talk about stupid malware tricks. Here’s what you see on a test machine with no Flash installed:
Note in the screen above that Internet Explorer threw a warning into both the frame on the page where the video appears, and at the top of the page, prompting the user to install Flash.
The video window that appears, which has all the appearance of an interactive Web page coded in Ajax, is actually itself a Flash .SWF file, playing within a frame in the page. And the Flash video is scripted in such a way that, whenever a user even mouses over the “video” it attempts to force the visitor’s browser to download the Koobface installer, which is typically called “setup.exe” or something equally generic.
So this Flash video that runs is actually a video of a fake Flash update prompt, embedded within a fake video page. If you don’t have Flash installed, you have to install Flash before you can be prompted to install (what you are told is) Flash.
It’s too bad the double-fakery doesn’t simply negate the damage caused by the worm. Here are just a few of the payloads it downloads during the course of its infection:
Koobface still installs a backdoor on infected computers (with p.exe), opens ports in the firewall, pulls cookie data from Firefox (using ff2ie.exe), and steals FTP credentials (using m24.in.exe). Once installed, the worm receives commands, including instructions to open browser windows to fake “antivirus scan” pages, which can lead to more infections. Fortunately, due to either the laziness or ineptitude of Koobface’s creator(s), we can still easily detect and remove the worm from infected computers.