On the morning of January 2nd, still bleary eyed, I checked my email to find a charming notification informing me that I’d received an electronic greeting card. Yay! I thought to myself: The first targeted malware of 2011 plopped right into my lap.
On the morning of January 2nd, still bleary eyed, I checked my email to find a charming notification informing me that I’d received an electronic greeting card. Yay! I thought to myself: The first targeted malware of 2011 plopped right into my lap.
I immediately pulled up my research machine, browsed to the URL in the message (don’t try this at home, kids), and found my test system swamped in malware. After classifying the files and their source URLs into our definitions — I didn’t want this to happen to you, after all — I turned the computer back off and slept until Tuesday, when I resumed my analysis.
As it turns out, the payloads delivered by the drive-by download are as common as sand at the beach, but some of the techniques used by the malware’s distributor to obfuscate the true nature of the executable payload files (which may have been stored on what appears to be a hijacked, legitimate server running Joomla) are fairly novel, and also a bit ridiculous.
Our festive drive-by started with a browser exploit against the outdated version of Internet Explorer running on my test system. The page looked like it was trying to load a flash video, and displayed just a link that says “You need to update to the latest Flash Player.” Without waiting for me to click the link, the page pulled down and executed the first payload, a downloader called adobeupdate.exe that’s relatively recent to the scene: Trojan-Downloader-Karagany. We first wrote about this trojan in November.
Karagany quietly copied itself to the desktop, naming the file err.log####### (where the # signs indicate a random number from 0 to 9, which changes each time you run the Trojan). This behavior is virtually identical to what we saw two months ago.
What was interesting was just how the malicious Javascript running on the server hosting the drive-by pulled down the Karagany payload. The payload was embedded in the source HTML of the driveby page, but it looked like a jumble of binary nonsense data. However, a Javascript file called within the context of the page performs a little computational gymnastics with the jumbled data, as shown in this screenshot.
The malware was first encoded in Base64, then the Base64-encoded version of the file was, byte by byte, reversed. The command within the script that switches the data back to a readily decodable format is called “reverseBase64Chars.” The end result was a double-encoded binary data embedded in the page, which looked like junk. However, when a victim visits the page, the script runs, and the script does the required byte-flip on each character, then decodes the Base64, as it writes the file to the victim’s PC. The infographic below illustrates the malware distributor’s elevator pitch description of the process.
Looking back at the research I had done in November, it appears that this double-decoding baloney has been part of Karagany’s infection behavior since I first looked at it, but I hadn’t noticed it the previous time. It’s worth noting that as silly as it seems, the process appears to be effective at masking the true nature of the binary — the file is hidden in plain sight, so to speak.
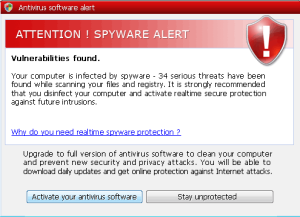
Karagany’s previous payload was a rogue named Antivirus 2010. Its new rogue payload carries the oddly generic moniker Antivirus Scan. These bogus products report that a raft of infections have taken control of the PC, and try, without a hint of subtlety, to coerce you into paying as much as $70 for a useless “subscription.”
Hey, after all, Antivirus Scan’s Web site claims to provide powerfull protection, even in the Standart Edition. The $70 Ultimate version must be really good, because the description says “Buying this version, you obtain an ultimate protection. Since this day you can feel safe.”
That’s a lie, since forever. And what about these testimonials?
Thanks to this fraud, Gary in London is finally able to read his Apache server logs free of the fear and loathing that previously accompanied such a task? Well, free of the fear, anyway.
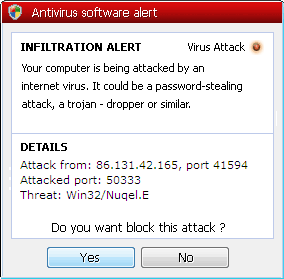
Among the tricks this rogue employs are the fake scan, the fake “detection of malicious activity” dialog box;
…the “fake System Tray warning message balloon”
…the fake firewall alert
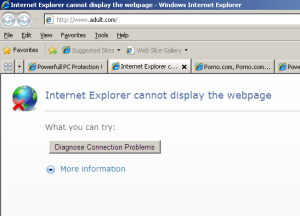
…and the instant classic, “randomly opening a new tab in the active browser to a porn site” trick.
That one never gets old, except, of course, when the porn site the rogue’s creators chose to load is offline.
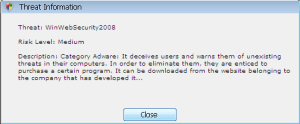
I can also appreciate the recursive irony when a rogue antivirus infection displays a warning message about a (supposedly different) rogue antivirus infection.
All well-deserved mockery aside, though, I hope the real lesson gets across: Avoid links that point to electronic greeting cards, especially when those links come from a source you don’t know, and point to a site you’ve never heard of. Electronic greeting card emails are, quite possibly, the most hackneyed trope in social engineering. It’s fun to get into the holiday spirit, but you shouldn’t let your guard down for a second, even when you’ve been on vacation.