Facebook users, watch what you click on!
Cybercriminals are currently mass mailing bogus “Facebook Account Cancellation Requests“, in an attempt to trick Facebook’s users into clicking on the malicious link found in the email. Upon clicking on the link, users are exposed to client-side exploits which ultimately drop malware on the affected host.
More details:
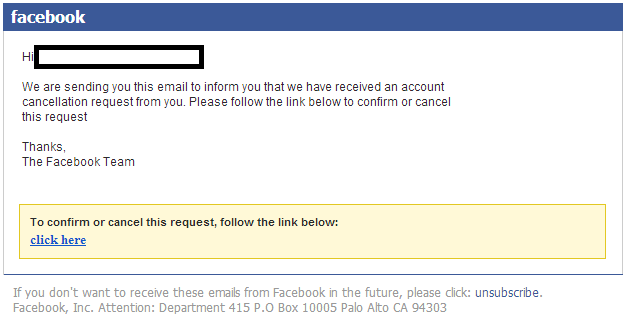
Sample screenshot of the spamvertised email:
Sample client-side exploitation chain: hxxp://adlinkservhost.strangled.net -> hxxp://lakkumigdc.com/media/clients/index.php?showtopic=397065 -> hxxp://lakkumigdc.com/media/clients/rhin.jar -> hxxp://lakkumigdc.com/media/clients/Goo.jar -> hxxp://lakkumigdc.com/media/clients/lib.php -> hxxp://lakkumigdc.com/media/clients/load.php?showforum=lib
Sample client-side exploits served: CVE-2010-0188; CVE-2011-3544; CVE-2010-0840
Malicious domain name reconnaissance:
lakkumigdc.com – 68.168.100.135 – Email: dolphinkarthi@gmail.com
Name Server: NS1.MACROVIEWTECH.COM – 68.168.100.136
Name Server: NS2.MACROVIEWTECH.COM – 68.168.100.137
Domains responding to the same IP, including domains also registered with the same GMail account:
drganesanneurospine.com
dryathishoncologist.com
hematologistcoimbatore.com
lakkumigdc.com
ciska.org
texsonpumps.com
icreu2012.com
lakkumigdc.com
paypal.com.tradelinee.com
pianoforall.theseopark.com
update-paypall.32165453423154623166352.indianmjp.com
paypal.com.usa.ssion.secure.acess.update.reg.ideators.co
paypal.com.us.cgi-bin.session.secure.update-info.ideators.co
paypal.com.vtigp.org
zakcreations.com
techhoot.com
ideators.co
Upon successsful client-side exploitation, the campaign drops MD5: 8b3979c1a9c85a7fd5f8ff3caf83fc56 – detected by 3 out of 46 antivirus scanners as PWS-Zbot.gen.aru
Upon execution, the sample creates the following file on the affected hosts:
%AppData%Ixriyvemarosa.exe – MD5: A33684FD2D1FA669FF6573921F608FBB
It also creates the following directories:
%AppData%Ixriyv
%AppData%Uxwonyl
As well as the following Mutex:
Local{7A4AAF46-5391-8FF9-A32F-78A34C8B50D7}
It then phones back to shallowave.jumpingcrab.com (93.174.95.78) on port 8012. Another similar subdomain on this host (takemeout.jumpingcrab.com), was also seen in a crowdsourced DDoS campaign in 2009.
Historically, more malware is known to have been hosted at another subdomain (hxxp://dady.jumpingcrab.com:881/js/js/) in 2011. List of associated MD5s:
MD5: e58fe6d04e8d9fce1020f532d3f0bd49 – detected by 40 out of 44 antivirus scanners as Backdoor.Win32.Delf.yqo
MD5: 60fde61eea4da0601a294d8cac18fb85 – detected by 37 out of 42 antivirus scanners as Backdoor:Win32/Hupigon.EA
MD5: ac95c84a99edd65b00fbc845f8e167f0 – detected by 38 out of 42 antivirus scanners as TrojanDropper:Win32/Delfsnif.A
MD5: 7487bbfadde66edddf131b879382a9ef – detected by 38 out of 43 antivirus scanners as Trojan-PSW.Win32.Bjlog.vge
MD5: 6cf58ce47e4a9163ecf2e5e0498d3fa8 – detected by 38 out of 43 antivirus scanners as Worm.Win32.AutoRun.davw
MD5: a694f0c6a0b64cc3601d946f63330a23 – detected by 34 out of 44 antivirus scanners as Trojan.RAR.Qhost.c
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.