This week, we turn our attention temporarily away from the never-ending stream of rogue security products on the Windows platform and take a closer look at the Mac OS analogue, MacProtector (aka Mac Security, Mac Defender, MacGuard, and–if history serves–soon to be many, many other names).
This week, we turn our attention temporarily away from the never-ending stream of rogue security products on the Windows platform and take a closer look at the Mac OS analogue, MacProtector (aka Mac Security, Mac Defender, MacGuard, and–if history serves–soon to be many, many other names).
There’s been a lot of press coverage of these rogues — including a video blog post by us — in the past few weeks, so we thought it was high time we took a deeper dive.
Even though Webroot doesn’t offer an automated removal solution for the Mac, there’s good news for most Mac users — with only a little bit of effort, it’s fairly rudimentary to simply delete the rogue .app and be done with it. In this case, the Activity Monitor (Apple’s GUI process monitor, located by default in the Utilities folder inside the Applications folder) is your best friend.
The program appears as a stub .mpkg installer, which means that the application that installs the program isn’t a container with the full program stuffed inside. The installer drops an app named avRunner.app into the Applications directory, then executes it.
avRunner.app simply downloads the full version of the rogue .app from a Web server (in our case, the file originated from the IP address 86.55.210.102).
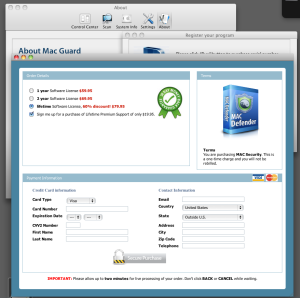
As with most rogues, the developers come up with names faster than the program’s UI gets updated, which makes the creators of the program look extremely dense. Here you can see the program running one window labeling itself as Mac Guard, with another window in the foreground that contains a bogus box-shot labeled Mac Defender, and a line of text beneath that box shot which says “You are purchasing MAC Security.” To bowdlerize the immortal words of Blink 182, what’s your name again?
Having seen my share of rogues over the past several years, I have to tell my Mac-using friends you ain’t seen nothing yet. This rogue is kid stuff compared to the rogues that infect Windows boxes.
For one thing, there’s no Registry in the MacOS, so the rogue can’t readily make debilitating changes to the way the operating system functions. On Windows boxes, rogues typically are accompanied by rootkit drivers and registry modifications that, in essence, prevent you from doing almost anything useful on the infected computer.
While the Mac rogues — like their big-city cousins, the Windows rogues — try hard to put on the airs of legitimacy, MacProtector (et al) ends up with egg on its face, just as the Windows rogues so often do. The scam is the same, but so are the stupid errors in these hastily constructed scams.
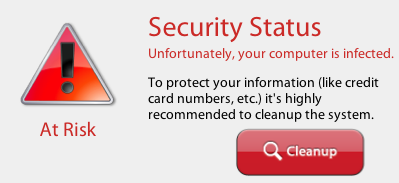
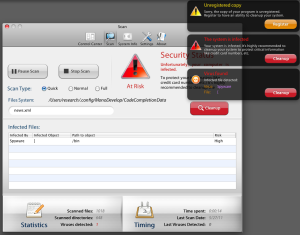
Each variant we’ve looked at works in almost identical ways: The installer pulls down and launches the app; The app begins “scanning” almost immediately, and soon after scanning begins, reports that “The system is infected” with, uh, something. They’re making it all up as they go along anyway, so it doesn’t really matter what they call the malicious files.
I was actually impressed to see that the program includes its own built-in process monitoring tool. Of course, you can’t actually use it to kill the rogue, but it works with any other running app or service on the machine.
The program even has some settings you can modify, including the Scan Type (sadly, there’s no option for non-BS scan) and options that let you disable automatic execution on startup.
We also watched the program, after it sat idling for about 12 minutes on the infected computer, spawn instances of the Safari browser where it opened pages to such tasteful and family-friendly Web sites as gay.porn.com and buy-viagra-now.net in the background. I guess that’s supposed to push you over the edge, to convince you that you’re infected with something bad. (Your computer is infected, just not with what they’re claiming.) Stay classy, rogue antivirus guys.
The scam is that the program continuously throws warning messages onto the desktop while repeatedly prompting you to make a $100 purchase for a “license key.” The whole past week, the purchasing window loaded from the IP address 91.213.217.30. That IP has been blacklisted in our definitions for its involvement in Windows rogue activity, so if you’re able to localhost it in your Hosts file, be my guest. You won’t be missing out on anything important if you do.
I’m quite impressed with the backstory fiction they’ve invented for their rogue. It would actually be quite compelling if it weren’t a steaming pile of horse puckey: 250 specialists in more than 10 countries, working around the clock, all just to protect your CREDIT CARD NUMBERS, ETC. Yeah, right.
Now, as for the fix, you’re in luck: Launch Activity Monitor, find the name of the rogue in the list of running processes, then click the little stop sign icon to Force Quit the rogue. Once that’s done, delete the .app from the Applications directory and you’re golden.
Remember, Mac users, Apple won’t give you any support if you get infected (after all, it’s not an Apple software vulnerability that’s being exploited), so you’ll have to do this all by yourself.