(Update, July 11, 2011: On May 25, 2011, we were contacted by representatives of Future Ads, LLC, the parent company of both Playsushi and Gamevance. Future Ads informed us that they, too, had been victims of a scam perpetrated by rogue affiliates who seemed to be involved with the malicious campaigns we described in this post. Future Ads claims that it has taken action to prevent this type of abuse from happening in the future.)
 A worm that has been circulating on Facebook in the form of a Facebook application appears to have been engineered to drive traffic to a sleazy online advertising network which tries to connive people into installing software and disclosing a great deal of personal information about themselves in return for the promise of outrageously large gifts or prizes. As I write this, nearly 5 million people have fallen victim to this scam in just the past two days.
A worm that has been circulating on Facebook in the form of a Facebook application appears to have been engineered to drive traffic to a sleazy online advertising network which tries to connive people into installing software and disclosing a great deal of personal information about themselves in return for the promise of outrageously large gifts or prizes. As I write this, nearly 5 million people have fallen victim to this scam in just the past two days.
Last month, we published a report about a spam campaign designed to lure people into clicking a link to a bogus YouTube video. In that case, when you tried to play the video, your browser was instead redirected into an advertising network called CPALead. A convoluted series of steps eventually led victims to a page where they were prompted to fill out surveys (with outrageous promises for high-value gift cards or other valuable prizes) or download and install software from a Web site named Gamevance, which publishes online games and promises players cash prizes for high scores.
In this case, the campaign uses a clearly deceptive Facebook app — actually, dozens of duplicate apps with slightly different names — that (when you click the Accept button in Facebook) spams a shortlink to all of the victim’s contacts through Facebook’s chat mechanism. The spam messages all imply that the link leads to some sort of modified photo of the message recipient, but lead into a feedback loop which tries to spread itself further by infecting the Facebook accounts of new victims. Then it displays the ads.
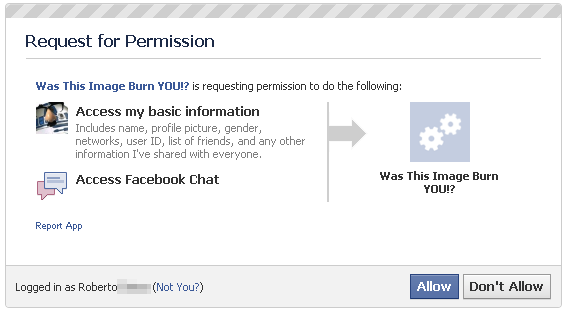
Clicking a shortlink leads a visitor first to a page on Facebook where they are asked to click a link to give the app permission to view their contacts. The app always has a slightly different name. Clicking “Allow” is a very bad idea.
Next, it redirects the browser to a page that rapidly displays a picture of a dog that has been modified to put a human’s face on its head. Hundreds of shortlinks being used in the campaign lead to different Web sites, but they all work in identical fashion.
Just to dissuade the curious Facebook users, here’s what the photo looks like.
Don’t click the links if you receive them.
However, almost too quickly, the page turns black and visitors are prompted to click a link in an online ad that comes from impressionlead.com. The ad includes the misleading title “Security Check” as though it were a part of Facebook’s security mechanism.
If you stumble into their trap and decide you want to back out of it, the purveyors of this scam employ another technique that’s pretty popular with the rogue antivirus crowd: The you-don’t-want-to-leave-now dialog box.
Yes, I’m sure. No, you cannot describe your spam-driven “special content” or “market research survey” as spam-free under the circumstances. Maybe they just mean there will be no cans of pink processed meat. That’s probably the only believable thing this company could say at this point.
The ads delivered by impressionlead.com prompt visitors (as in the previously reported campaign) to fill out surveys or install software from a Web site called Playsushi.
Unlike Gamevance, Playsushi’s domain registration information is not protected through private registration. That site just happens to be operated by a company called Future Ads LLC. The domain was registered to a street address in Irvine, CA, which also — in what must be a monumental and highly improbable coincidence — happens to be the business address of Gamevance, and another company called Trafficvance. Or, you know, not at all a coincidence.
Sound familiar? Yeah, I’m getting sick of this stuff, too. Same junk, different day.
The campaign really ramped up in the past two days. In the past two days, we’ve tracked more than 300 Internet domain names and more than that number of shortlinks that were involved in the campaign.
In the meantime, after we contacted the domain registrar that the operators of this sleazy campaign used to create most of the Web sites pushing the campaign, many of the domains have been taken offline.
As of this morning, however, more than 4.6 million people clicked the shortlinks that led to one of the Web sites currently involved in the campaign. New domains are being added as I write this.
We have no way to know how many of these people followed through and gave up personal information or installed game software as a result, but it’s fair to say that more than a few new users of Playsushi found their way into the gaming network through these maliciously-propagated links. Just as we did last month with Gamevance, we’ve now classified the Playsushi software as Adware and will remove it from our customers’ machines if they perform a full sweep of their system.
We’re also working more closely with the registrars used to create the domains as a way to proactively identify campaigns like this in the future, before they have a chance to spread themselves through social media. In particular, the people who run the co.cc service have been extremely helpful and we thank them for their responsiveness to this situation and other problems we’ve run across that involve domains registered through their service.
























Hi very interesting post!
Facebook is really getting bad about their phishing and fake apps.
great work! that’s why I use Webroot
I believe in Webroot wholeheartedly. YOU ARE MY TEAM ………………
no entiendo esto??
Have to be careful with what apps you install on facebook. For those who are not as savy as the author of this blog (great stuff btw) one thing you can do is when you are on the “grant permission” page for an app, click on the app’s name – this leads you to the page for the app, where you can see what other people are saying, how many monthly users they have etc.
If the page seems fishy or there are comments complaining that it’s spam, you know not to grant permission to that app.
Keep in mind though that the scam might be done by affiliates, and the CPA company might actually be good. I don’t think CPAleads is a scam company for instance.