![]() Where’s the work ethic, malware geniuses? If this latest example of shenanigans is the best you can deliver, you’re not even trying to generate convincing scams — or even something that makes sense — anymore.
Where’s the work ethic, malware geniuses? If this latest example of shenanigans is the best you can deliver, you’re not even trying to generate convincing scams — or even something that makes sense — anymore.
One of our Threat Research Analysts pointed me to a Web page hosting a fake update program for Firefox the other day, and the only thing it was useful for was a pretty good laugh.
In replicating the Firefox “you’re now running…” page, the malware distributor managed only to build something that looks remarkably similar to a more sophisticated, and ultimately more plausible, scam we first described this past summer. But the scam is full of fail.
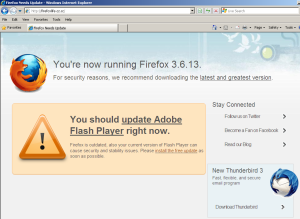
The malicious page, which had been hosted at firefoxlife.cz.cc (and is now, thankfully, shut down), looks like the page that automatically pops up when you first launch the Firefox browser after you’ve applied an update. Ultimately, it not only fails the smell test, giving the user contradictory information, but also fails at the effective malware test, delivering multiple different samples, all of which crashed when we tried to run them on test systems or in debuggers.

The easiest failure to describe is the text of the page. At the time I write this, version 3.6.13 is the latest version of Firefox available that isn’t a beta or a nightly build. But the warning message is contradictory, telling the reader both “You’re now running Firefox 3.6.13” and “we recommend downloading the latest and greatest version.” Huh? A simple update check could confirm to any concerned Firefox user that you are, in fact, running the latest and greatest version, but silly issues like easy verifications of demonstrably wrong information are of no importance to the goon who produced this marvel.
Then the author of this farce gets a bigger shovel, and digs himself into a deeper hole with the “Firefox is outdated” blurb in the box touting an update to Adobe Flash. Wait, so am I downloading an update to Firefox, or an update to Flash? And please note that, in the screenshot above, I’m viewing the page using IE 8. Malware guy dropped his Firefox scam in my Internet Explorer? Even the people who pulled together the black hat SEO scam in August customized the page so it appears to be an update to the browser version you happen to be using when you view the page. This is just shoddy.
Finally, the site pushes down a file named Firefox-update.exe, but it only appears when you click the text “update Adobe Flash player.” Oh, and it sports the Windows Media Player icon of a media file. So is this supposed to be a fake Firefox, Flash, or Media Player update, a fake codec, or a bogus music file? Throwing caution and reason to the wind, the malware distributor would probably answer that question with a resounding yes.
Of course, the cherry on top is the fact that none of the malware samples we retrieved actually worked.
Over a period of three days, we pulled down nine samples. Three were duplicates, two were corrupted files, and four were unique executables. Best news for everyone: every single one of them crashes when we ran it, and we really tried to run it on a variety of Windows versions, on both real machines and in VMs. We got zilch, other than a few references in the file’s strings to M S Extrim Edition 2011 and Extrim Edition.exe. I and a few others spent more time looking at Dr Watson, struggling in vain to get this lousy code to run, than looking at the malicious file itself.
The last time we took a look at bogus browser updates, the bad guys had their act together. This time, not so much. Really, it’s like they’re just phoning it in, now. Sloppy work all around, malware doofus (or perhaps doofuses? Doofi?). And to all you scam artists, a holiday toast: May the quality of your code continue its downward slide towards mediocrity and failure into next year and beyond. It gives me such good material to work with!




















Um – berating the bad guys for writing sloppy pages seems to be the wrong thing. “Hey guys – this all you got? My 6-year old can write better stuff than this! C’mon, you can do better!”
Remember, it’s a *good* thing when the bad guys get sloppy!
Agreed. I don’t think anyone (except, perhaps, the criminals themselves) would argue that their failure is anything other than a good thing. However, I don’t see why I shouldn’t mock their incompetence. After all, aren’t these people alleged to be those big, bad cybercriminals we’re all supposed to be afraid of? They’re more like bank robbers who leave behind a wallet containing ID.
Also got to think of it this way: If the idiots keep writting bad malware that doesn’t work, Webroot might go out of business.
By taunting them, Mr. Brandt is only practicing “job security”.
In this economy, I really can’t blame him for poking the bear.
I would like nothing more than to never have to deal with malware again. If all malware disappeared tomorrow, I would be thrilled. I certainly don’t need or want the kind of job security you’re describing.
Are you implying we only detect the poorly-written stuff? That’s hardly the case. AV-Test says we do much better than the rest of the industry at removing active infections. The poorly written stuff is merely comedy gold.
Then again, I also disagree with your metaphor. Instead of “poking the bear” a better description of what I do is “deliberately step in a pile, then scrape the dog doo off the sole of my shoe.”