 For years, the makers of those snake oil security programs we call Rogue Security Products have spent considerable effort making up new names, developing unique graphic design standards, and inventing backstories for their utterly useless, expensive scam products. Now a new rogue has taken this never ending shell game one step further, releasing a single program that calls itself one of five different names, depending on what button an unfortunate victim clicks in a highly deceptive dialog box. Let’s call it what it really is, though: A malicious play in five acts.
For years, the makers of those snake oil security programs we call Rogue Security Products have spent considerable effort making up new names, developing unique graphic design standards, and inventing backstories for their utterly useless, expensive scam products. Now a new rogue has taken this never ending shell game one step further, releasing a single program that calls itself one of five different names, depending on what button an unfortunate victim clicks in a highly deceptive dialog box. Let’s call it what it really is, though: A malicious play in five acts.
The rogue’s delivery method, or Act 1 in this melodrama, is no different from the many we’ve seen in the past 18 months which use a Javascript-enhanced Web page to convince viewers they’re watching a live malware scan on their computer. This trick is so hackneyed, it’s become the cybercrime equivalent of the dastardly villain in a silent movie tying the hapless woman to a railroad track, then twisting the ends of his mustache for dramatic effect. Does anyone still fall for this?
Only, this time the fakealert delivers a different payload: When the victim runs the rogue executable (named simply setup.exe), Act 2 begins. The rogue displays a dialog box that looks like an alert message issued by Microsoft Security Essentials, cautioning the victim that a legitimate Windows component present on most or all installations of Windows, such as iexplore.exe or cmd.exe, is actually a piece of malware.
The rogue helpfully offers to perform some sort of online scan, and that’s where it gets weird. The rogue pretends to scan the hard drive with 32 different antivirus engines, a-la VirusTotal. The vast majority of them are well known, at least in the security community. But five are new, and it’s those five that merit closer inspection.
Yes, Webroot appears in their list, even though we’re not part of the VirusTotal system. Thanks for thinking of us, Rogue leader.
At the end of this fiction, the program claims five of those “engines” report the legitimate file is a Trojan — and, wouldn’t you know, each of those programs conveniently offers a “Free install.”
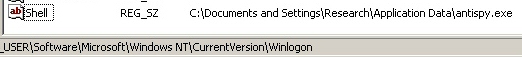
The joke is on the victim, though: Whether you choose AntiSpy Safeguard, Major Defense Kit, Peak Protection, Pest Detector, or Red Cross Antivirus, nothing gets downloaded — what you get instead is Act 3: A copy of that same setup.exe you downloaded, only renamed to match the name of the rogue you happen to choose.
The hilarity only starts there. Depending on which Free Install button you click, the program spawns another dialog box that looks like some kind of installation wizard. The installation dialog is identical except for the name of the product, and it looks like the creators of this rogue copied, verbatim, the boilerplate text of the GPL software license…
…including the instructions that follow the text on the Free Software Foundation’s Web site that explain how software developers are supposed to display the GPL under various circumstances.
Oops. Not that anyone ever reads software license clickwrap agreements anyway, right?
Or error dialogs with obscure warnings.
After this farce wraps itself up, Act 4 gets underway. The dialog prompts the victim to reboot the computer. After the reboot, the rogue launches before the Explorer shell loads, thanks to a little registry tweak.
Now the rogue goes into full circus-act mode. I believe the problem here is a very low level of self control on the part of the rogue’s creator, as confirmed by the product itself.
The program pretends to scan the hard drive, warning the user that some infected programs (which include any installed browsers, as well as other legitimate Windows components), need the rogue’s “Required heuristics module” to disinfect these not-infected programs.
Even the firewall (or, in this case, FireWall) log slowly fills itself with bogus data.
And that leads us to our big conclusion, Act 5, the hard sell: Of course you need to buy their product in order to fix these nonexistent problems, and the program cheerfully recommends that you buy the lifetime license for the low, low price of…$99.90.
Fortunately for the customers of a real antivirus product, the rogue is almost effortlessly removed, and the startup hijack setting is easily deleted. What isn’t so easy to fix is the fact that some people are likely to believe the fiction that the rogue is a real product. If there was an awards ceremony for cybercrime, this tool might pick up the trophy for best supporting actor in furtherance of fraud.



























Now i feel weird to read all about malware stuffs because day in day out its all about new threats and it seems the antivirus software have fail to do its job.
Thanks for your hard work on warning. I’m not sure I understand all this, but you have certainly opened my eyes. Thanks again