From DIY (do-it-yourself) exploit generating tools, to efficient platforms for exploitation of end and corporate users, today’s efficiency-oriented cybercriminals are constantly looking for ways to monetize hijacked web traffic. In order to do so, they periodically introduce new features in the exploit kits, initiate new partnerships with managed malware/script crypting services, and do their best to stay ahead of the security industry.
What are some of the latest developments in this field?
Meet Sweet Orange, one of the most recently released web malware exploitation kits, available for sale at selected invite-only cybercrime-friendly communities.
What’s so special about Sweet Orange? Does it come with customer support? What client-side exploits is it serving? How are the Russian cybercriminals behind it differentiating their underground market proposition in comparison with competing kits, such as the market leading Black Hole web malware exploitation kit?
Let’s find out.
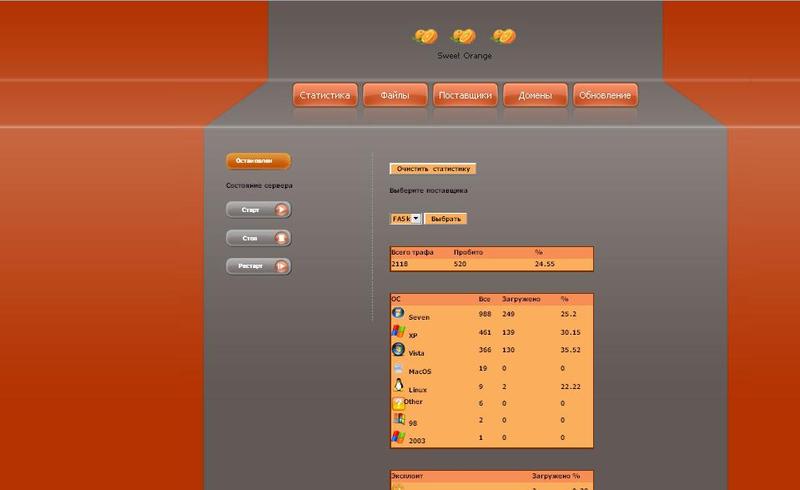
Screenshots of the Sweet Orange web malware exploitation kit in action:
As you see in the attached demo shots, the cybercriminals have already managed to infect 497 users running Internet Explorer, and another 22 running Mozilla’s Firefox. Affected operating systems include, 249 hosts running Windows 7, 139 running Windows XP, and 130 running Windows Vista.
What’s particularly interesting about the Sweet Orange web malware exploitation kit, is that just like the Black Hole exploit kit, its authors are doing their best to ensure that the security community wouldn’t be able to obtain access to the source code of the kit, in an attempt to analyze it. They’re doing this, by minimizing the advertising messages posted on invite-only cybercrime-friendly web communities, and without offering any specific details, demos or screen shots unless the potential buyer directly contacts the seller and has a decent reputation within the cybercrime ecosystem.
Despite the OPSEC (operational security) applied to their underground market proposition, we managed to find out interesting details regarding the pricing, including screenshots, and the variety of exploits included in the kit.
How much does it cost to rent or purchase the Sweet Orange exploit kit? According to the Russian cybercriminals behind it:
- We can provide one-day test for 80 WMZ, rent for week – 375$, month – 1400$, unlimited domains ; purchasing: 2500$ and support: 800$ for cleaning, 10$ – one domain, 300$ – multi-domain license; we accept WebMoney only
More details from their underground market proposition:
- Rent: traffic limit 150k/day; purchasing: unlimited traffic; ratio – you can test with your traf; ratio 10-25%, always clean pack; domains is clean in long time
Client-side exploits found in the kit:
- Java exploits, PDF exploits, Internet Explorer exploits, Firefox exploits
Next to managed crypting of the malicious binaries, the vendor is also offering 150,000 unique visitors to be redirected to the malicious payload served by the exploit kit. Cybercriminals often hijack millions of unique visitors through black hat search engine optimization campaigns (blackhat SEO), malvertising, and bogus content blog farms consisting of hundreds of thousands of automatically registered blogs.
Webroot will continue monitoring the development of this kit, to ensure that Webroot SecureAnywhere customers are protected from its malicious payload.
To find more about Dancho Danchev, follow him on Twitter.










Very dangerous kits.Security experts and analysist should be aware of this.Thanks Dancho and webroot team to share this.I have shared this in Facebook Internet Security Group so that every security geek should be aware of this.
dont worry guys next time SWEET ORANGE sends you a normal Xmass card with glitteringglattering snow and reindeeer and santa claaus
and angels “and wich up on a STAR”
it works to,right!!????