 While nowhere near the size of the mammoth Facebook, the social network Multiply is no slouch. Based in Boca Raton, Florida, the site is designed around not only sharing photos and videos with friends and family, but also a relatively novel concept called social shopping, which permits users of the site to shop together in a virtual marketplace, or even set up an Internet storefront. At last count, according to Multiply’s blog, the site has over 12 million users, which means that the Multiply Market may be one of the largest single shopping Web sites in Southeast Asia, where most of its users live.
While nowhere near the size of the mammoth Facebook, the social network Multiply is no slouch. Based in Boca Raton, Florida, the site is designed around not only sharing photos and videos with friends and family, but also a relatively novel concept called social shopping, which permits users of the site to shop together in a virtual marketplace, or even set up an Internet storefront. At last count, according to Multiply’s blog, the site has over 12 million users, which means that the Multiply Market may be one of the largest single shopping Web sites in Southeast Asia, where most of its users live.
I would never have even known about Multiply (it’s one of nearly 200 active social network sites listed on Wikipedia) if it weren’t for one of our Threat Research analysts, Rhoda Aronce, who hails from the Philippines and uses Multiply to keep in touch with family. She received an odd-looking message that appeared to come from Multiply on her Yahoo mail account yesterday, and it set off alarm bells. Good thing, too, because it looks like a spam campaign targeting Multiply users is trying to infect those users’ computers with a rogue AV that calls itself Antivirus Solution 2010 Next.
The initial spam message uses familiar social engineering tropes: It’s a message that looks like it was sent via Multiply’s servers to Rhoda’s Yahoo mail account. The message body reads
heyy! (username), do we know from some place isn’t it? so here’s a special video i did for you, ull recall me!, pls holler me back!!!, kisses <3
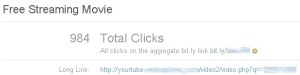
The message is dominated with a photo of what looks like a streaming video window that says Click here to see movie. That’s where the fun begins for researchers, but please, don’t click this at home, especially if you’re in the middle of shopping online. Leave getting infected to the professionals. If you see something like this in your email inbox, just delete the message.
The image of a video player was only that — a static picture of a video player. However, it was hotlinked to a bit.ly shortcut. We all remember the old put a + sign after the bit.ly shortlink to see its information page trick, right? Here’s what I was treated to:
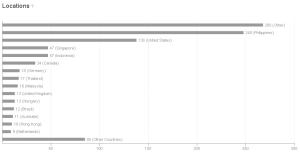
So, as of last night, 984 people had clicked the spam message and followed the link. (That doesn’t mean 984 computers were infected — more on that in a minute.) Here are some stats about the geographic location of those people who clicked the links:
Now it starts to make sense. The single largest geographically identifiable collection of victims is based in the Philippines, followed by the US, Singapore, Indonesia, and a dozen other countries. Finally, the referrers tab tells us what page people were reading when they clicked their shortlinks. It looks like the largest percentage came straight from Multiply, while most of the rest were reading their Yahoo mail.
Now, when you click the link (the yourtube URL in the bit.ly window above), you’re taken to a page on a free Web hosting site which looks like this:
Yes, Madeleine, someone has taken a screenshot of Windows Media Player and dressed it up (badly — look at those crops, they cut off the edges of the window) to make it look like a streaming video page. Take note of that text below. Does that remind you of anything? Yeah, me too. Raiting x/10 should be a subtrope of its own.
If you click anywhere in the window, the fake player page displays a warning dialog which reads You must download new video codec to play this video file. Start downloading? with an “OK” and “Cancel” button.
If you click OK, you’re presented with a standard “File Download – Security Warning” dialog that asks whether you want to save or run the file. Anyone who clicks Run at this point is infected. If you click Save, you could still infect yourself by launching the program, named divxplayer.exe (MD5: 1967c9470706360a25afb5a5555d21fe), when it has been saved to your computer.
The installer first checked in with a Web site named httpguard.us (which is actually hosted on a machine in Russia). On our test system, the Trojan sent a query string to that server uniquely identifying the infected computer. The response from the server was just two characters: OK. Afterwards, the Trojan contacts a different site, httpwizard.us (hosted in the Netherlands), and sends a query asking the server for a URL where it can pull down a payload. As of last night, it wasn’t delivering a payload, but it was notable that the IP address hosting httpwizard.us is shared with antivirussolution2010next.com. Coincidence? There ain’t no such thing when it comes to rogue antivirus.
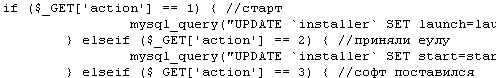
Now, the best part is that the doofus running this scam didn’t bother to protect his server in any way. What does that mean? Well, I was able to navigate through the directories on the server with just a browser and, by chance, happened to run into the source code for a PHP script he’s running on the backend. Here’s a picture of what it looks like.
From all appearances, the script does some geolocation search on the IP address of the visitor, tracks whether the infected user has accepted the EULA and whether or not they’ve installed the rogue. It then adds that information into a database. Looks pretty similar to what a lot of botherders do with their botnets for tracking infected users and analyzing them. It’s nicely commented in Russian, as well, which probably clears up any lingering doubts as to where this dog and pony show originates.
Bottom line, it appears no social network is too small or narrowly focused to be off a malware distributor’s radar screen. And it pays to be cautious, especially with spam, during this holiday shopping season, especially as we’re in the run up to Black Friday.






















His script is easily open for SQL injection judging by that source: you should distribute justice.
Not surprising at all. I prefer to distribute public information and leave the distribution of justice, whatever that might be in this case, to someone else.
Fantastic article Andrew.
You malware analysts never cease to amaze me in your investigative process.
Thank you Rhoda A. for catching an reporting this.
Thank you Andrew for the excellent write up it has been passed around in Multiply.
uh oh… kinda realized too late that this was screwed up since i opened it early when i just woke up. I was using a mac when i checked though, so i stopped when it asked me to install a .exe file. so… uh… should i worry about anything? like say, change my password for my multiply or yahoomail?
…can’t believe I’d fall for something like this.
While it isn’t likely your passwords were phished, it’s not a bad idea to change them anyhow.
Yea, I had it sent to me. Opened it and F-Secure caught it right away… Poor excuse for a l337 haxor should be ashamed of himself.
Really good.
Recently i received facebook notifications as email-
In that, my friends commenting the ” why u get tagged in this video?”.
I checked that notification, but it is not active.
That page shown to be like restricted one.
Its pretty similar case!
I found it here, what the idea is ?
Thanks!!