![]() An unusual family of Trojans, apparently of Chinese origin, engages in rootkit-like behavior which seems designed not to hide the presence of the malware on an infected system, but to misdirect or confuse a technical person who might be using system analysis tools on an infected computer.
An unusual family of Trojans, apparently of Chinese origin, engages in rootkit-like behavior which seems designed not to hide the presence of the malware on an infected system, but to misdirect or confuse a technical person who might be using system analysis tools on an infected computer.
The Trojans all originated from a server operated by a free Web host in China, and each sample we tested sent profiling data about the infected system to a command-and-control server located on yet another free Web host, also located in China. It appears to have capabilities to receive instructions to download other components, and it scans the system for antivirus products commonly available in China, including products made by Qihoo 360, China’s largest homegrown antivirus company.
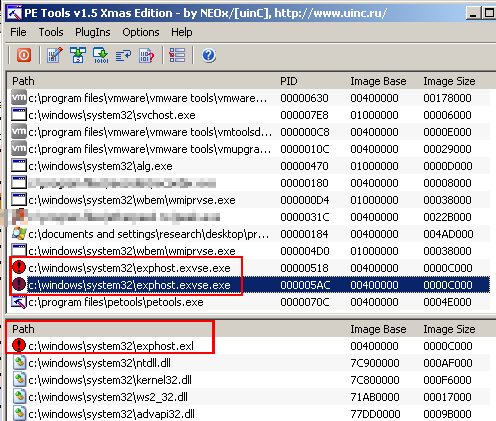
But the most interesting aspect of the Trojans was how it managed to fool most of the free tools someone might use to monitor running programs. The Trojan shows up in the list of active programs, but when that list includes a full path to the running executable, that path points at a nonexistent file supposedly in another location.
The files were executables, but had the .rar extension of a compressed file. Renaming the file with the correct extension reveals the malware application’s distinctive icon of three interlocking 3D cubes.
The malware installs itself as a Windows service, which ensures that it will run after a reboot. The service names are pseudorandom, and the malware also randomizes the text description of the services, but the randomization technique is also kind of unique: They always use the same root phrase for both the name and description, but the malware inserts random letters and numbers somewhere in the middle of these two items. The name, for example, always started with the phrase DHCP Service (the real Windows service that handles DHCP is named DHCP Client) but, in one case, the name was randomized to DHCP service fo2344r and in another to DHCP servrtrt465466565ice for — the random characters can occur anywhere in the name. Likewise, the descriptions were Network address tran4442slation for virtual and Network address translatio565n for virtual, respectively. Clearly, English comprehension is not a necessary skill for these goofballs.
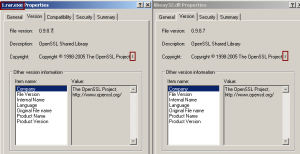
The malware’s properties sheet claims that the Trojan is the OpenSSL Shared Library, version 0.9.8.7, but the only problem is that shared libraries don’t typically take the form of an executable; In this case, the real, legitimate OpenSSL Shared Library is normally distributed to Windows users in the form of files named ssleay32.dll or libeay32.dll. I’ve shown both, next to one another, for comparison. OpenSSL is common and fairly widespread, installed by many applications which need to communicate securely with a server elsewhere. This malware’s mimickry of the properties data even includes the (possibly unintentional) pipe character that appears in the real OpenSSL library’s properties. All of this is just another item in the social engineer’s bag ‘o tricks.
As you can see from this screenshot, the malware sample copies itself into the root of the Program Files directory, but then tricks Process Explorer into displaying the wrong path, falsely claiming that the malware is running from c:windowssystem32exphost.exe — a file that doesn’t exist on my testbed.
It took some time for the malware to begin doing something; After several hours of the Trojan idling on the testbed, periodically checking in with its command-and-control server, it began to repeatedly try to download something from several different Web servers that, as far as I can tell, are all offline.
In addition, the malware sample started sending IPv6 “ping” packets, at the “hey, look at me, I’m calling attention to myself” rate of 2975 pings per second, at the IP address 59.34.197.232 — the CnC server hosted on China Telecom’s network used by one of the malware samples from the same set (and apparently a source of spam and other nastiness, because the IP address is blacklisted by multiple providers of spam-source blacklist services). This seems to be a no-brainer IP address to blackhole on your local network.
The rapid pinging causes free tools like NetworkMiner to crash after a while, but it has no effect on the internal network monitoring tools we use. In the end, setting up a simple “accept no ping request or ping reply packets” rule filtered out the junk and let us observe the rest of the network traffic, interspersed between a flood of irrelevant data.
Another blackhole-worthy IP address is 183.60.132.157, the other CnC address (and the IP address assigned to the malware source URL, vip.hyaiwl.name). The malware checks in with this address about once every ten seconds. And the malware SYN-floods the IP address of 112.91.169.232, a China Unicom address which itself is blacklisted in several lists as a result of misbehavior.
Unfortunately, the poor coding practices by the sample’s author cause additional problems: A memory leak in the malware sample slowly saps system resources until Windows starts issuing “low on memory” errors. The constant pinging seems to exacerbate the problem. On one testbed, where the malware was allowed to run overnight, by morning it had swelled from using a mere 50MB of RAM to more than 485MB of system memory. Nice job, malware dork.






















I received a security message indicating that my computer was infected with RDN/Trojan.worm! Should I be concerned is someone fishing?
Hello, Kathy!
It sounds like a junky/scam popup, but you can never be too lax when it comes to your safety.
Feel free to reach out to our Support Team and they’ll be happy to conduct a review of your Computer.
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send a Support Ticket
Best,
Josh P.
Digital Care Coordinator