The ever-adapting cybercrime ecosystem is constantly producing new underground releases in the form of malware loaders, remote access trojans (RATs), malware cryptors, Web, IRC and P2P based command and control interfaces, all with the clear objective to undermine current security solutions.
Continuing the “A peek inside…” series, in this post I will profile a malware loader recently advertised within the cybercrime ecosystem , namely, the Ann Malware Loader.
Some of the key features of teh Ann Malware Loader include:
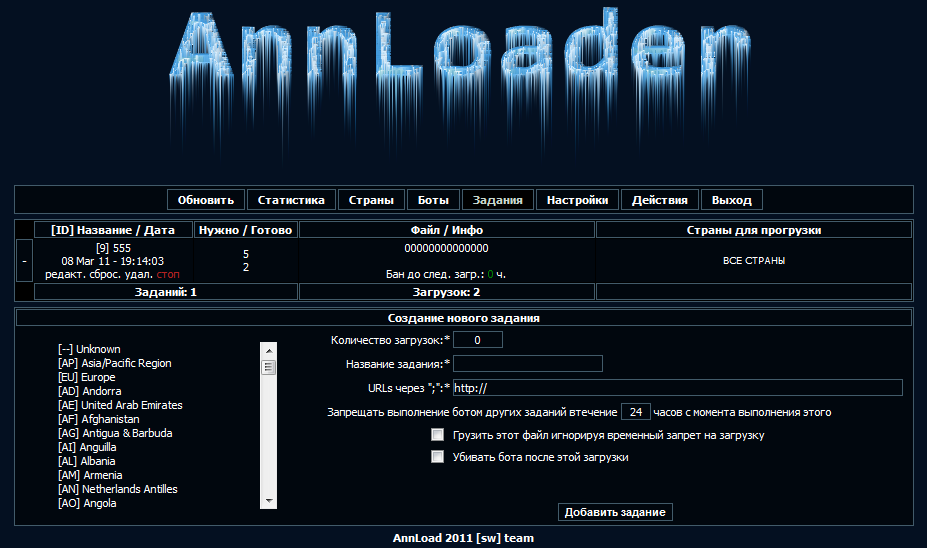
- Supporting tasks: as it downloads, such as country, etc.
- The sequence of tasks
- Ability to edit and rearrange every way the job sits.
- The small size of the build, only 14 kb
- The program is written on pure API
- Ability to control loads on the bots, and selection in the white zone
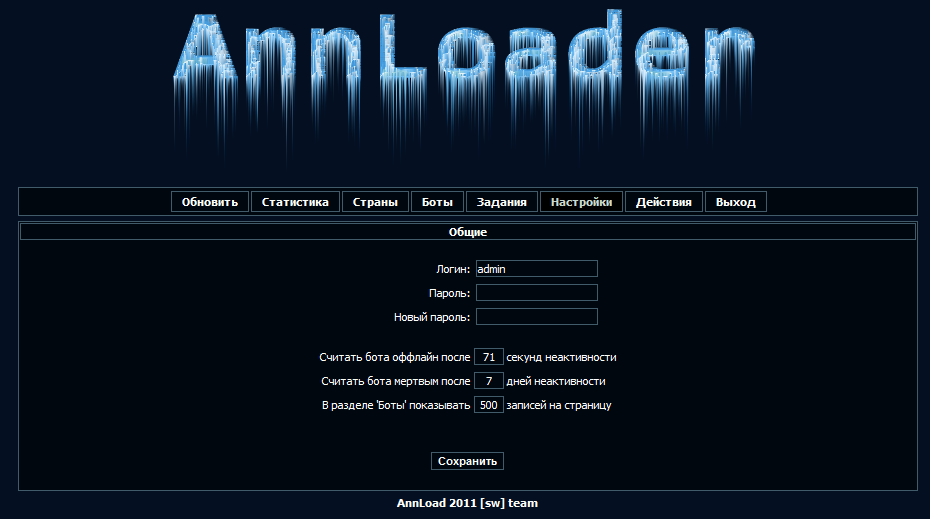
- AnnLoad got stable, fast, easy, secure admin panel.
- The control panel does NOT even store your password in the config, only cache!
- The algorithm AnnLoad does not contain anything that could interfere with the crypt (service mode, tls, etc …)
The flexible pricing list:
- Minimum: Loader no free upgrades – $ 330.
- Standard: Loader + months of free upgrades – $ 380.
- Bronze: Loader + 3 months free upgrades Free rebild + 1 – $ 480.
- Silver: Loader + months of free updates + 2 free rebilda – $ 530.
- Gold: Loader + free upgrade forever + 5% discount on our products + 5 free rebildov + module to choose a gift – $ 630.
- Platinum: Loader + Update + free 25% discount on our products rebildy + free + 2 modules to choose a gift – $ 725.
- Diamond: Loader + Free updates + Free unlimited rebildy without limitation + 30% discount on all our products + plug-ins as a gift. = $ 825
- Upgrades – $ 35-85 (depending on the importance of the upgrade).
- ReBuild (change URL) – $ 35.
- Sources – discussed separately.
- New function – is discussed separately.
- Fxp (ftp)
- Total commander (ftp)
- Filezilla (ftp)
- Wsftp (ftp)
- Mozilla Firefox (web, forms)
- Opera (web, forms, ftp)
- CuteFTP (ftp)
- Qip2005 (icq)
- Qip2010 (icq, eml)
- QipInfium (icq, eml)
- The bat (eml)
- RDP (rdp)
- Google Chrome (web)
- Safari (web)
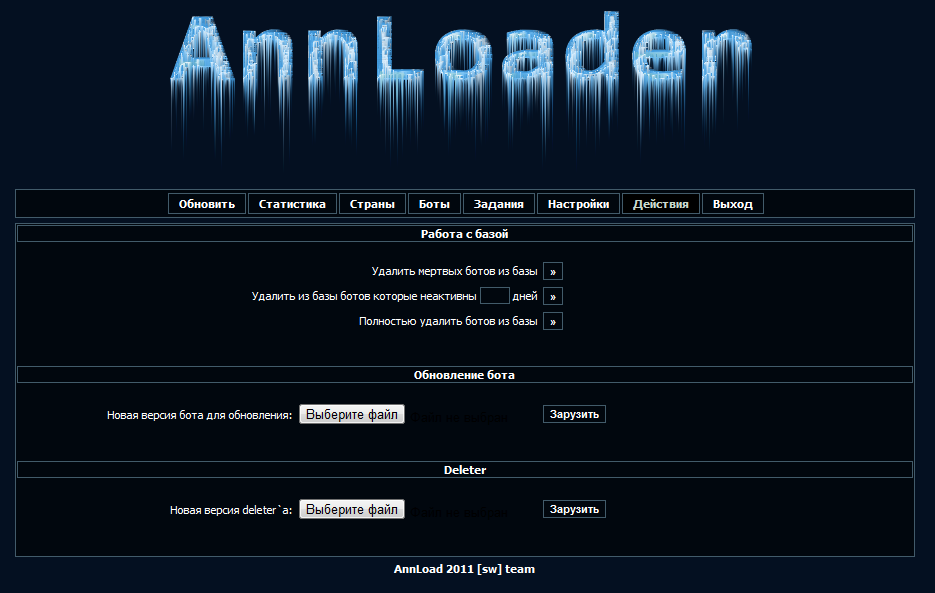
Screenshots of the Ann Malware Loader in action:
What’s particularly interesting about the Ann Malware Loader is the fact that it comes with an EULA agreement, emphasizing on the fact that the malware loader is to be used for testing purposes only. By doing this, the key coder behind this underground release is forwarding the responsibility for its uses to his customers.
Moreover, thanks to its modular nature, the malware author is offering custom made modules allowing potential cybercriminals to hire a malware coder for a specified amount of money.
Webroot’s security researchers will continue monitoring the development of this malware loader to ensure that Webroot SecureAnywhere customers are protected from it.
Related posts:
- A peek inside the Smoke Malware Loader
- A peek inside the uBot malware bot
- A peek inside the PickPocket Botnet
- A peek inside the Umbra malware loader
- A peek inside the Cythosia v2 DDoS Bot
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.