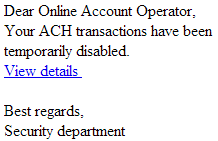
Cybercriminals have recently launched yet another massive spam campaign attempting to trick e-banking users into thinking that their ability to process ACH transactions has been temporarily disabled. Upon clicking on the link found in the malicious email, users are exposed to the client-side exploits served by the Black Hole Exploit Kit.
More details
Sample screenshot of the spamvertised email:
Sample spamvertised compromised URLs:
hxxp://promic.pl/page4.htm
hxxp://promic.pl/rating.htm
Sample client-side exploits serving URLs:
hxxp://bamanaco.ru:8080/forum/links/column.php
hxxp://lentuiax.ru:8080/forum/links/column.php
Malicious domains reconnaissance:
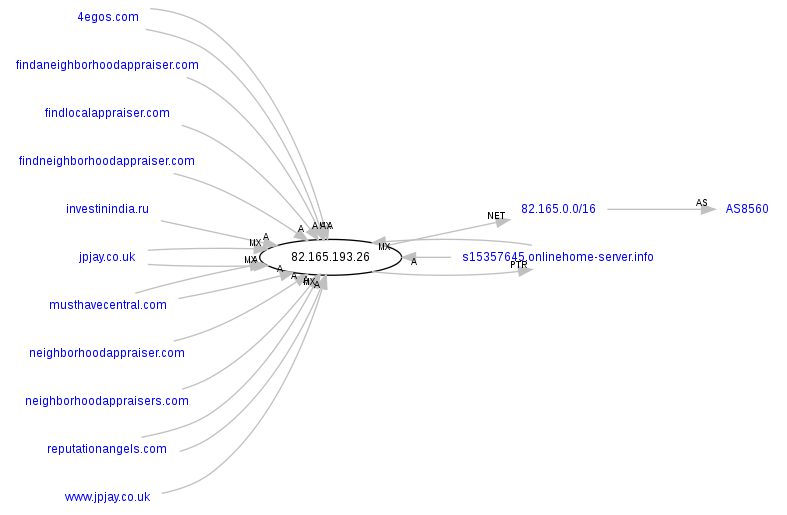
bamanaco.ru – 82.165.193.26 (AS8560); 203.80.16.81 (AS24514); 216.24.196.66 (AS40676)
Name servers:
ns1.bamanaco.ru -62.76.178.233
ns2.bamanaco.ru – 41.168.5.140
ns3.bamanaco.ru – 132.248.49.112
ns4.bamanaco.ru – 209.51.221.247
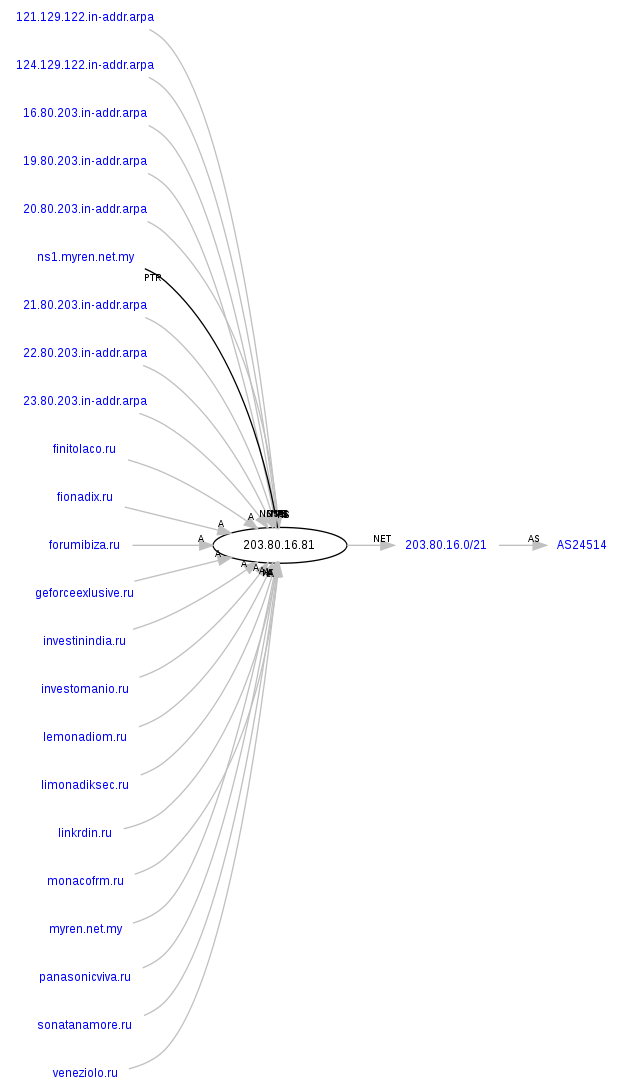
lentuiax.ru – 203.80.16.81 (AS24514)
Name servers:
ns1.lentuiax.ru – 62.76.178.233
ns2.lentuiax.ru – 41.168.5.140
ns3.lentuiax.ru – 132.248.49.112
ns4.lentuiax.ru – 209.51.221.247
Sample detection rate for the redirection script: MD5: 35e6ddb6ce4229d36c43d9d3ccd182f3 – detected by 21 out of 44 antivirus scanners as Trojan-Downloader.JS.Iframe.dby.
Although we couldn’t reproduce the malicious exploitation taking place through bamanaco.ru and lentuiax.ru, we found out that, during the time of the attack, similar client-side exploit serving URls were also responding to the same IPs, leading us to the actual malicious payload found on two of these domains.
Responding to same IPs at the time of the attack were also the following malicious domains:
hxxp://ganiopatia.ru:8080/forum/links/column.php
hxxp://dimarikanko.ru/forum/links/column.php
Upon successful client-side exploitation, both domains serve MD5: 3a1d644172308dc358121bd2984a57a4 – detected by 30 out of 46 antivirus scanners as Trojan:Win32/Tobfy.I.
Upon execution, it creates the following process in the system:
%AppData%kb00121600.exe
It also creates the following Registry Keys:
HKEY_CURRENT_USERSoftwareMicrosoftWindows NTCFBDC89D4
HKEY_CURRENT_USERSoftwareMicrosoftWindows NTS25BC2D7B
Next it also creates the following mutexes on the system:
LocalXMM000004B8
LocalXMI000004B8
LocalXMRFB119394
LocalXMM000000C8
LocalXMI000000C8
LocalXMM000000D4
LocalXMI000000D4
LocalXMM000000F0
LocalXMI000000F0
LocalXMM00000148
LocalXMI00000148
It then phones back to 173.224.215.130/AJtw/UCygrDAA/Ud+asDAA (AS40676). The IP responds to beast.unixbsd.info – Email: abuse@psychz.net
Another MD5 is known to have phoned back to the same IP: MD5: 3bf5c62fe6e18bc93073ecf79e079020 – detected by 15 out of 45 antivirus scanners as Trojan-Ransom.Win32.PornoAsset.biiy.
We’ve already seen the same static command and control server characters used in the following previously profiled campaigns:
- Cybercriminals spamvertise bogus ‘Microsoft License Orders’ serve client-side exploits and malware
- Bogus ‘Meeting Reminder” themed emails serve malware
- ‘American Express Alert: Your Transaction is Aborted’ themed emails serve client-side exploits and malware
- Bogus IRS ‘Your tax return appeal is declined’ themed emails lead to malware
Responding to the IPs of the client-side exploits serving domains – 82.165.193.26 (AS8560); 203.80.16.81 (AS24514); 216.24.196.66 (AS40676) – are also the following malicious/fraudulent domains:
investinindia.ru
feronialopam.ru
lemonadiom.ru
monacofrm.ru
bamanaco.ru
investomanio.ru
veneziolo.ru
fanatiaono.ru
lentuiax.ru
limonadiksec.ru
fionadix.ru
forumibiza.ru
investomanio.ru
geforceexlusive.ru
finitolaco.ru
monacofrm.ru
lemonadiom.ru
panasonicviva.ru
sonatanamore.ru
veneziolo.ru
linkrdin.ru
neighborhoodappraiser.com
jpjay.co.uk
findlocalappraiser.com
4egos.com
neighborhoodappraisers.com
musthavecentral.com
findaneighborhoodappraiser.com
reputationangels.com
findneighborhoodappraiser.com
A huge percentage of these domains have been previously profiled in a series of malicious campaigns, indicating that these campaigns continue getting launched by the same cybercriminal/gang of cybercriminals.
Name servers part of the campaign’s infrastructure:
ns1.investinindia.ru – 62.76.178.233
ns2.investinindia.ru – 41.168.5.140
ns3.investinindia.ru – 132.248.49.112
ns4.investinindia.ru – 209.51.221.247
ns1.feronialopam.ru – 62.76.178.233
ns2.feronialopam.ru – 41.168.5.140
ns3.feronialopam.ru – 132.248.49.112
ns4.feronialopam.ru – 209.51.221.247
ns1.lemonadiom.ru – 85.143.166.170
ns2.lemonadiom.ru – 132.248.49.112
ns3.lemonadiom.ru – 84.22.100.108
ns4.lemonadiom.ru – 213.251.171.30
ns1.monacofrm.ru – 62.76.178.233
ns2.monacofrm.ru – 41.168.5.140
ns3.monacofrm.ru – 132.248.49.112
ns4.monacofrm.ru – 209.51.221.247
ns1.bamanaco.ru – 62.76.178.233
ns2.bamanaco.ru – 41.168.5.140
ns3.bamanaco.ru – 132.248.49.112
ns4.bamanaco.ru – 209.51.221.247
ns1.investomanio.ru – 62.76.178.233
ns2.investomanio.ru – 41.168.5.140
ns3.investomanio.ru – 132.248.49.112
ns4.investomanio.ru – 209.51.221.247
ns1.veneziolo.ru – 62.76.178.233
ns2.veneziolo.ru – 41.168.5.140
ns3.veneziolo.ru – 132.248.49.112
ns4.veneziolo.ru – 209.51.221.247
ns1.fanatiaono.ru – 62.76.178.233
ns2.fanatiaono.ru – 41.168.5.140
ns3.fanatiaono.ru – 132.248.49.112
ns4.fanatiaono.ru – 209.51.221.247
ns1.lentuiax.ru – 62.76.178.233
ns2.lentuiax.ru – 41.168.5.140
ns3.lentuiax.ru – 132.248.49.112
ns4.lentuiax.ru – 209.51.221.247
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.