By Andrew Brandt and Armando Orozco
![]() A Trojaned application that displays a cutesy image of a 2011 calendar on an Android device’s desktop comes with a nasty surprise: The app sends text messages to a premium service that charges the phone’s owner money.
A Trojaned application that displays a cutesy image of a 2011 calendar on an Android device’s desktop comes with a nasty surprise: The app sends text messages to a premium service that charges the phone’s owner money.
As first reported by the Taiwan-based AegisLab, a single developer, which went by the name zsone, published the apps to Google’s Android Market. All apps from that developer were pulled from the Market today by Google, though only some of them appeared to contain the undesirable code.
We took a closer look at one of the apps, called iCalendar, that AegisLab was kind enough to share with us, and it didn’t take long to find the malicious code inside. Fortunately for most non-Chinese Android users, the premium numbers reportedly only work within China. We’re still testing to make sure that’s correct.
The application includes a unique image for each calendar month; Each time you tap the screen, the app displays the following month’s calendar image.The app is really badly programmed — when it runs out of the calendar images, it starts toggling through built-in system icons, and then eventually crashes. At least the coder behind this junk is consistent with other malware developers: QA really isn’t his strong suit.
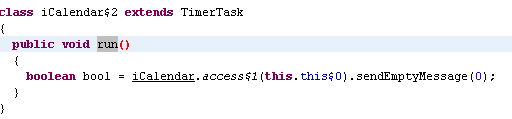
When you get to an image you want to set on the desktop, you long-press the screen to bring up a menu (in Chinese characters) that permits you to set that image as the background. However, after a preset number of screen-presses, or when a timer elapses, the app invokes a routine called sendSMS which, well, sends an SMS message to the premium service. Once the app has sent the SMS message, it sets a variable that precludes the app from sending it again from the same phone in the future.
Interestingly enough, the program’s creator also put in place certain protection methods to ensure that the program didn’t invoke that functionality on phones with certain phone numbers. If the device’s phone number equals one of six numbers in a hard-coded list, the abortBroadcast routine is called, and the messages don’t get sent.
At least one of these “abort” numbers is the default phone number that’s built into the Android development environment’s virtual device, so it won’t work on an Android instance running inside an unmodified Android developer’s kit.
AegisLab performed analysis on another app, called iCartoon, which contained similar functionality.
We’re adding detection for all of the zsone apps (as Android/Trojan.SMS.ZSones) in our next definition release — possibly as soon as this afternoon — because even though Google removed it from the market, the APKs may be floating around on Web sites or in Android app collections. It’s worth reminding all Android users that it’s always important to scrutinize the permissions an application requests when you install it. The price you pay for ignoring warnings that, for instance, a desktop image application wants to send SMS messages may be costly.