On a daily basis, new market entrants into the cybercrime ecosystem attempt to monetize their coding skills by releasing and branding new DIY DDoS malware loaders. Largely dominated by “me too” features, these DIY malware loaders are purposely released with prices lower than the prices of competing bots, in an attempt by the cybercriminal behind them to gain market share – a necessary prerequisite for a successful long-term oriented business model.
In this post, I’ll profile a recently released Russian DDoS malware bot.
More details:
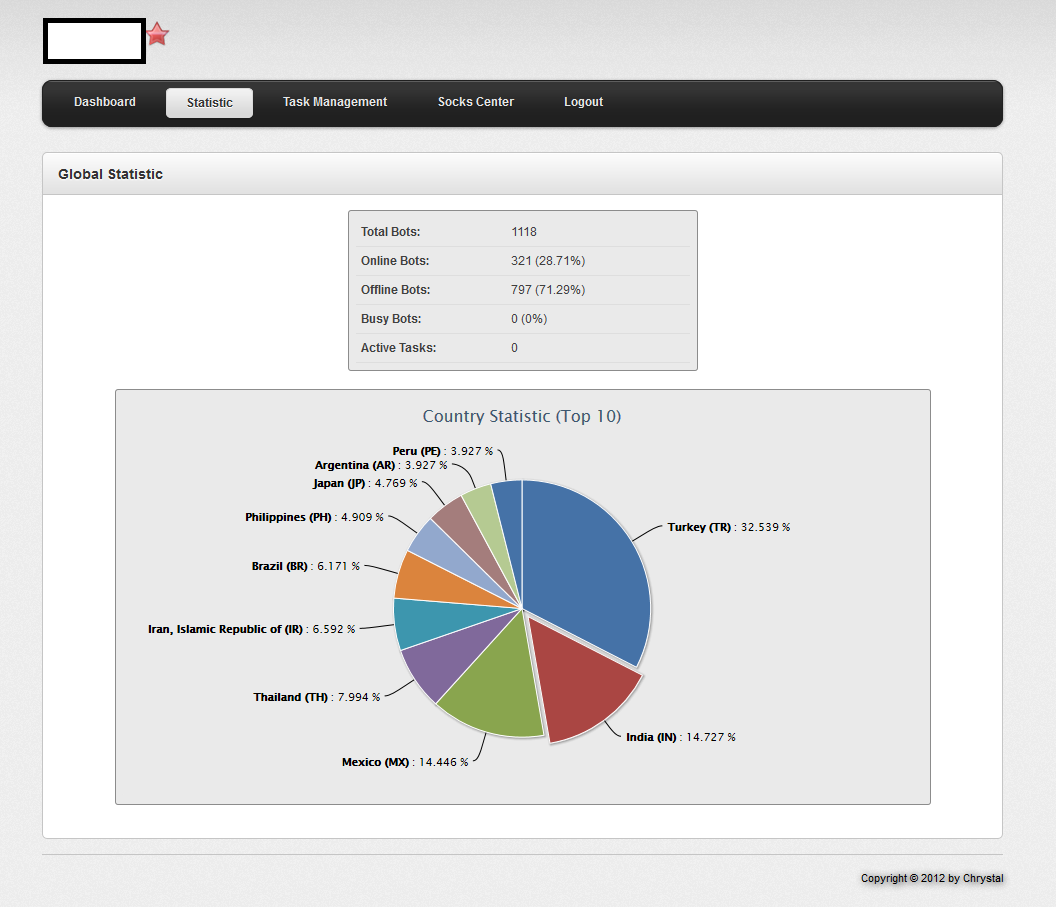
Sample screenshot of the GUI of the DDoS malware loader:
As you can see in the above screenshot, the cybercriminal behind the malware loader has already managed to infect 1,118 users, the majority of whom are based in Turkey, followed by India and Mexico.
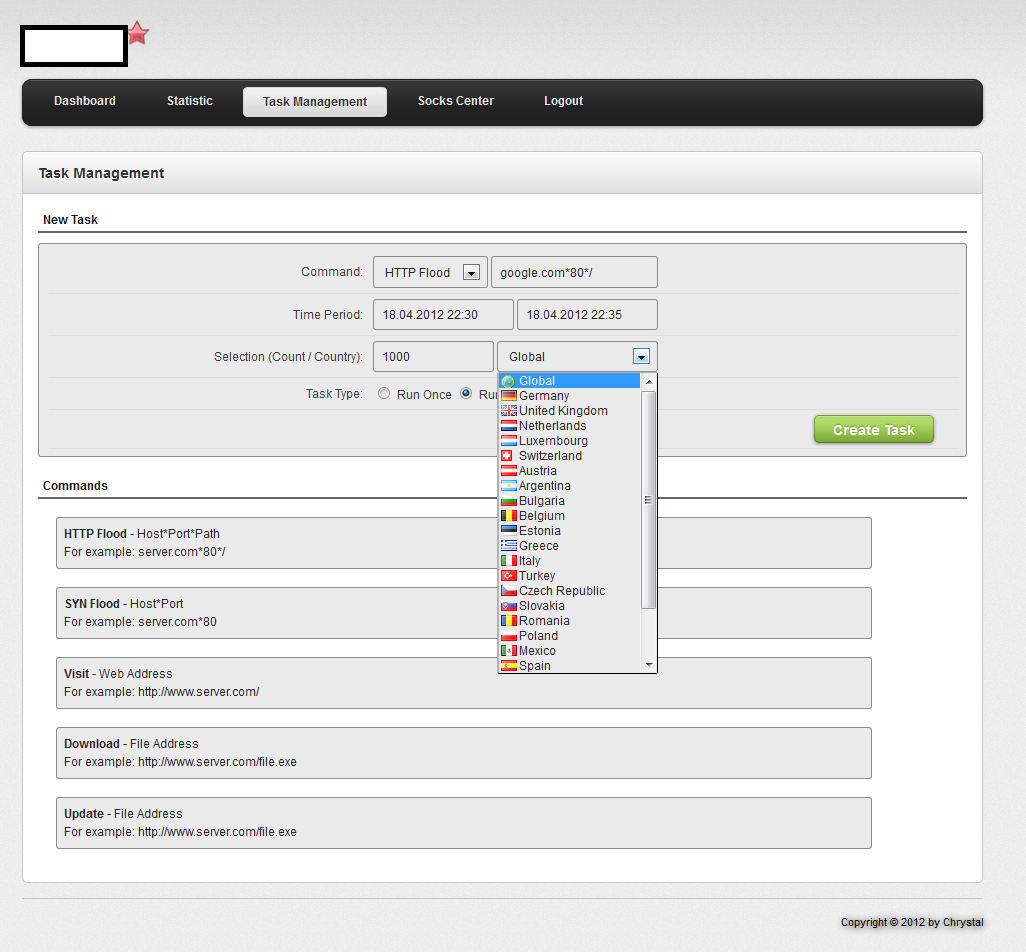
Second screenshot of the GUI of the DDoS malware loader:
He has also managed to infect a variety of different Microsoft Windows versions.
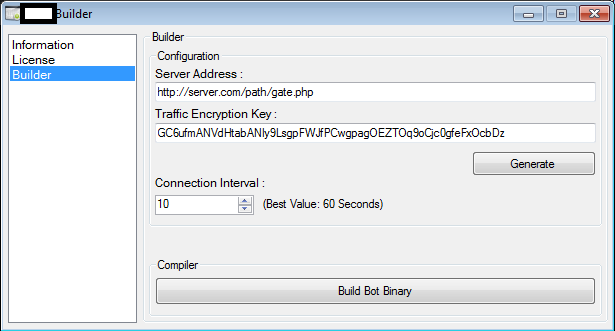
Third screenshot of the GUI of the DDoS malware loader:
Some of the key features of the malware loader are:
– Intuitive command and control panel
– DDoS capability, currently supporting HTTP/SYN Flood/UDP flood
– Loader functionality
– Visit a specific site — potential click-fraud abuse
– USB spreading mechanism
– Socks5 conversion available
– Update mechanism for the malware loader
– 256 bit AES encryption used in the command and control communication
– Anti-Debugging functionality
Go through related profiles of DIY DDoS bots and malware loaders:
- New Russian DIY DDoS bot spotted in the wild
- A peek inside the Darkness (Optima) DDoS Bot
- A peek inside the Cythosia v2 DDoS Bot
- A peek inside the uBot malware bot
- A peek inside the Smoke Malware Loader
- A peek inside the PickPocket Botnet
- A peek inside the Umbra malware loader
What’s particularly interesting about this malware loader, is the fact that it’s a modification of the original code by Chrystal, author of the first versions. Sample screenshots of version 1.0:
We’ll continue monitoring the development of this malware loader.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.