 It’s been said that sunlight sanitizes almost everything it shines on. Beginning this week, and every week from now on, we’ll focus a concentrated beam on the rogue antivirus programs our support staff and Threat Research team have been working to remediate.
It’s been said that sunlight sanitizes almost everything it shines on. Beginning this week, and every week from now on, we’ll focus a concentrated beam on the rogue antivirus programs our support staff and Threat Research team have been working to remediate.
Rogues have a tendency to switch up their names, user interface, and other outward characteristics, while retaining most of the same internal functionality — and by functionality I mean the fraudulent tricks these forms of malware use to make it difficult for someone to identify them as malicious or remove them from an infected computer. It’s not as though the charlatans behind these scams (or their parents) ever made anything that was actually useful or desirable.
So for our inaugural Rogue of the Week post, we bring you notes on MS Removal Tool and XP Total Security, courtesy of Threat Research Analysts Brenden Vaughan and Stephen Ham.
MS Removal Tool
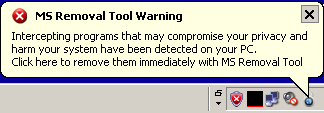
The most frequent infection this week has been the rogue security product MS Removal Tool, which is just the latest variant of the System Tool rogue. What a tool. Here’s what it looks like:
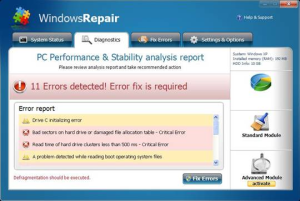
Support also mentioned seeing numerous cases of another rogue that goes by the names Windows Recovery, Windows Repair, or Windows Restore. All of these are “re-branded” versions of the same program.
None of these, obviously, are real Microsoft products, even though they use icons that look like the Microsoft Office logo:
It installs itself to the %appdata%Microsoft folder and is extremely randomized like other System Tool variants.
It also prevents all executable files from running once the rogue starts. However, if you run a sweep while Windows is in Safe Mode, we should be able to remove the infection.
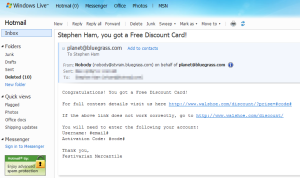
Stephen Ham found that links in spam email led to a drive-by download of MS Removal Tool. The spam messages offered a “Free Discount Card” for…something. The scammer kind of ran out of steam at that point. Thanks for sending the stuff directly to us, crimeware distributor guy. It makes our jobs a lot easier.
Technical details:
Rogue executable is installed to (where <random> indicates an unpredictable jumble of letters and numbers that changes each time someone installs the rogue on a computer):
C:Documents and SettingsAll usersApplication Data<random><random>.exe
Rogue sets start points from the following Registry location(s):
HKEY_CURRENT_USERsoftwaremicrosoftwindowscurrentversionrunonce
<random>= C:Documents and SettingsAll usersApplication Data<random><random>.exe
— Vaughan & Ham
XP Total Security
The other rogue security products our support team has primarily seen this week have been variants of the rogue with a randomized, 3-character file name. According to analysts working with the rogue, its user interface and name varies, depending on the operating system you happen to be running.
Here’s the short list of names the rogue’s authors have come up with for this scam:
| Windows XP | Windows Vista | Windows 7 |
| XP Anti-Virus | Vista Anti-Virus | Win 7 Anti-Virus |
| XP Anti-Virus 2011 | Vista Anti-Virus 2011 | Win 7 Anti-Virus 2011 |
| XP Anti-Spyware | Vista Anti-Spyware | Win 7 Anti-Spyware |
| XP Anti-Spyware 2011 | Vista Anti-Spyware 2011 | Win 7 Anti-Spyware 2011 |
| XP Home Security | Vista Home Security | Win 7 Home Security |
| XP Home Security 2011 | Vista Home Security 2011 | Win 7 Home Security 2011 |
| XP Total Security | Vista Total Security | Win 7 Total Security |
| XP Total Security 2011 | Vista Total Security 2011 | Win 7 Total Security 2011 |
| XP Security | Vista Security | Win 7 Security |
| XP Security 2011 | Vista Security 2011 | Win 7 Security 2011 |
| XP Internet Security | Vista Internet Security | Win 7 Internet Security |
| XP Internet Security 2011 | Vista Internet Security 2011 | Win 7 Internet Security 2011 |
— Vaughan






















I am a tech and I ran into the Windows Restore rogue on a clients machine. This was the first rogue I have run across that didn’t bring along the TDSS rooktit/bootkit infection. Does the family that this rogue belongs to not bring along the TDSS family like all the rest?
I also research malware and am a security consultant so you know where my curiosity comes from.
Josh
Usually, it’s a stub installer that brings down both TDSS and the rogue.
out of my league, interesting, just a pc trying to protect itself
My wife managed to download this jewel by clicking a link to watch a video on Facebook. The damn thing blew right past McAfee and Windows Defender. Regrettably, Spy Sweeper is now such a memory hog that it slows our computer to the point of hair pulling misery. Given this, it was disabled at the time.
The descriptions above are all cutesey and imply that this beast is simply an annoyance. On the contrary, it really corrupted stretches of the hard drive and deleted (or worse, stole) every file in our personal folder including spreadsheets, word docs, and thousands of family photos. True, it is easy enough to remove in safe mode but even the required system restore could not recover any of our personal files. Even now, our system isn’t right.
I’d like very much to choke the living shit out of the losers that wrote this program. It’s a shame these people don’t direct their energy toward world peace. War and crime would be history.
It would be helpful if each one of these notices were prefaced with at least the following information:
1. Does Webroot automatically identify and block such malware? If so, which versions.
2. If not, what should the computer user do, specifically, if such a malware pop-up is presented to him/her? Does the threat need to be removed? How must it be removed.
3. If a user installs the the malware, what should be done? Often, my wife or mother-in-law will tell me after the fact that they may have clicked on something that said they had a virus, for example. Often, I try to help, but must start with somebody’s vague recollection.
Most of us are pretty dumb when it comes to these things. Virus protection is not our full time job. The insider jargon that is sometimes used in these reports is meaningless to us. Keep it simple and direct, and we’ll love you for it.
Overall. High compliments for doing this report and keeping the customer in mind. That is why I’ve been a very satisified Webroot user for many years.
Steve Wynkoop
Denver, Colo.
i got this today from doing a google search for pictures, i think the webroot got the program out of my system but it was a scary thing should i do anything else to make sure it out completely
I got the XP Total Security infection earlier this morning, which happened after a Flash ad failed to load properly. It might have come through that, or a trusted website that was down earlier in the day, and might have come back with the infection ready for download on the website’s pages. I never click on spam mail links, nor have I opened .exe/.zip files in email.
Much thanks to Microsoft and Firefox 4 for letting this happen.
man i personaly hate total security a.k.a total destuction
it killed my previous computer and one more warning when it says in your desktop background save your files do not i repeat DO NOT save your files because you infect your next computer
Mi abogado me comento acerca esta pagina.
En verdad esta muy buena.