 The criminals who push rogues at the world don’t really care about the reputations of the ISPs or Web hosting services they abuse. They leap from free service to free service until they’ve thoroughly worn out their welcome and, in some cases, destroyed the reputation of the service they abused. But they have behaved in one predictable way over the years: They’re stingy, and won’t pay for anything unless it’s absolutely necessary, despite the fact that they’re raking in cash by the boatload.
The criminals who push rogues at the world don’t really care about the reputations of the ISPs or Web hosting services they abuse. They leap from free service to free service until they’ve thoroughly worn out their welcome and, in some cases, destroyed the reputation of the service they abused. But they have behaved in one predictable way over the years: They’re stingy, and won’t pay for anything unless it’s absolutely necessary, despite the fact that they’re raking in cash by the boatload.
But that seemed to change this week when we saw a number of Web sites pop up on the radar. The sites employ the now well-worn scam of pretending to be some sort of video streaming service. In this case, they pretended to be a porn site, but the most surprising part was not what was hosted, but where: Amazon’s Cloudfront hosting service ended up, temporarily for a few hours, serving up malicious Web pages. Amazingly, it seems they actually paid for hosting instead of just stealing it.
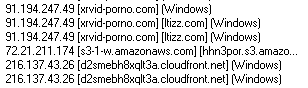
Amazon shut the sites down quickly, but before they did, we visited one site called xrvid-porno.com. The page isn’t exactly family friendly, but the gist of the scam is that that page eventually redirected the browser to a server inside of Amazon’s cloud hosting service, and that’s where the trouble began.
The Amazon-hosted page was located on a server in a colocation facility in Dallas-Fort Worth, Texas, but the pages themselves were written in Russian, which indicates that these scammers (who have been based in Russia for some time) are turning on their own countrymen to advance their criminal enterprise. With the help of a free Web proxy, I made the browser on my test system appear to come from a Russian IP address, and in return, the Web site delivered a series of exploit files which eventually resulted in the computer becoming infected with a rogue.
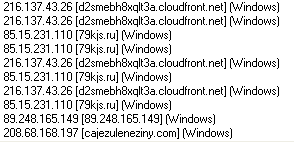
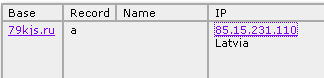
None of the really malicious code or content was actually hosted within Amazon’s servers. Instead, the fake porno site, hosted on Amazon, called scripts from another server which was actually located in the network belonging to Latvenergo, the Latvian national energy company. The domain from which the malicious scripts originated, 79kjs.ru, points to an IP address inside of Latvenergo’s network, and remains active and serving malware as I write this.
Those scripts included one of the many varieties of browser exploit kits, and the exploit kit which ran decided that the most efficient method of infecting my test machine was to push down malicious PDF files to the browser, though it also tried a number of other browser exploits before settling on this one.
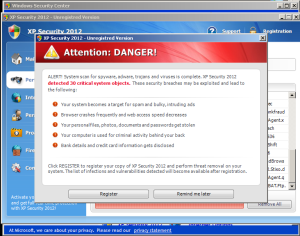
Those PDFs, running in an older, more vulnerable version of the Adobe Acrobat Reader, contained just enough scripted code to force the browser to yet another IP address, physically hosted in the Netherlands, where the rogue application was hosted. The file which came down the pipe calls itself XP Security 2012.
It also brought along a friend: A ransomware application which hijacks the desktop with an all-black screen (hiding the desktop icons), kills Explorer, and makes a demand for payment of 500 rubles in a window that looks like a Windows BSOD screen.
The best part of this ransomware “warning message” is its internal contradiction. Roughly translated, the message threatens (emphasis mine):
Computer is Blocked!
Your computer is blocked for viewing, copying and
dissemination of video materials containing elements of pedophilia
and rape of children. In order to remove the block You are required to
pay a fine in the amount of 500 rubles to the (telephone) number
8-965-265-90-84. In case of payment of the sum equal to or
greater the amount fine there will be an unblock code on the receipt.
You’ll need to enter the code in the lower portion of the window and
press the “unblock” button. Once the block is removed you
must delete all materials containing elements of rape and
pedophilia. If you do not pay the fine within 12 hours, all
information on your personal computer will be permanently
deleted and the case will be sent to court for investigation in accordance to
chapter 242 part 1 of the Penal Code of Russian Federation.Rebooting or turning off of the computer will lead to
prompt removal of all data, including the
operating system and BIOS, without ability of further
restoration.
Wow, really? You’re going to delete the evidence, then send the case in for prosecution? I don’t know anything about Russian Federation cybercrime law, but if I had been committing a crime, that sounds pretty good to me. Bring it on! Also, I’d like to see you try to wipe the BIOS out of its firmware hidey-hole. The only thing they didn’t threaten their software would do was remove all the screws from the PC. As Bugs Bunny might say, what a maroon!
Fortunately for me, I had Process Explorer running in the background, and could alt-tab to that task manager-like tool (which the ransomware had simply shoved into the background) and kill the ransomware process.
Amazon should be credited with shutting down the site within just a few hours of it appearing online, but the entire incident stands as a cautionary tale to Web hosting providers or ISPs: No matter how large you are, you’re not invulnerable to the threat of malware distributors abusing your service.
(Thanks to Timur Kovalev on the Threat Research dev team for the ransomware translation)





















We got the russian warning on our exchange server. We are able to see the task manager. What is the process we need to kill?
Is there a registry ky as well to change after that?
In Soviet Russia hacker sues you! 🙂