Imagine you’re a cybercriminal that has somehow managed to infect a 1000 U.S based hosts and is looking for ways to monetize his malicious activity? He could easily start spreading spam or phishing emails, use the infected hosts as a platform for disseminating related malware attacks, or basically data mine the infected hosts for accounting data to be later on sold to fellow cybercriminals.
What if all he wanted to do is earn as much profit in the shortest possible amount of time without investing more efforts into the monetization of the infected hosts? Is the cybercrime ecosystem mature enough to offer him an alternative? Appreciate the rhetoric. The maturing cybercrime ecosystem is fully capable of offering him a high liquidity monetization approach for earning revenue by infecting hosts and spreading a specific undetectable executable pushed by the pay-per-install affiliate network that I’ll profile in this post.
More details:
The Pay-Per-Install affiliate network model, has been steadily gaining popularity over the past few years. With a dozen of affiliate networks willing to share revenue for the process of infecting hosts with an executable provided by them, cybercriminals have been taking advantage of this well developed monetization strategy for years.
Over the past few months, I’ve been noticing an increase in the advertising of a particular Pay-Per-Install affiliate network, on selected cybercrime-friendly online communities. The network, is exclusively targeting Internet users located in developed countries with cybercriminals taking into consideration their high purchasing power. What’s so special about this affiliate network? What’s the underground market’s going rate for a 1000 U.S based malware-infected hosts? Let’s find out.
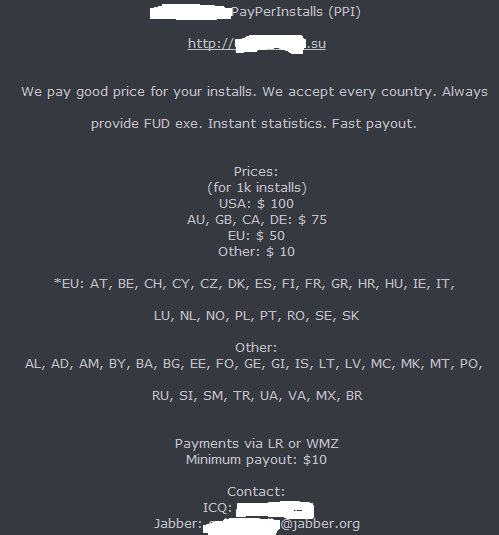
Screenshoot of a sample advertisement of the Pay-Per-Install affiliate network:
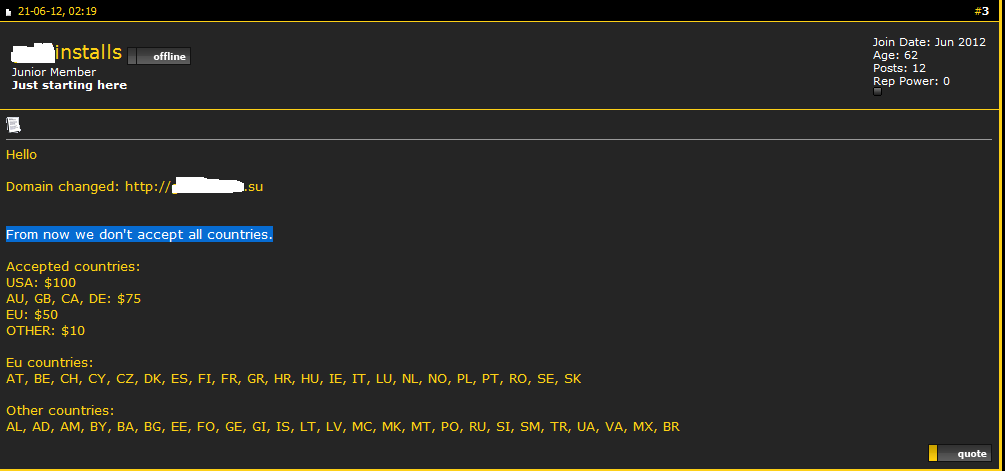
Second screenshot of a sample advertisement of the Pay-Per-Install affiliate network:
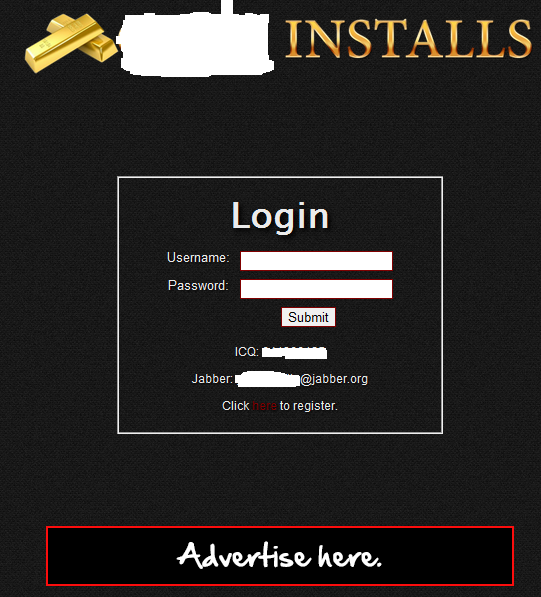
Screenshot of the main registration — invite only — site of the Pay-Per-Install affiliate network:
What’s particularly interesting about this affiliate network is that it’s invite only, namely only selected members of the cybercrime ecosystem will get access to the administration panel, and consequently to the latest version of the malicious executable that they have to spread in order to earn revenue from the service.
The prices? A 1,000 U.S based malware-infected hosts go for $100, AU, GB, CA and DE go for $75 and EU based malware-infected users go for $50. What’s also worth pointing out is that the administrator of the affiliate network is soliciting additional revenues from this project by offering advertising space for related cybercrime-friendly projects on the front page of the affiliate network.
Webroot will continue monitoring the development of the pay-per-install affiliate network.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.







Am I protected from the latest invasion?