![]() A novel worm we’re calling Worm-IM-Shorty appears to be winding its way through Facebook and some instant messaging services, with its come-on disguised as a link to a photograph hosted elsewhere. But when recipients click the link, they receive an executable Trojan instead, dressed up with the name and icon of a JPEG image.
A novel worm we’re calling Worm-IM-Shorty appears to be winding its way through Facebook and some instant messaging services, with its come-on disguised as a link to a photograph hosted elsewhere. But when recipients click the link, they receive an executable Trojan instead, dressed up with the name and icon of a JPEG image.
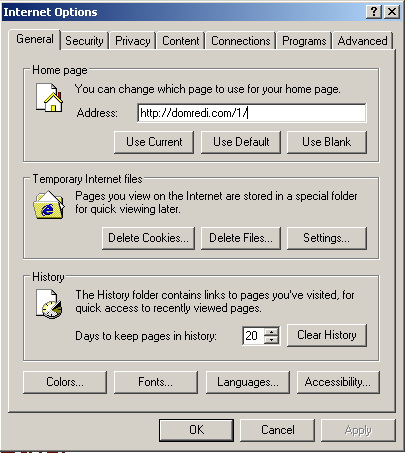
If one double-clicks the file, the Trojan turns the computer into an advertising cash cow for some enterprising malware distributor. The Trojan modifies the active browser’s home page setting to a malicious page on domredi.com, which in turn redirects the browser, at random, to one of several domains hosted on a server in The Netherlands. Each page the browser loads is filled with ads, and when you load an ad-filled page, someone likely gets paid. Follow the money, and you’ll find the perps.
The links spammed by the Trojan all share certain common characteristics, making them easy to spot. But there are still people out there — I’m sure you know a few — who will just click any blue, underlined text, no matter what it says or how dodgy it might seem. We, collectively, have to correct this self-harming behavior.
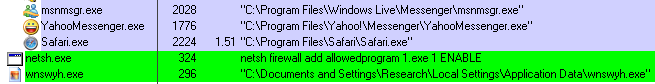
We first stumbled across the Trojan in our malware repository, waiting to be processed. Upon execution it drops a program into the logged-in user’s Application Data folder (with a name using six random alphanumeric characters), and writes a run key in the Registry to start up that program after a reboot. The Trojan also adds an exception rule to the Windows Firewall for a program named 1.exe, but the samples we tested didn’t drop or download a payload by that name.
A Facebook code injection, in progress.
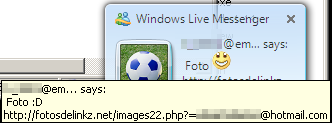
A Live Messenger popup alerts to a propagation message from an infected test account.
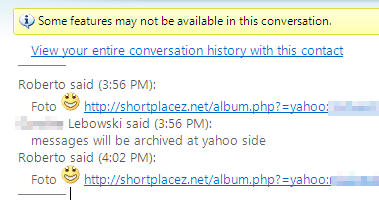
The payload program targets Facebook accounts, Windows Live Messenger, and Yahoo Messenger for propagation. We watched it inject links and one-word messages into Facebook wall posts and private messages from the infected PC’s Yahoo IM client app to all other accounts in the IM buddy list.
The Trojan, once it had transmitted its links, also prevented us from opening the chat logs in Yahoo IM, which you normally do by double-clicking the buddy’s name or icon in the buddy list. Until you quit and restart Yahoo IM’s client, double-clicking a buddy name has no effect. But after you restart the app, the logs will contain the malicious links, which always have the targeted victim’s account name in the query string of the URL.
The homepage hijack is easily reversed, but still annoying. The link to domredi.com randomly redirects the browser to one of several sites. The sites all look like they were built from a template, but each has been customized enough to make them look sufficiently different to the casual user.
The sites you end up on include a2articles.com, diggarticle.com, easynetseek.com, digitword.com, qoolsearch.info, articleslot.info, and several others. All the WHOIS information on these domains are hidden behind either PrivacyProtect.org or Domains By Proxy private registrations. Most pages also contain the text sponsored by Google, though it’s highly unlikely this is the case. Easynetseek.com wins the unintentional irony award for having a large anti-software piracy ad from the Business Software Alliance appear ‘above the fold’ on its page.
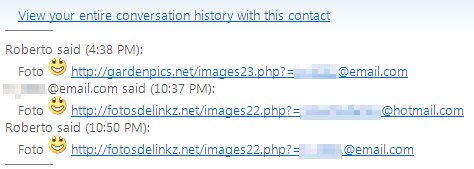
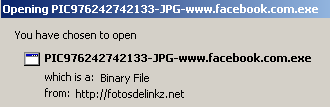
The sites where malicious payloads (like PIC976242742133-JPG-www.facebook.com.exe above) originate — which include gardenpics.net, shortplacez.net, golynto.com, and fotosdelinkz.net — were all registered yesterday or today. Any domain registrants masked their identities behind a whois privacy protection service (an unusually expensive choice).
We’re working to add these domains, and any new ones the worm begins using, to our Brightcloud domain reputation service. But if you could convince your click-prone friends to resist their urges, everyone would be much better off.






























A Pleasure megérteni a blog. A fenti cikkek elég különleges, és nagyon élveztem olvasás a blog, és rámutat, hogy kifejezésre. Nagyon szeretem megjelenni vissza több mint egy tipikus alapon, postai úton sokkal több a téma. Köszönöm, hogy közös … ne írásban!
Great post! We will be linking to this great
article on our site. Keep up the good writing.