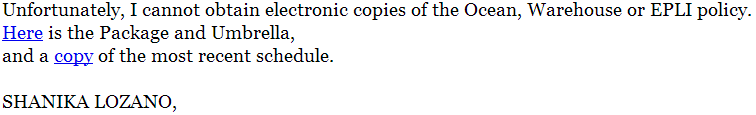Attempting to achieve a higher click-through rate for their exploits and malware serving malicious campaign, cybercriminals are currently spamvertising millions of emails attempting to trick users into thinking they’ve become part of a private conversation about missing EPLI policies.
In reality, clicking on any of the links in the oddly formulated email will expose them to the client-side exploits served by the latest version of the Black Hole Exploit Kit.
More details:
Sample screenshot of the spamvertised email:
Sample spamvertised and compromised URLs used in the campaign: hxxp://visage.ie/catalog/infourl.htm; hxxp://www.dace.nul.usb.ve/infourl.htm; hxxp://www.radclivecumchackmore.org.uk/drupal/sites/default/files/infourl.htm; hxxp://www.sgsoluciones.com.ar/sites/default/files/infourl.htm; hxxp://www.mv-ettlingenweier.de/sites/default/files/infourl.htm; hxxp://lanhaituandui.com/infourl.htm; hxxp://www.mv-ettlingenweier.de/sites/default/files/infourl.htm; hxxp://www.radclivecumchackmore.org.uk/drupal/sites/default/files/infourl.htm; hxxp://erotictrust.info/sites/all/themes/infourl.htm; hxxp://www.cardissa.fr/sites/default/files/infourl.htm; hxxp://mercurycube.com/infourl.htm; hxxp://www.fest-for-alle.dk/infourl.htm; hxxp://www.catriders.com/infourl.htm
Sample client-side exploits serving URL: hxxp://monacofrm.ru:8080/forum/links/column.php
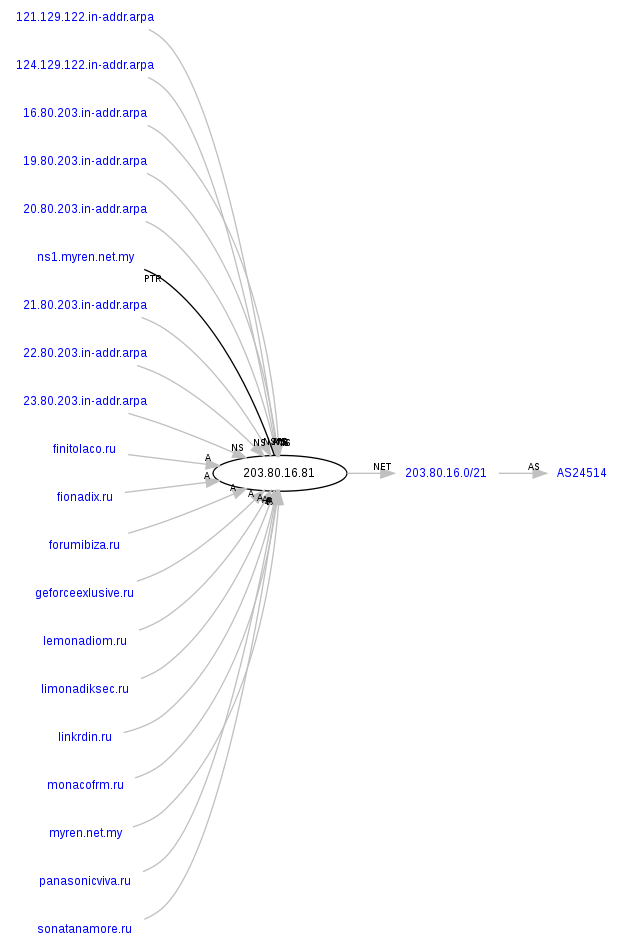
Malicious domain name reconnaissance:
monacofrm.ru – 202.180.221.186, AS24496; 203.80.16.81, AS24514; 216.24.194.66, AS40676
Name server: ns1.monacofrm.ru – 62.76.178.233
Name server: ns2.monacofrm.ru – 41.168.5.140
Name server: ns3.monacofrm.ru – 132.248.49.112
Name server: ns4.monacofrm.ru – 209.51.221.247
The following malicious domains also respond to these IPs:
canadianpanakota.ru
lemonadiom.ru
peneloipin.ru
veneziolo.ru
forumibiza.ru
controlleramo.ru
moneymakergrow.ru
fionadix.ru
linkrdin.ru
geforceexlusive.ru
We’ve already seen lemonadiom.ru in another malicious campaign – “‘Fwd: Scan from a Xerox W. Pro’ themed emails lead to Black Hole Exploit Kit“, as well as linkrdin.ru in the following malicious campaigns: “‘Fwd: Scan from a Xerox W. Pro’ themed emails lead to Black Hole Exploit Kit“; “Cybercriminals spamvertise bogus ‘Microsoft License Orders’ serve client-side exploits and malware“. Clearly, these campaigns are operated by the same cybercriminal/gang of cybercriminals.
Sample detection rate for the javascript redirector: MD5: 65077fafa6632a43015320272c6a5776 – detected by 10 out of 44 antivirus scanners as Mal/JSRedir-M
Sample detection rate for a live client-side exploit: hxxp://monacofrm.ru:8080/forum/data/spn2.jar – SHANIKA.jar – MD5: d44ffa6065298d8b87900a7b9b16a494 – detected by 10 out of 44 antivirus scanners as Exploit.Java.CVE-2012-5076.A
Upon successful client-side exploitation, the campaign drops MD5: eadc019f64bbc6c162631db2430cb9a7 – detected by 15 out of 44 antivirus scanners as Trojan-Spy.Win32.Zbot.gkjh
We also know is that on 2012-11-12 10:58:07, the following client-side exploits serving domain was also responding to the same IP (202.180.221.186) – hxxp://canadianpanakota.ru:8080/forum/links/column.php. Upon successful client-side exploitation, this URL dropped MD5: 532bdd2565cae7b84cb26e4cf02f42a0 – detected by 33 out of 44 antivirus scanners as Worm:Win32/Cridex.E.
We’re also aware of two more client-side exploits serving domains responding to the same IP (202.180.221.186) on 2012-11-15 19:49:33 – hxxp://investomanio.ru/forum/links/public_version.php, and on the 2012-11-15 04:40:06 – hxxp://veneziolo.ru/forum/links/column.php.
Name servers part of the campaign’s infrastructure:
Name server: ns1.canadianpanakota.ru – 62.76.178.233
Name server: ns2.canadianpanakota.ru – 132.248.49.112
Name server: ns3.canadianpanakota.ru – 84.22.100.108
Name server: ns4.canadianpanakota.ru – 65.99.223.24
Name server: ns1.lemonadiom.ru – 85.143.166.170
Name server: ns2.lemonadiom.ru – 132.248.49.112
Name server: ns3.lemonadiom.ru – 84.22.100.108
Name server: ns4.lemonadiom.ru – 213.251.171.30
Name server: ns1.peneloipin.ru – 62.76.186.190
Name server: ns2.peneloipin.ru – 132.248.49.112
Name server: ns3.peneloipin.ru – 84.22.100.108
Name server: ns4.peneloipin.ru – 65.99.223.24
Name server: ns1.veneziolo.ru – 62.76.178.233
Name server: ns2.veneziolo.ru – 41.168.5.140
Name server: ns3.veneziolo.ru – 132.248.49.112
Name server: ns4.veneziolo.ru – 209.51.221.247
Name server: ns1.forumibiza.ru – 62.76.186.190
Name server: ns2.forumibiza.ru – 84.22.100.108
Name server: ns3.forumibiza.ru – 50.22.102.132
Name server: ns4.forumibiza.ru – 213.251.171.30
Name server: ns1.controlleramo.ru – 62.76.186.190
Name server: ns2.controlleramo.ru – 132.248.49.112
Name server: ns3.controlleramo.ru – 84.22.100.108
Name server: ns4.controlleramo.ru – 65.99.223.24
Name server: ns1.moneymakergrow.ru – 62.76.178.233
Name server: ns2.moneymakergrow.ru – 132.248.49.112
Name server: ns3.moneymakergrow.ru – 84.22.100.108
Name server: ns04.moneymakergrow.ru – 65.99.223.24
Name server: ns1.fionadix.ru – 62.76.186.190
Name server: ns2.fionadix.ru – 84.22.100.108
Name server: ns3.fionadix.ru – 50.22.102.132
Name server: ns4.fionadix.ru – 213.251.171.30
Name server: ns1.linkrdin.ru – 85.143.166.170
Name server: ns2.linkrdin.ru – 132.248.49.112
Name server: ns3.linkrdin.ru – 84.22.100.108
Name server: ns4.linkrdin.ru – 79.98.27.9
Name server: ns1.geforceexlusive.ru – 62.76.47.51
Name server: ns2.geforceexlusive.ru – 132.248.49.112
Name server: ns3.geforceexlusive.ru – 84.22.100.108
Name server: ns4.geforceexlusive.ru – 79.98.27.9
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.