 Word from the AMR group last week was that there weren’t many changes from the previous week; Many of the same rogue antivirus previously reported in this blog continue to plague the Internet.
Word from the AMR group last week was that there weren’t many changes from the previous week; Many of the same rogue antivirus previously reported in this blog continue to plague the Internet.
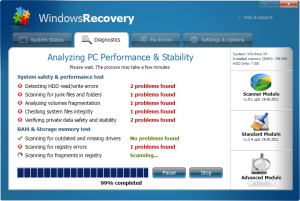
This week I decided to focus on a rogue that’s recently become a problem. It goes by the name Windows Recovery, though it’s also been called Ultra Defragger or HDD Rescue by other AV vendors. Bottom line, it’s still a fraudulent program which relies on deception and trickery to convince a victim to fork over some cash for a “fix.” It’s just not a rogue antivirus; Call it a rogue system utility. Fortunately, the damage caused by this rogue is actually relatively straighforward to manually clean up.
The gist of this rogue’s deception comes down to trying to convince the victim that their computer hard drive has experienced some sort of major malfunction. To accomplish this, the rogue does a lot of sneaky stuff: For instance, it flags all files on the boot drive with the “hidden” attribute, then uses registry tricks to prevent Windows from displaying any hidden icons.
It also moves any shortcuts that point to programs (both from the start menu and on the desktop) into the Temp folder, effectively neutering the utility of the Start menu. (We have a free tool that can fix this.) And it uses the Registry to disable the user’s ability to open the Task Manager, changes the system wallpaper (and prevents you from changing that wallpaper), and hides the entire desktop from view. (And we have another free tool that can fix this, too.)
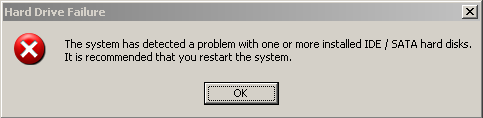
When I ran the Windows Recovery installer on my clean testbed, the program started up right away but sat idling for a while. After a few minutes, it started to display error messages. The dialog box, labeled Hard Drive Failure claims The system has detected a problem with one or more installed IDE / SATA hard disks. It is recommended that you restart the system. If you do restart, you’re in for a world of hurt.
That’s because meanwhile, in the background, the rogue (running from the Application Data folder under the All Users profile) marked all files on the C: drive as “hidden,” modified the registry so those hidden files would appear to vanish after a reboot, wiped out the Internet Explorer favorites, and moved all the shortcuts pointing to programs that were in the Start menu and desktop into nested folders within the %temp%smtmp folder.
After the reboot, Windows didn’t start itself up normally. The rogue had hidden everything, and kicked itself into “scanning” mode.
When it was finished, boy did it look like I was in trouble.
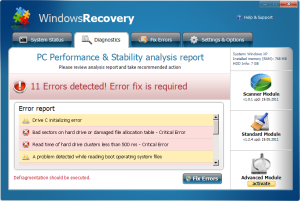
Among the messages the program displayed about the state of the testbed computer, Windows Recovery claims:
- Drive C initializing error (whatever that means — the computer booted up, after all)
- Bad sectors on hard drive or damaged file allocation table – Critical Error (Would be critical — if it were true)
- Read time of hard drive clusters less than 500ms – Critical Error (Really? It’s a problem if I have a hard drive that works too fast?)
- A problem detected while reading boot operating system files (Thanks for being so specific. Oh, and by the way, it managed to boot just fine, thankyouverymuch)
- Hard drive doesn’t respond to system commands – Critical Error (No thanks to your tampering)
- RAM memory temperature is 83°C. Optimization is required for normal RAM functi… (Remind me again: What’s the connection between the temperature of a memory module and memory optimization?)
- Boot sector of the hard drive disk is damaged – Critical Error (Also would be critical — and you wouldn’t be reading this — if it were true)
- 40% of HDD space is unreadable – Critical Error (No thanks to your modifications to the registry)
Screenshots here, and here, and here.
It goes on and on.
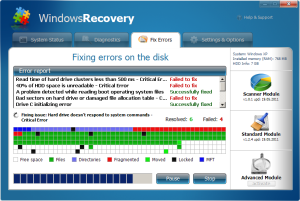
Next, it goes through the motions to make it look like it’s actually fixing some stuff. Really fancy animations and little squares that flash on and off in different colors, like a computer console from Star Trek, the original series.
Remember, nothing on the testbed system is malfunctioning, and any problems were caused by the rogue itself.
The program claims that it is capable of fixing some of the problems it alleges it discovered; Of course, the rest can be fixed for a low, low price: The one set by the rogue’s creators. An example of mean-spirited, coercive “sales” in its lowest form.
It’s possible to reverse most of the modifications the rogue made to the system manually. But you’ll have to use keyboard shortcuts to get it done. If you normally navigate by clicking folders or the My Computer icon, those things won’t be there. However, you can use keyboard shortcuts: hold down the Windows key and type E to bring up Explorer; Windows – R brings up the Run dialog. From the Run dialog you can launch any program.
To reverse the hidden files issue, you can just run the same command that Windows Recovery did, in reverse, from the Run dialog. The command to use is:
attrib -h "C:*.*" /s /d
Enter that command exactly as shown, and click OK. But you’re not done, yet.
Here’s the list of registry keys the rogue modifies, and the values it sets for those keys. If you’re comfortable modifying the Registry, you can revert these changes by switching the ones for zeroes, or vice versa. Just remember, you can do more damage to your computer and render it unbootable if you don’t know what you’re doing, so only modify the Registry if you are familiar with it.
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionExplorerAdvanced | Hidden | 0 HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionExplorerAdvanced | ShowSuperHidden | 0 HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionPoliciesActiveDesktop | NoChangingWallPaper | 1 HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionPoliciesExplorer | NoDesktop | 1
These keys are set by the rogue to disable the Task Manager.
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionPoliciesSystem | DisableTaskMgr | 1 HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionpoliciessystem | DisableTaskMgr | 1
These keys are also set by the rogue, and you can simply delete them.
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionPoliciesAssociations | LowRiskFileTypes |
{hq:/s`s:/ogn:/uyu:/dyd:/c`u:/bnl:/ble:/sdf:/lrh:/iul:/iulm:/fhg:/clq:/kqf:/`wh:/lqf:/lqdf:/lnw:/lq2:/l2t:/v`w:/rbs:
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionPoliciesAttachments | SaveZoneInformation | 1




















Thanks for this info. The first time through your article, I missed the detail about the shortcuts being hidden in the temp/sntmp folder. By the time saw it, I had deleted my temp folders. Might be good to mention that in the “how to reverse the modifications” section so other people don’t miss it. Also, might be good to mention rkiller or malwarebytes for the folks like me who find your article first on google.
Thanks again
Great info here, thanks. I helped someone who was taken over by “XP Total Security 2011.” It operated nearly identical to the Windows Recovery Rogue discussed above. It hid programs, files, and desktop, disabled task mgr, and even forced restart command when trying to download WR online. Running the manual commands and registry key revisions allowed me to install WISE from a disc in safeboot with networking, and use task mgr to continuously end the rogue’s process while installation proceeded. Note, this XP Total Security rogue took over his ESET Smart Security 4 software and Firewall. We uninstalled that, ran a full scan, which caught ~15 various rogues with ~80 items quarantined. Amongs the variety of fake antivirus rogues and trojan downloaders caught, there was a manipulated adobe file, and XsscWvvgUnQhD.exe that I think was the ringleader of this gang. He’s quite content now that it’s all fixed up – thanks so much for your expertise!
My girlfriend’s PC got hit with this, but it went under Windows XP Recovery instead of just Windows Recovery. Unfortunately it came bundled with the TDSS rootkit. I was able to remove the rogue but not the rootkit, which would launch IE in the background every chance it got.
I tried tdsskiller from Kaspersky and that didn’t want to run on the system. Other rootkit programs wouldn’t find it either. Another symptom I couldn’t get rid of was the Google redirects to random sites in Firefox.
Considering this was the third virus my gf got in the past month, I decided to install Ubuntu for her.
TDSS is bad news. It interferes with low level hooks to the kernel and filesystem that we use to remediate infections. It’s causing headaches for every AV vendor.
I have a Vista version of this rogue on a clients machine. You mentioned that it asks if you would like to restart. My client said they were surfing on google (so it could have been a part of the OBL attacks as of late) and the laptop suddenly just restarted without user intervention, when it restarted the rogue just took over. Is the TDL3 or TDL4 versions of the TDSS rootkit involved with this rogue? When I find out if you guys don’t know I will post the results for you guys.
Various forms of TDSS/TDL rootkits seem to correlate with rogue infections; As TDSS seems to be as much a rootkit as a delivery mechanism for other malware, it’s likely the case that the rogue is being delivered by TDSS in some cases, not the other way around, but it can happen either way.