 It’s been more than a week that we at Webroot, and countless others, have been getting floods of bogus messages with HTML attachments. I thought I’d give the curious readers of this blog a quick glance at one of the drive-by sites that load in the browser if you try to open the file.
It’s been more than a week that we at Webroot, and countless others, have been getting floods of bogus messages with HTML attachments. I thought I’d give the curious readers of this blog a quick glance at one of the drive-by sites that load in the browser if you try to open the file.
As I’d mentioned previously, the HTML files themselves simply contain highly obfuscated Javascript (code that’s hard for humans to read but easy for machines to interpret). When you try to load those malicious scripts into a browser, the script instructs the browser to load a page from another Web site. In fact, the file I saw today goes to server 1, which bounces the browser to server 2, and then a script on server 2 loads more files from servers 3 & 4 in a full-screen iFrame.
In the end, what I saw looked like an update to what has become the “classic” Javascript fakealert. Unfortunately for the malware distributors, this so-called update is laughably obvious. These are clearly not the sharpest tacks in the box.
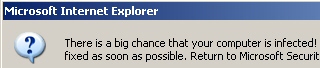
It all starts with a warning popup which reads:
There is a big chance that your computer is infected! They can cause data loss and file damages and need to be fixed as soon as possible. Return to Microsoft Security Assessment Tool and download it to guard your PC.
Wow, really? How big is the chance? Is this more like a scratch-off lottery ticket level of chance, or is it closer to a look under the bottle cap to see if you win chance? What they don’t tell you is that your chance of becoming infected with an annoying rogue increases to about 100% if you continue down this well-worn path.
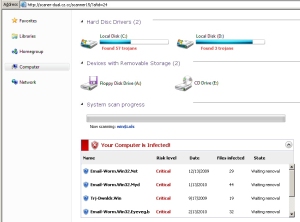
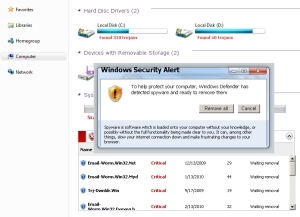
The next thing that shows up is a revised version of the hey, look, we’re pretending to scan your PC and will show you a bunch of scary-looking stuff window. The icons have been changed, and the hard drives are now inexplicably referred to as Hard Disc Drivers, but otherwise the charade is pretty much par for the course. While the so-called scan proceeds, text fills a box labeled with the header Your Computer is Infected! that’s placed near the bottom of the window, detailing the supposed infections that have been detected. Remember, at this point, we’re still looking at an animated Web page.
The page is generated by a lot of scripting and a few graphic files. Here’s what one of those graphic files looks like, starting with the hard drive icons:
Then there’s the “removable media” icons:
Someone invested in a new clip-art collection. Here’s the fake “results” dialog with nothing in it:
And here are the labels that run alongside the left edge of the fakealert window:
Finally, here’s a screenshot of what it looks like when you put all this together.
I love the new names for the malware the fakealert pretends it finds. What bad things do you suppose a “malware file” with the name Email-Worm.Win32.Eyeveg.b will do? Hit me in the face with a tomato while it spams my friends? Taking a look at the HTML of the page, you can see the full list of fake detections. They are:
Email-Worm.Win32.Net
Email-Worm.Win32.Myd
Trj-Dwnldr.Win
Email-Worm.Win32.Eyeveg.b
Lemena.3544
Macro.PPoint.Attach
Virus.BAT.Vr.a
Backdoor.Perl.AEI.20
Trojan-Spy.Win32.WMPatch
Trojan-PSW.Win32.Aletc
Trojan-Clicker.Win32.Bitdefener
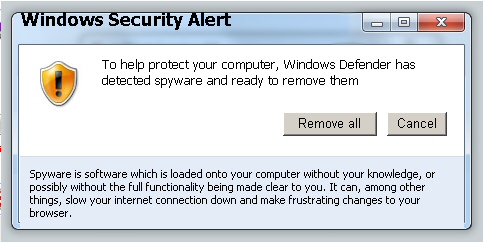
The page then calls a script which generates a popup titled Windows Security Alert over the top of the scan window. Text alignment? Who needs it?
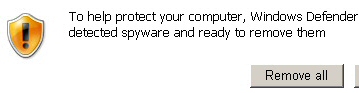
This popup helpfully, verblessly, informs the victim that To help protect your computer, Windows Defender has detected spyware and ready to remove them. Yeah, right.
Here’s the complete package in all its glory:
The dialog also states Spyware is software which is loaded onto your computer without your knowledge, or possibly without the full functionality being made clear to you. It can, among other things, slow your internet connection down and make frustrating changes to your browser.
With this, Webroot agrees, which is why we’ve added detection for the rogue AV payload the page downloads, as well as the domains from which this fakealert appears, into our definitions. So, if you’ve been just curious about what happens when you open one of those malicious file attachments, I hope this satisfies your curiosity. Just don’t open them.



















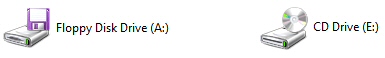
Interesting post…
I use linux, and as far as I can see this problem is mostly related to Windows computers.
Is that correct?
Thanks,
Anders
Yes and no. The HTML attachments will run in any browser on any platform. Whether the destination site is able to exploit your computer is another matter entirely.
Brilliant. Thanks for that. I had this happen to me just yesterday. The small warning banner just seemed to jump from a web page which I was searching, I don’t remember seeing this particular sign before but even though its appearance didn’t seem genuine, it is always a shock to think your PC has been infected by malware. However, I am always suspicious of anything dubious like this, so before doing anything, I simply rang my business partner for assurance (He’s the Geek in our business and he’s sharp as glass) He calmly explained what it would be and advised me to always check my latest downloads to be sure that nothing that I wasn’t previously aware of was shown there. But your comment made me laugh as on hind site I realised it had been created by, as you so humorously explained, a ‘blunt tack’ in the box