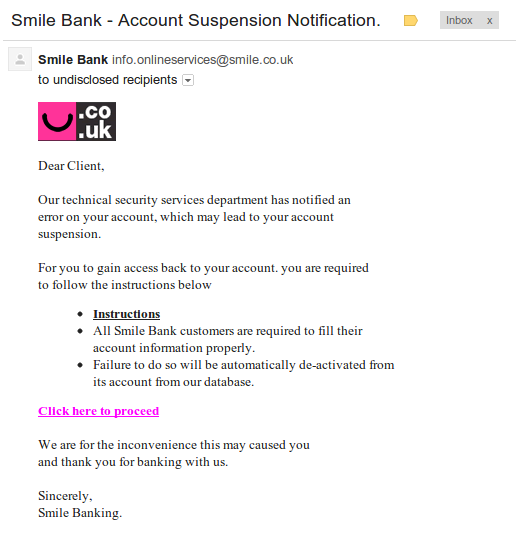
When you’re a threat researcher, you are always on the look out for anything that looks ‘phishy’, even if it’s on your own personal time. Today, I opened my personal email to find this:
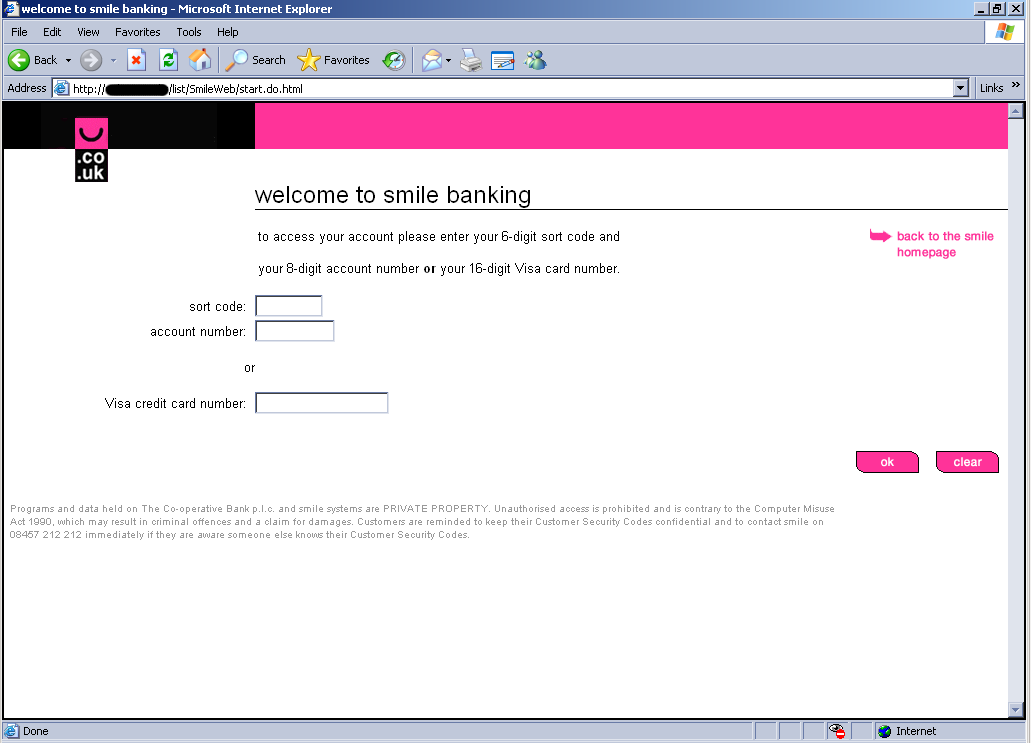
Although the email looked very convincing, I don’t bank with Smile Bank so I knew something was up. Smile Bank is an actual bank based in the UK. The bad guys used a spoofed email address to make it look like it came from the legit Smile Bank domain smile.co.uk. If someone did bank with Smile Bank, I can see how they could easily be tricked. It’s the “Click here to proceed” link that gives the bad guys away. The link goes to a page hosted by pier3.hk, which is a legitimate domain, but appears to be compromised with a simple HTM page that is a redirect to the real malicious site. The redirect sends you here:
Once filled in and submitted, it then sends you here:
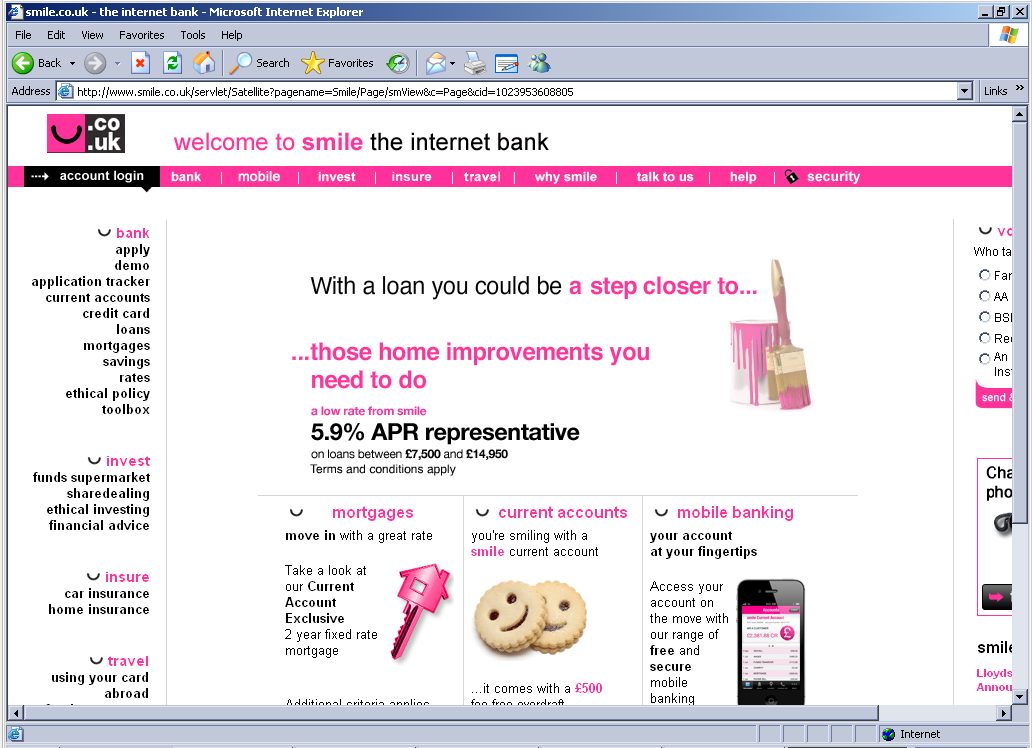
When this page is filled in and submitted, it sends you to the legitimate Smile Bank site:
In the background, I captured the network traffic to discovery all the input I entered being sent in plain text to the malicious URL:
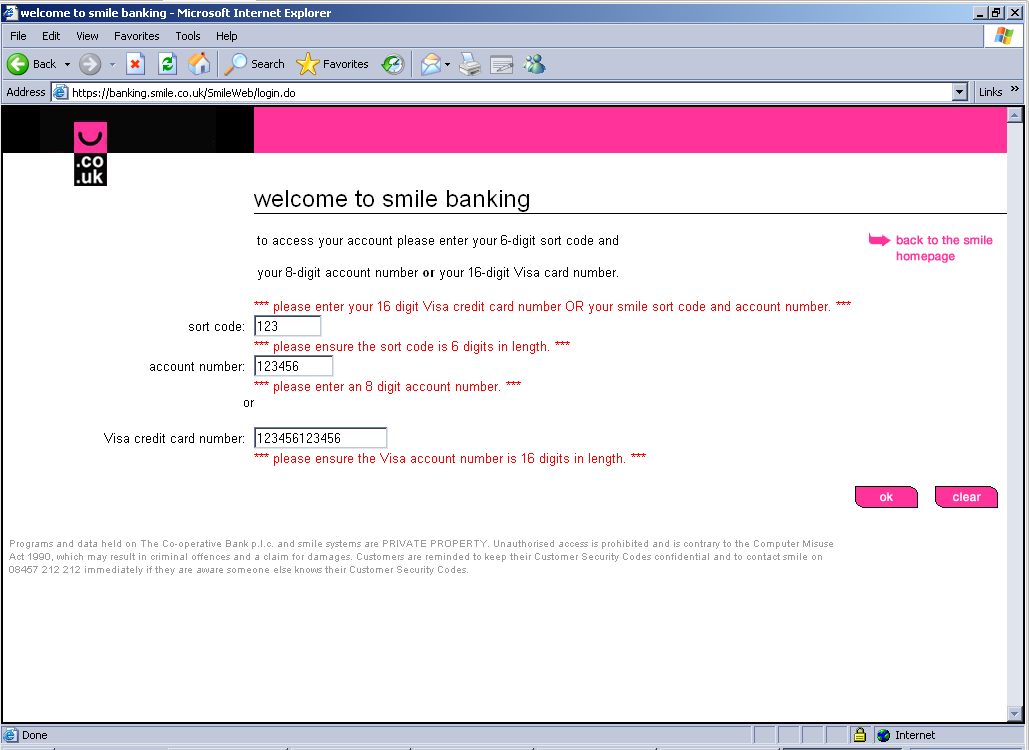
In comparison, I went to Smile Bank’s real login screen. It was identical except for the fact it didn’t accept my nonsense for inputs:
This trick could easily be done with any large bank. Make sure to always be suspicious of any email claiming to be from your bank that threatens your account has been locked and insists that you need to enter your account information. Also, if the link to enter your account information isn’t to the URL of the bank it claims to be from, you know it’s malicious.