By Mike Johnson
Several weeks back, I was presented with a group of snapshots from an active BlackHole Exploit Kit 1.2 Control Panel.
As with other toolkits I’ve seen in the wild, this one has all the makings of some real bad medicine. The authors have yet again gone to the trouble of making this toolkit incredibly easy to use and widely available for a price. Just a little unsavory web hosting in a country with few or no diplomatic relations and off to the races they go.
It appears this toolkit is configurable in both Russian and English, making one wonder its true origins.
I’ve slowly tracked URLs accompanying this toolkit and watched it dish out some very widely undetected malware, such as:
Information Stealing/Banking Trojans:
SpyEye
Zeus
Carberp
Mebroot Rootkit
Another more popular rootkit we’re seeing very widely on the Webroot realtime watch is: vSirefef.B/Zero-Access.
BlackHole toolkit preys on only two items in a user’s machine:
1) Unpatched operating system exploits
2) Internet browsers, add-in and plugin exploits such as Adobe and Java Software
Here are some of the known exploits the kit can execute on a victim’s machines.
Windows Operating Systems:
CVE-2010-1885 HCP (Microsoft Windows Help and Support Center in Windows XP and Windows Server 2003)
http://technet.microsoft.com/en-us/security/bulletin/MS10-042
CVE-2006-0003 IE MDAC
http://technet.microsoft.com/en-us/security/bulletin/ms06-014
Adobe Software:
CVE-2008-2992 Adobe Reader util.printf
CVE-2009-0927 Adobe Reader Collab GetIcon
CVE-2007-5659 Adobe Reader CollectEmailInfo
Java Software:
CVE-2009-1671 Java buffer overflows in the Deployment Toolkit ActiveX control in deploytk.dll
CVE-2010-0840 Java trusted Methods Chaining Remote Code Execution Vulnerability
CVE-2010-0842 Java JRE MixerSequencer Invalid Array Index Remote Code Execution Vulnerability
CVE-2010-0886 Java Unspecified vulnerability in the Java Deployment Toolkit component in Oracle Java SE
CVE-2010-1423 Java argument injection vulnerability in the URI handler in Java NPAPI plugin
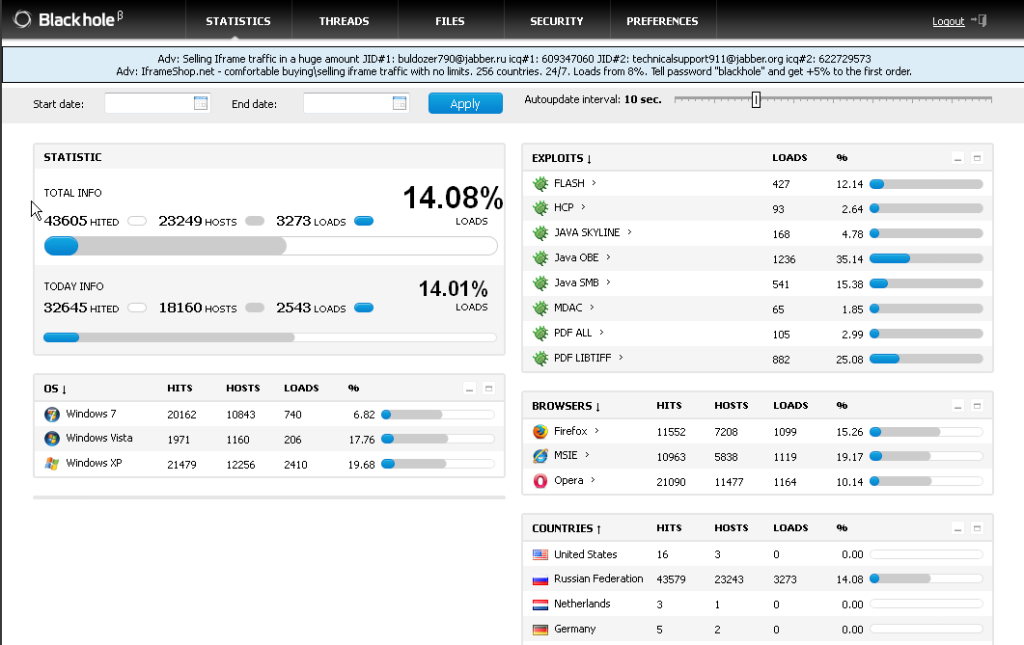
The basic view the bot controller has is of the statistics page, which should indicate why I listed some of the expoits this toolkit is using. Not surprisingly, for as young as the kit is, you can see that both the Java and Adobe softwares are exploited far more than any others.
I’m sure some think they are safe using a browser other than Internet Explorer but it appears from this image there isn’t alot of difference in how this toolkit has behaved between the three browsers it’s touched.
As the authors have made this toolkit easy to use, they have also made it easy to maintain a low detection rate on the binaries by using an antivirus scanning service which does not share any binaries collected with the AV industry.
The easy-to-read statistics page make it simple for the controller to view and monitor how well or poor the current bot is doing — how many operating systems it’s infected, what type of operating systems were infected, and in which countries they’re located.
Image 2 is the preference page where the user of the control panel can make quick changes to the toolkit’s delivery methods or the binary state via virus scan.
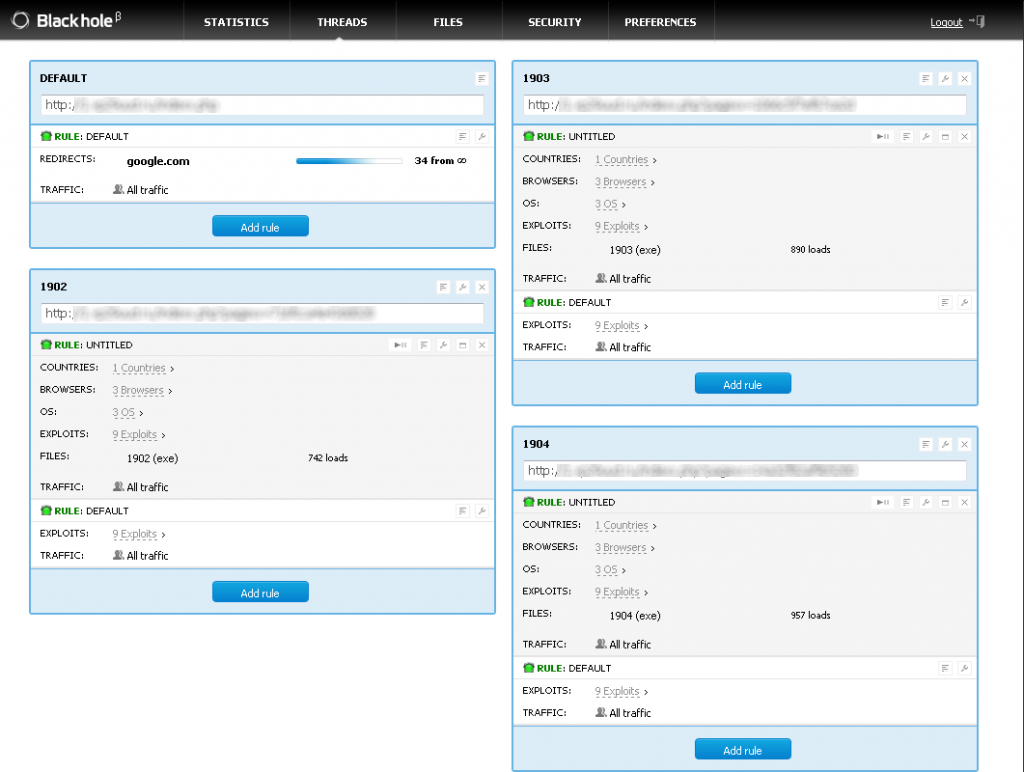
The below images show how easy it is to see that the authors had some form of longevity in mind by giving the controller to ability to set any type of rule to avoid quick detections on the delivery points, along with quick means to replace any file at any given time.
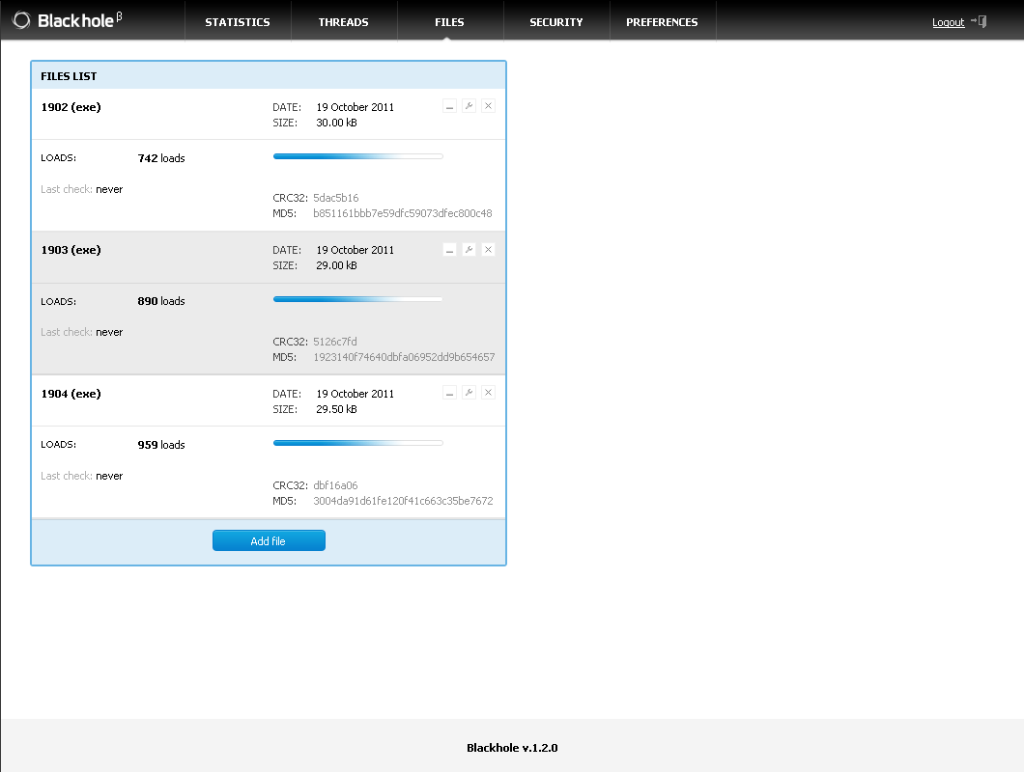
Blackhole uses custom file encryptions to assist in avoiding detections but oddly enough, they have chose to use some static file naming for the actual files, as they would exist on a victims machine.
So far Ive only encountered four static names:
contact.exe
readme.exe
info.exe
about.exe
calc.exe
This glance at the Blackhole Toolkit confirms the dependence on outdated operating systems and outdated software in general, in order for it to exist efficiently.








so does Webroot stop this, just asking.
We do protect against the Trojans we’ve seen this kit dish out. However, there are always new variants being discovered so as soon as we find them we add them to our threat intelligence network and you are protected.
I’ve been subscribed to the RSS feed for a couple of months now, and I’m impressed by the level of content you guys put out.
Thanks Webroot!