 A complex and elaborately conceived family of malware that originates in China installs the Apache Web server, as well as half a dozen keylogger and downloader payloads, disguised as components of legitimate apps. We and a few other antivirus vendors are calling this type of malware Taobatuo.
A complex and elaborately conceived family of malware that originates in China installs the Apache Web server, as well as half a dozen keylogger and downloader payloads, disguised as components of legitimate apps. We and a few other antivirus vendors are calling this type of malware Taobatuo.
It just so happens that I’ve been setting up a Windows virtual machine with the latest versions of Apache, MySQL, and PHP for an unrelated project. I hadn’t installed these apps onto a Windows box before, and Apache in particular is notoriously finicky about Windows installations, so after several days of trial and error (mostly error) I was somewhat amused to discover, after finally getting Apache to work, that the malware sample I tested actually pulls down its own working, customized Apache installer…along with a bunch of phishing Trojans, keyloggers, and downloaders, all dressed up to look like the services you might see on a Microsoft-based Web server.
It just goes to show how much good these malware creators could accomplish, simply if they wanted to. But that’s clearly not the goal. The malware, along with text files containing instructions for the malware, came from taobao.lylwc.com. That’s not to be confused with Taobao.com, one of China’s most heavily trafficked Internet portals. This site and the real Taobao are not related in any way I can determine, other than the (ab)use of the Taobao name.
 The lylwc.com domain itself is quite a piece of work. It claims to offer free downloads or streams of current Hollywood movies, as well as an extensive library of films and TV shows. The operative word is “claims” — when you try to view those movies, the site attempts to push a download of a Trojaned installer for the QVOD media player (a streaming media app that’s popular in China). So let’s just say I wasn’t all that surprised to find the taobao subdomain of this Web site hosting a raft of malware.
The lylwc.com domain itself is quite a piece of work. It claims to offer free downloads or streams of current Hollywood movies, as well as an extensive library of films and TV shows. The operative word is “claims” — when you try to view those movies, the site attempts to push a download of a Trojaned installer for the QVOD media player (a streaming media app that’s popular in China). So let’s just say I wasn’t all that surprised to find the taobao subdomain of this Web site hosting a raft of malware.
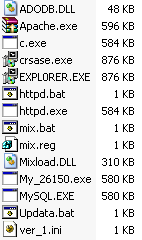
We’ve been seeing files originating from this domain since August, and there’s evidence online that they’ve been circulating and infecting computers in China and elsewhere since as early as March, 2010. The infection seems to begin when we run one of the executable installers (a process that could be invoked by a drive-by download). The malware executables all have .txt extensions, and are either self-extracting RAR archives or NSIS installer files (either of which are easily taken apart by a handy, free tool called Universal Extractor).
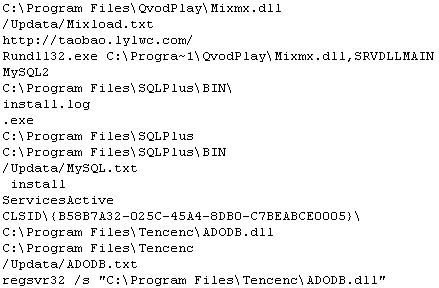
The main installer for the malware appears to be a DLL named Mixload.dll (MD5 ec3653025fb6ba3578e5fd9b190f4e63, among others). When loaded, Mixload moves itself to C:Program FilesQvodPlay — the directory that is the default installation location for the QVOD player — and sets a run key so it starts up with Windows or whenever a user with QVOD installed starts that program.
The strings include a reference to what the Trojan’s creators call it, Taobao_netking_master_1. One thing’s for sure: these guys might be good at hiding their malware in plain sight, but they are neither humble nor masters of subtlety.
It also begins pulling down additional installers, including one which drops other malware files into a directory named after Oracle’s SQL*Plus product. The first payload it pulls down and executes is named EXPL0RER.txt (with a zero instead of the letter O in the filename, MD5 06B67929C28D002693EAE3BC891492A8), which is an NSIS installer. And it retrieves a list of commands and instructions, some of which are in simplified Chinese characters, encoded in base64:
I found the translation of some of these commands (the lines that begin with pid=) illustrative, if a bit obtuse:
The EXPL0RER.txt file contains the self-extracting RAR with the Apache Web server files inside (MD5 4CA888FC1E5A9074F0CDE405E434E9D8), as well as a Trojan named svehcet.exe (MD5 972db39350c9b3f4dc169beb5be0212f), which EXPL0RER installs as a service in the C:Program Filesadobeflash folder. EXPL0RER also duplicates itself to the C:Program FilesSQLPlus folder using the filename crsase.exe.
Mixload also pulls down several other components:
- MySQL.txt (MD5 4A5D515D24E6A62B78C7B5D29750A313) is an executable that ends up as a file named My_26150.exe in the C:Program FilesSQLPlusBIN folder;
- c.exe (MD5 E97C4DA9B829E5335711BA42784637CF) drops into C:Program FilesApache with a duplicate copy in C:Program FilesApachebin named HTTPD.exe, and periodically runs batch files that upload stolen data elsewhere;
- http.dll (MD5 9ea479de6a8d9d2f499b20fef9abd2ac) is a game password stealer and keylogger belonging to the Trojan-Backdoor-Graypigeon (Hupigon) family, installed to C:Program Filesadobeflash;
- adodb.dll (MD5 17776a78eedda974732c9593dafdb79a) gets installed as a Browser Helper Object (CLSID: b58b7a32-025c-45a4-8db0-c7beabce0005) into C:Program Filestencenc (likely a deliberate misspelling of Tencent, the publisher of QQ, China’s most popular instant messenger).
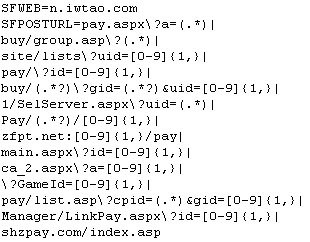
The BHO hijacks Web pages that have specific names (such as pay.aspx or LinkPay.aspx) that are used as the payment pages on some shopping Web sites, using a complicated regular expression rule to determine which IIS pages to monitor. It also redirects browsers trying to visit a small number of specific Chinese-hosted Web sites to a page on the n.iwtao.com domain.
In summary, the brands/businesses whose names were stolen for use by this Trojan include Adobe, the Apache Software Foundation, Oracle (both for SQLPlus and MySQL), Microsoft (for the adodb.dll, expl0rer, and other payloads), and the Chinese firms QVOD, Taobao, and Tencent. All this leads me to believe that the creators must feel they are untouchable, untraceable, or otherwise beyond the reach of any law enforcement. The fact that these shenanigans have been going on for nearly a year indicate that they may be correct, or just arrogant.
Our products currently block the domain, and also remove the files left behind. Without the connection to the domain, the malware samples cannot do anything, as they rely on instructions (in the form of plain text files) hosted on the malicious server in order to run commands. If you’ve suddenly discovered Apache’s httpd.exe service running on your machine, despite never having installed it, or ever using your computer as a Web server, it might be time for a quick scan.





















Excellent description!