 I didn’t want to let too much time pass before I wrote about a new Zbot-like bank phishing Trojan variant that came across my desk last week. The keylogger started arriving the first week of February as an attachment to a spam email designed to look like it came from United Parcel Service. No, the old malware trope of spammed shipping invoices is not dead yet, Alice, but we’re going to follow this one down the rabbit hole anyhow.
I didn’t want to let too much time pass before I wrote about a new Zbot-like bank phishing Trojan variant that came across my desk last week. The keylogger started arriving the first week of February as an attachment to a spam email designed to look like it came from United Parcel Service. No, the old malware trope of spammed shipping invoices is not dead yet, Alice, but we’re going to follow this one down the rabbit hole anyhow.
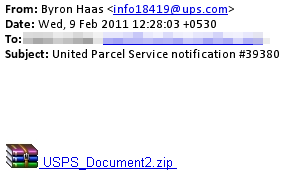
The brief message had a Subject line of “United Parcel Service notification” followed by a random, five-digit number, and a file named USPS_Document.zip attached to the message. Why spammers seem to confuse the US Postal Service with UPS eludes common sense, but I think it has been made abundantly clear by now that, by and large, the people who send these kinds of files around aren’t the sharpest tacks in the box. The HTML body of the message indicated that the .zip file contains a tracking number, but that’s just part of the ruse.
![]() The Trojan is readily identified by its appearance. It uses an old Adobe PDF document icon, but the programmers picked a version of that icon with an X drawn over the top. D’oh. The file also throws an error when run in a virtual machine that forces the VM to bluescreen, but that didn’t affect our ability to analyze the file. We could execute it and observe its behavior without a problem. This new Trojan installs services that remain memory resident after the installer has run, dropped its payloads in the Application Data folder, and deleted the original copy of itself.
The Trojan is readily identified by its appearance. It uses an old Adobe PDF document icon, but the programmers picked a version of that icon with an X drawn over the top. D’oh. The file also throws an error when run in a virtual machine that forces the VM to bluescreen, but that didn’t affect our ability to analyze the file. We could execute it and observe its behavior without a problem. This new Trojan installs services that remain memory resident after the installer has run, dropped its payloads in the Application Data folder, and deleted the original copy of itself.
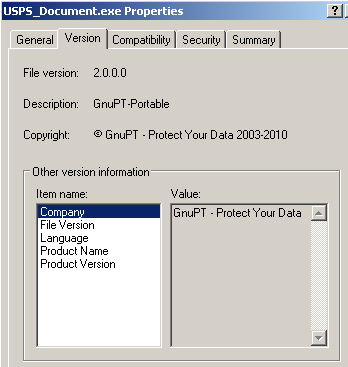
The attached Trojan itself had the appearance that it had been encrypted using a free tool called GnuPT, but if it had, that encryption falls apart as soon as you successfully get the file to load into memory. Some of the installers had spoofed Properties sheet data indicating they were the Opera browser.
Taking a closer look at the strings indicates exactly which banks are targeted by this variant.
The targeted banks include US-based Bank of America, Chase, and Capital One, as well as five banks based in Australia, six based in Germany, four in Italy, two in Russia, and two based in Cyprus. In addition, the Trojan targets two online payment services that have a less-than-stellar online reputation for link-spamming message boards and blog comments.
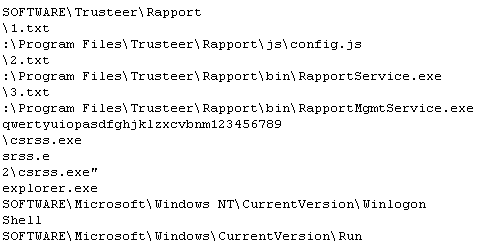
The strings also indicate that the Trojan makes an attempt to disable Trusteer’s Rapport service, an application employed by some online banks to help protect their customers from these kinds of keyloggers. We didn’t test the Trojan on a box with Rapport installed, so we didn’t actually see whether the Trojan was successful, but in the past, Trojans that target Rapport were unable to trip up Rapport’s components, which have a built in self-protection mechanism.
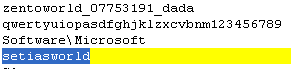
As a part of the setup process, the Trojan creates a registry key under HKEY_CURRENT_USERSoftwareMicrosoft named setiasworld and generates a unique ID for the infected machine for the Data value of the key. When the Trojan contacts its command-and-control server, it submits the value of this Registry key in the query string.
The CnC server returns binary data which includes commands to download additional payloads, which we already detect as Trojan-Pushu (aka Cutwail) and Trojan-Backdoor-Poebot.
One of the payloads installs a rootkit, and another, second backdoor component. This second backdoor contained a list of IP addresses and URLs to which it presumably submits stolen credentials over port 443/TCP, typically used for SSL-encrypted secure HTTP connections.
The list of domains includes nightphantom.com, romanspamer.com, eveningquest.com, and (most tellingly) cheburash.com. According to colleagues here literate in Russian pop culture, this is likely to be a reference to an early 1970s-era Russian cartoon TV series called The Adventures of Cheburashka and Crocodile Gena, pictured above, in which the top-heavy title character of Cheburashka is most well known for having a hard time not falling down. Accordingly, as we managed to trip up this nuisance with little difficulty, we’ve named our new definition for the spy Trojan-Backdoor-Downfall.