Recently, cybercriminals launched yet another massive spam campaign, this time impersonating the Internal Revenue Service (IRS) in an attempt to trick tax payers into clicking on a link pointing to a bogus Microsoft Word Document. Once the user clicks on it, they are redirected to a Black Hole exploit kit landing URL, where they’re exposed to the client-side exploits served by the kit.
More details:
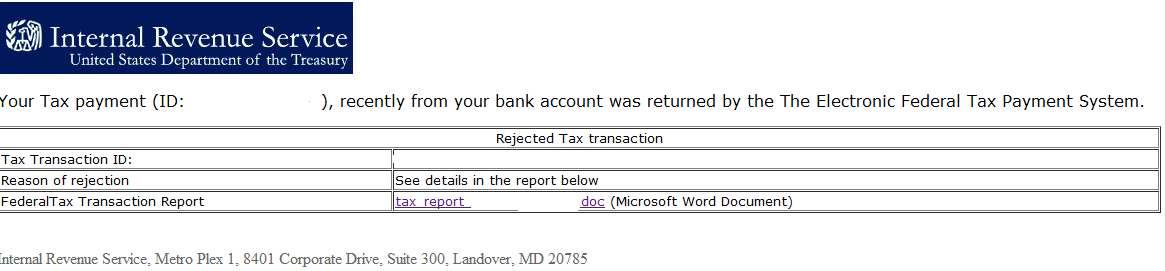
Screenshot of the spamvertised IRS themed email:
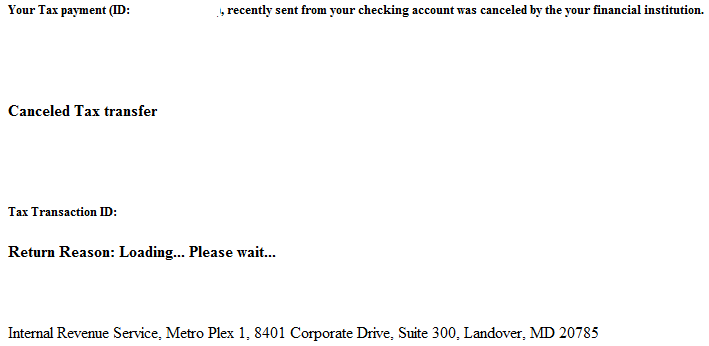
Once the user clicks on the link pointing to a Black Hole landing URL, he’s exposed to the following bogus “Page loading…” page:
Spamvertised URLs: hxxp://tiraccontolamusica.it/reves.html; hxxp://marcina.pl//reves.html; hxxp://juegosinternet.org/reves.html; hxxp://breastenlargementratings.com/reves.html
Client-side exploits serving URL: hxxp://retweetadministrator.org/main.php?page=8b45f871830c6e5a
Client-side exploits served: CVE-2010-0188; CVE-2010-1885
Detection rate for a sample redirection script: MD5: 1ab7543c3c7857eec5014b3de5da362e detected by 3 out of 41 antivirus scanners as JS/Iframe.W!tr; Trojan-Downloader.JS.Iframe.czj.
Upon successful client-side exploitation, the campaign drops MD5: 6d7b7d2409626f2c8c166373e5ef76a5 on the affected hosts, currently detected by 30 out of 41 antivirus scanners as Trojan-Ransom.Win32.Gimemo.akxc
Also, as you can see in the first screenshot, the cybercriminals behind the campaign didn’t bother to use the services of a “cultural diversity on demand” underground market proposition offering the ability to localize a message or a web site to the native language of the prospective victim, hence they failed to properly formulate their sentence, thereby raising suspicion in the eyes of the prospective victim.
Webroot SecureAnywhere users are proactively protected from this threat.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.