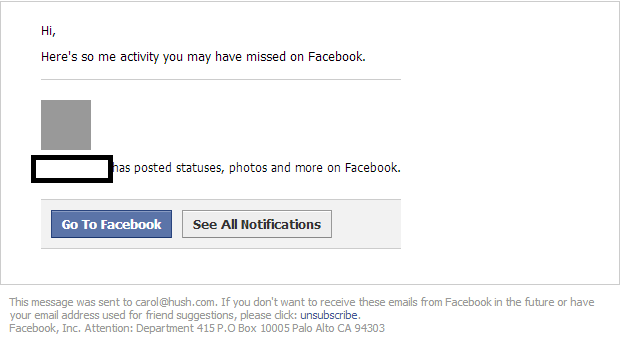
Facebook users, watch out!
A recently launched malicious spam campaign is impersonating Facebook, Inc. in an attempt to trick its one billion users into thinking that they’ve received a notification alerting them on activities they may have missed on Facebook. Upon clicking on any of the links found in the email, users are exposed to the client-side exploits served by the Black Hole Exploit Kit.
More details:
Sample screenshot of the spamvertised email:
Sample spamvertised compromised URL: hxxp://www.covellogroup.com/new.htm?_RANDOM_CHARACTERS
Sample client-side exploits serving URL: hxxp://ceredinopl.ru:8080/forum/links/column.php
Malicious payload serving URL: hxxp://ceredinopl.ru:8080/forum/links/column.php?cfcjm=xbc229&fnhcuc=njx&svdp=2v:1k:1m:32:33:1k:1k:31:1j:1o&xdva=
Sample client-side exploits served: CVE-2010-0188
Malicious domain name reconnaissance:
ceredinopl.ru – 203.80.16.81 (AS24514); 208.87.243.131; 216.24.196.66 (AS40676); 202.180.221.186 (AS24496)
Name servers:
ns1.ceredinopl.ru – 203.172.140.202
ns10.ceredinopl.ru – 88.84.130.46
ns11.ceredinopl.ru – 89.216.41.8
ns12.ceredinopl.ru – 41.66.137.155
ns13.ceredinopl.ru – 79.142.32.36
ns14.ceredinopl.ru – 87.120.41.155
ns15.ceredinopl.ru – 72.55.156.167
ns16.ceredinopl.ru – 91.194.122.8
ns17.ceredinopl.ru – 202.3.245.13
ns18.ceredinopl.ru – 178.79.146.49
ns19.ceredinopl.ru – 69.64.89.82
ns2.ceredinopl.ru – 41.168.5.140
ns20.ceredinopl.ru – 70.38.31.71
ns21.ceredinopl.ru – 132.248.49.112
ns22.ceredinopl.ru – 74.117.59.55
ns23.ceredinopl.ru – 62.76.178.233
ns24.ceredinopl.ru – 62.76.188.138
ns25.ceredinopl.ru – 216.24.194.130
ns26.ceredinopl.ru – 79.98.27.9
ns27.ceredinopl.ru – 209.44.116.18
ns28.ceredinopl.ru – 173.224.220.180
ns29.ceredinopl.ru – 78.83.233.242
ns3.ceredinopl.ru – 132.248.49.112
ns30.ceredinopl.ru – 87.204.199.100
ns31.ceredinopl.ru – 199.71.212.78
ns32.ceredinopl.ru – 173.224.209.66
ns33.ceredinopl.ru – 62.76.188.246
ns34.ceredinopl.ru – 50.23.137.202
ns35.ceredinopl.ru – 95.154.43.193
ns36.ceredinopl.ru – 188.138.92.16
ns37.ceredinopl.ru – 64.150.187.72
ns38.ceredinopl.ru – 84.22.100.108
ns39.ceredinopl.ru – 184.106.189.124
ns4.ceredinopl.ru – 65.99.223.24
ns40.ceredinopl.ru – 116.12.49.68
ns41.ceredinopl.ru – 178.63.51.54
ns42.ceredinopl.ru – 120.89.91.57
ns43.ceredinopl.ru – 213.251.171.30
ns44.ceredinopl.ru – 85.125.81.51
ns5.ceredinopl.ru – 50.22.102.132
ns6.ceredinopl.ru – 41.168.5.140
ns7.ceredinopl.ru – 209.51.221.247
ns8.ceredinopl.ru – 203.80.16.81
ns9.ceredinopl.ru – 175.136.239.146
Upon successful client-side exploitation the campaign drops MD5: 9db13467c50ef248eaf6c796dffdd19c – detected by 3 out of 41 antivirus scanners as PWS-Zbot.gen.aqw.
Responding to the same IPs – 203.80.16.81 (AS24514); 208.87.243.131; 216.24.196.66 (AS40676); 202.180.221.186 (AS24496) – are also the following malicious domains:
investinindia.ru
hamasutra.ru
feronialopam.ru
monacofrm.ru
bamanaco.ru
ionalio.ru
investomanio.ru
veneziolo.ru
fanatiaono.ru
analunakis.ru
We’ve already seen and profiled some of these domains used in another malicious spam campaign, indicating that both campaigns have been launched by the same cybercriminal/gang of cybercriminals:
monacofrm.ru – seen in “‘Copies of Missing EPLI Policies’ themed emails lead to Black Hole Exploit Kit”
investomanio.ru – seen in “‘Copies of Missing EPLI Policies’ themed emails lead to Black Hole Exploit Kit”
veneziolo.ru – seen in “‘Copies of Missing EPLI Policies’ themed emails lead to Black Hole Exploit Kit”
Name servers part of the campaign’s infrastructure:
ns1.investinindia.ru – 62.76.178.233
ns2.investinindia.ru – 41.168.5.140
ns3.investinindia.ru – 132.248.49.112
ns4.investinindia.ru – 209.51.221.247
ns1.hamasutra.ru – 62.76.178.233
ns2.hamasutra.ru – 41.168.5.140
ns3.hamasutra.ru – 132.248.49.112
ns4.hamasutra.ru – 209.51.221.247
ns1.feronialopam.ru – 62.76.178.233
ns2.feronialopam.ru – 41.168.5.140
ns3.feronialopam.ru – 132.248.49.112
ns4.feronialopam.ru – 209.51.221.247
ns1.monacofrm.ru – 62.76.178.233
ns2.monacofrm.ru – 41.168.5.140
ns3.monacofrm.ru – 132.248.49.112
ns4.monacofrm.ru – 209.51.221.247
ns1.bamanaco.ru – 62.76.178.233
ns2.bamanaco.ru – 41.168.5.140
ns3.bamanaco.ru – 132.248.49.112
ns4.bamanaco.ru – 209.51.221.247
ns1.ionalio.ru – 62.76.178.233
ns2.ionalio.ru – 41.168.5.140
ns3.ionalio.ru – 132.248.49.112
ns4.ionalio.ru – 209.51.221.247
ns1.investomanio.ru – 62.76.178.233
ns2.investomanio.ru – 41.168.5.140
ns3.investomanio.ru – 132.248.49.112
ns4.investomanio.ru – 209.51.221.247
ns1.veneziolo.ru – 62.76.178.233
ns2.veneziolo.ru – 41.168.5.140
ns3.veneziolo.ru – 132.248.49.112
ns4.veneziolo.ru – 209.51.221.247
ns1.fanatiaono.ru – 62.76.178.233
ns2.fanatiaono.ru – 41.168.5.140
ns3.fanatiaono.ru – 132.248.49.112
ns4.fanatiaono.ru – 209.51.221.247
ns1.analunakis.ru – 62.76.178.233
ns2.analunakis.ru – 41.168.5.140
ns3.analunakis.ru – 132.248.49.112
ns4.analunakis.ru – 209.51.221.247
This isn’t the first time that we intercept a Facebook notifications themed malicious attack. During October, 2012, we intercepted two – “Bogus Facebook notifications lead to malware“; “Cybercriminals spamvertise millions of bogus Facebook notifications, serve malware“.
You can also consider going through previously analyzed Facebook themed malicious campaigns:
- Malware campaign spreading via Facebook direct messages spotted in the wild
- Spamvertised ‘You have 1 lost message on Facebook’ campaign leads to pharmaceutical scams
If users feel they received a bogus email that may not be coming from Facebook, they can alert Facebook by forwarding the message to phish@fb.com. In addition, users can check to see if their account has been compromised by visiting www.facebook.com/hacked.
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.