Security researchers from Webroot have intercepted two currently live client-side exploits serving malware campaigns that have already managed to infect over 20,000 PCs across the globe, primarily in the United States. Based upon detailed analysis, it can be concluded that both campaigns are launched by the same cybercriminal.
More details:
Using the BlackHole web malware exploitation kit, the malicious attackers are currently serving explots to tens of thousands of unsuspecting end users.
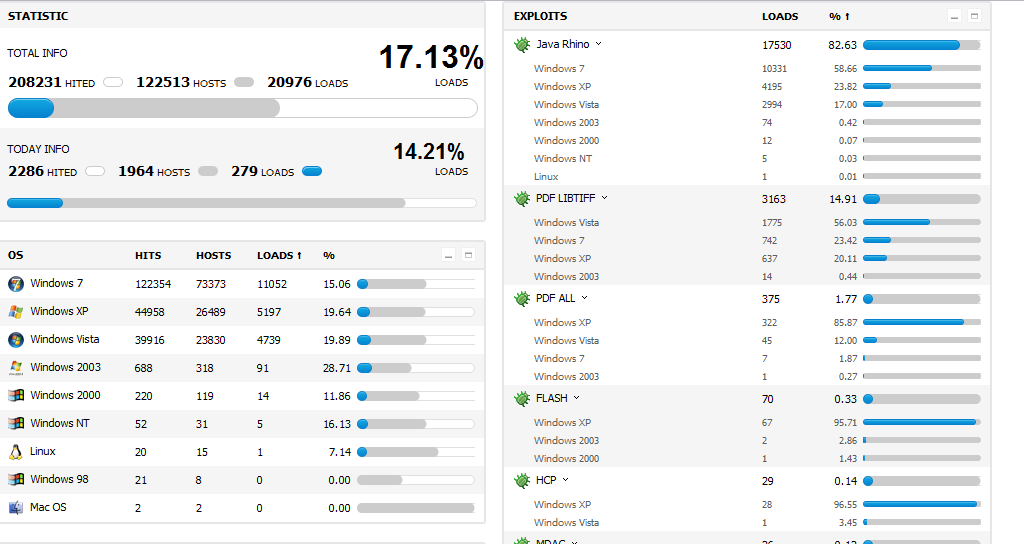
As you can seen in the screenshot, they have already managed to infect 20,976 hosts. 17530 hosts were successfully exploited using the Jave Rhino exploit, 3163 hosts were exploited using the PDF LIBTIFF exploit, 375 hosts were exploited using the PDF ALL exploit, 70 hosts were exploited using the FLASH exploit, 29 hosts were exploited using the HCP exploit, 26 hosts were exploited using the MDAC exploit, and 23 hosts were exploited using the Jave OBE exploit.
Screenshot of the affected browsers and exploited countries:
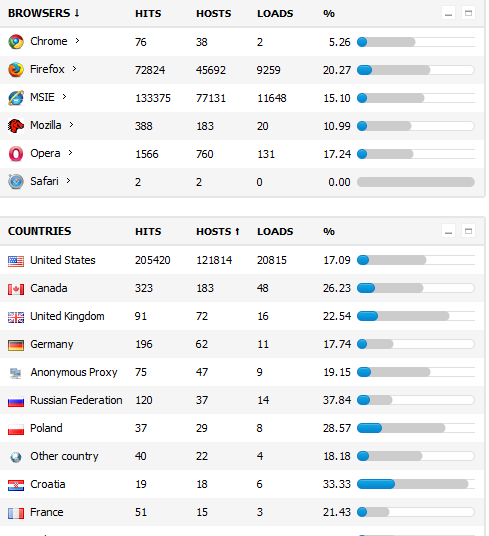
As you can see in the above screenshot, exploitation of vulnerable Internet Explorer versions tops the chart with 11,648 successful infections, followed by Firefox with 9259 infections, Opera with 131 and Chrome with just 2 infections. The majority of victims from the first campaigns are primarily based in the United States.
Cybercriminals often hijack traffic from developed countries, whose Internet users have a high purchasing power compared to users of developing countries.
Client-side exploits are served from the following URLs:
hxxp://178.18.243.177/main.php?page=691bdc57bceadabf
IP Information for 178.18.243.177
Germany Karlsruhe Inline Internet Online Dienste Gmbh, AS31147
Associated MD5s:
990af3738af00cd43b7f67e04e6cd869
94652039cb8cae5595a93f1dd40561cd
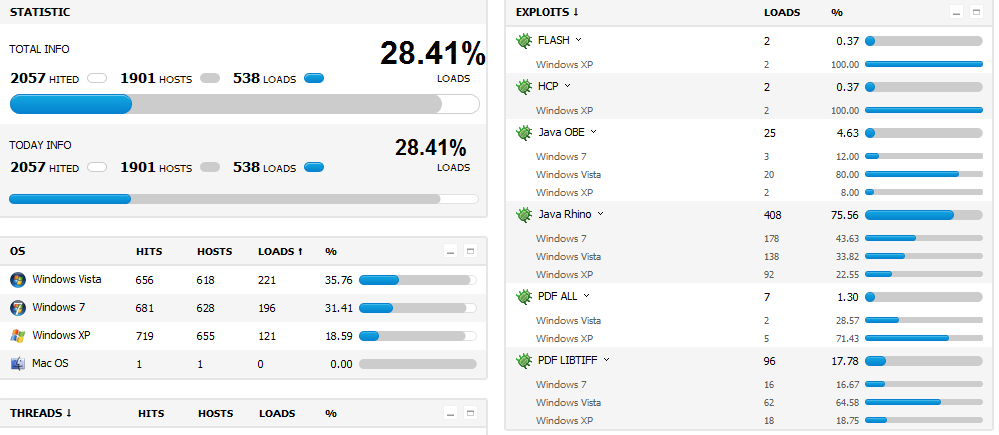
The second campaign is once again using the BlackHole web malware exploitation kit for serving client-side exploits to unsuspecting victims, and has already managed to infect 538 hosts from across the globe. Malicious cybercriminals have already managed to exploit 408 hosts using the Java Rhino exploit, 96 hosts using the PDF LIBTIFF exploit, and 25 hosts using the Java OBE exploit.
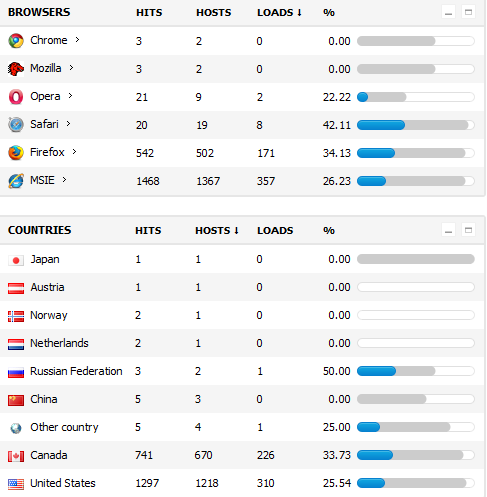
Which browsers were most susceptible to exploitation? According to the BlackHole statistics, 357 infections took place on Microsoft’s Internet Explorer browser, followed by another 171 on Mozilla’s Firefox, 8 on Safari, and 2 on Opera. Once again, the majority of victims are located within the United States.
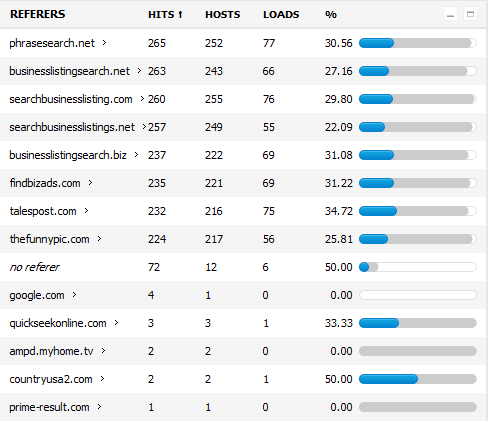
How are the malicious attackers delivering their malicious payload? Pretty simple in this case — by embedding malicious iFrames on questionable web sites and underground search engines, as you can see in the screenshot above, showing where the majority of the traffic is coming from.
IP Information for 81.17.24.93
Switzerland Zurich Private Layer Inc, AS51852
End users are advised to ensure that they’re not susceptible to client-side exploitation, by checking that they’re not running vulnerable versions of popular software and browser plugins.
Webroot’s security researchers will continue monitoring these campaigns, to ensure that Webroot SecureAnywhere customers are protected from the malicious payload served.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.







Ddanchev,thank you for that report.It is indeed a sad news to many internet users to hear about this malicious attackers.Many people are not aware of this hijackers. One to reduce this threat is to spread the information about the hijackers activities to many news site and social media ,
THANK YOU GREEN HORNET(AKA- Webroot)
I quit using IE 2 months ago and started using chrome, 100% imorovement. I USE NO PLUG INS.
KEEP UP THE GOOD WORK!!!
So is Chrome that much better than IE or FOX?
Excellent post however I was wondering if you could write a
litte more on this subject? I’d be very thankful if you could elaborate a little
bit more. Bless you!