What happens when a host gets infected with malware? On the majority of occasions, cybercriminals will use it as a launch platform for numerous malicious activities, such as spamming, launching DDoS attacks, harvesting for fresh emails, and account logins. But most interestingly, thanks to the support offered in multiple malware loaders, they will convert the malware-infected hosts into anonymization proxies used by cybercriminals to cover their Web activities.
In this post, I’ll profile a newly launched service, offering thousands of malware-infected hosts as Socks4 and Socks5 servers for anonymizing a cybercriminal’s Web activities.
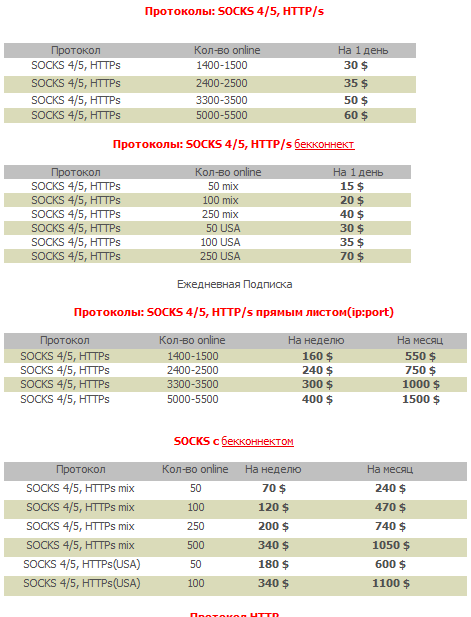
Most recently advertised as ProxyBuy, the service, in operation since 2004 under different names/domains, offers access to thousands of malware-infected hosts, now converted to Socks4 and Socks5 servers — back connect supported — thanks to the overall availability of this feature in the majority of today’s modern malware loaders.
Welcome to the website proxy Proxybuy . Founded in 2004, Proxy Service to quickly and securely won a stable position with a reputable service. Here you can buy a proxy http or https , buy socks excellent performance, order a subscription for a week or a month. Our paid proxy lists are used for different types of Internet businesses, as well as for “home use”. All we provide lists of proxy – anonymous and private. Good support high-speed operation. Quality you can check out the section Proxy checker . Buy proxy lists, or buy the socks we just. Simply select a Desirable your tariff and apply our specialist via ICQ , E – mail , skype or phone.
The prices vary, based on the number of requested Socks4/Socks5 servers. For instance, a potential buyer can purchase 1400-1500 socks servers for the price of $30. Naturally, the malware-infected hosts don’t keep any logs, making them the perfect tool in the arsenal of a malicious attacker wanting to launch malicious attacks while covering their tracks, by forwarding the responsibility for the malicious campaigns to the owners of the infected PCs.
A popular tactic often used by cybercriminals is called “socks chaining” that is the use of numerous Socks4/Socks5 servers to maintain the same connection, acting as stepping stones, allowing the cybercriminal to route their connection through multiple malware-infected hosts.
Such use and monetization of malware-infected hosts is making it increasingly difficult for security researchers and law enforcement to correctly attribute the source of a cyber attack.
Webroot’s security researchers will continue monitoring the service, and its future development.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.







Hi there! I am so delighted I found your weblog, I really found you by error while I was searching on Digg for something else. Anyhow I am here now and would just like to say kudos for a tremendous post and all around interesting blog (I also love the theme/design), I don’t have time to go through it all at the minute but I have book-marked it and also included your RSS feeds, so when I have time I will be back to read a lot more. Please do keep up the superb job!