Cybercriminals are masters of abusing legitimate infrastructure for their malicious purposes. From phishing sites and Black Hole exploit kit landing URLs hosted on compromised servers, abuse of legitimate web email service providers’ trusted DKIM verified ecosystem, to the systematic release of DIY spamming tools utilizing a publicly obtainable database of user names as potential “touch points”, cybercriminals are on the top of their game.
In this post, I’ll profile a recently advertised DIY SMS flooder using Skype’s infrastructure for disseminating the messages, and assess the potential impact it could have on end and corporate users.
More details:
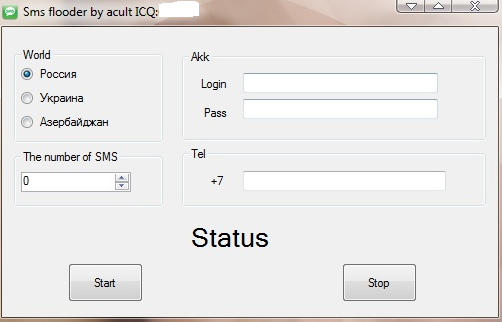
Sample screenshot of the advertised DIY Skype SMS flooding tool:
The DIY tool is available on selected cybercrime friendly communities for $20. It has the capability to send SMS messages to numbers in Russia, Ukraine, and Azerbaijan. It’s taking advantage of the fact that every Skype account with a positive balance has the ability to send SMS messages. Once the spammer authenticates himself with a stolen Skype account, the tool will automatically start using the account’s balance and flood the victim’s cell phone number with multiple messages.
Does this tool represent an actual threat to Skype’s users, or victims of the SMS flooding attack? Thanks to the fact that it has the capability to use only one Skype account, it will have a limited impact on Skype’s network, as well as on the device of a prospective victim. However, the tool is currently released as v 1.0, and the author can add support for multiple Skype accounts at any time, potentially multiplying the SMS flooding effect.
We’ll continue monitoring the development of the DIY tool.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.