In order for cybercriminals to launch, spam, phishing and targeted attacks, they would first have to obtain access to a “touch point”, in this case, your valid email address, IM screen name, or social networking account.
Throughout the years, they’ve been experimenting with multiple techniques to obtain usernames (YouTube user names, IM screen names, Hotmail email addresses) and valid email addresses from unsuspecting end and corporate users.
In this post we’ll profile a recently released Russian DIY email harvester, and emphasize on the difference between notice and experienced cybercriminals in the context of the tactics and techniques they use to obtain a potential victim’s email address.
More details:
Screenshots of the Email harvester in action:
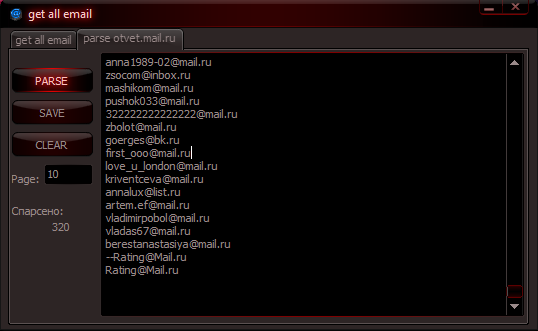
As you can see in the attached screeenshots, the program works by parsing email addresses available on a particular web site. It doesn’t automatically crawl other pages parked on the same domain. Instead, the page to be parses has to be a static one. The program, currently advertised as cybercrime-friendly web forums, doesn’t necessarily represent an immediate threat to Internet users, thanks to its simplistic nature.
Last month, Webroot profiled an underground web service that continue selling millions of already harvested email addresses, next to another service, selling exclusive access to U.S Government and U.S Military email addresses, for potential use in targeted, segmented attacks, also known as advanced persistent threats.
The primitive web page parsing technique used in this email harvester, cannot be compared to the data mining of malware-infected hosts for valid emails, next to actually harvesting them in real-time by using Twitter. These increasingly popular email harvesting techniques continue being used by cybercriminals across the globe in order to ensure that they can successfully reach their prospective victims at any time.
Webroot advises users to be extra cautions when sharing their email on a publicly accessible Web server, as spammers are constantly crawling these in order to obtain fresh and valid email addresses.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.








I read this description fully . It’s really great site . I think it will be helpful for everyone .
Thank you .
I have been wondering where all the spam mails were coming from, as I am quite careful with divulging my email. There will always be crime, and the web is an open field for perpetrators. We have to learn to protect ourselves as best as we can, just like in the real world. http://youtu.be/ZCRRD9xJ2w8
Great post to rise the awareness on the email security topic.
Still no comprehensive measures out there to fight the spammers.
Thanks for the post.