In the midst of the holidays season, cybercriminals are currently spamvertising tens of thousands of malicious “Flight Reservation Confirmations“, in an attempt to trick users into clicking on the link found in the fake emails. Once they click on the link, users are exposed to the client-side exploits served by the latest version of the Black Hole Exploit Kit.
More details:
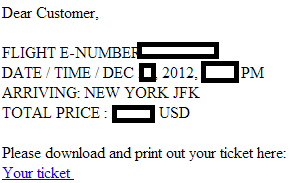
Sample screenshot of the spamvertised email:
Sample compromised URLs used in the campaign: hxxp://minjust.isfb.ru/mail.htm; hxxp://wrigglepot.com/mail.htm
Sample client-side exploits serving URL: hxxp://cinemaallon.ru:8080/forum/links/column.php
Sample malicious payload dropping URL: hxxp://cinemaallon.ru:8080/forum/links/column.php?column.php?
swo=030b360207&sdxuyi=46&wgqadt=3307093738070736060b&jtoasosd=02000200020002%22%20width=%221%22%20height=%221%22
Sample client-side exploits served: CVE-2010-0188
Surprisingly, upon successful client-side exploitation, the campaign returns an empty response, indicating that the cybercriminals behind the campaign have applied a low QA (Quality Assurance) to this particular campaign.
Malicious domain name reconnaissance:
cinemaallon.ru – 42.121.116.38 (AS37963); 202.180.221.186 (AS24496); 208.87.243.131 (AS40676)
ns1.cinemaallon.ru – 62.76.189.72
ns2.cinemaallon.ru – 41.168.5.140
ns3.cinemaallon.ru – 132.248.49.112
ns4.cinemaallon.ru – 209.51.221.247
ns5.cinemaallon.ru – 208.87.243.196
ns6.cinemaallon.ru – 216.99.149.226
We’ve already seen these IPs in the recently profiled “Malicious ‘Sendspace File Delivery Notifications’ lead to Black Hole Exploit Kit“, indicating that both campaigns have been launched by the same malicious party.
We’re also aware of more client-side exploits serving URLs that used to respond to these IPs in the past, for instance:
hxxp://ganiopatia.ru:8080/forum/links/column.php
hxxp://publicatorian.ru:8080/forum/links/public_version.php
hxxp://dimarikanko.ru:8080/forum/links/column.php
hxxp://podarunoki.ru:8080/forum/links/column.php
hxxp://gurmanikia.ru:8080/forum/links/column.php
hxxp://somaliaonfloor.ru:8080/forum/links/public_version.php
hxxp://aliamognoa.ru:8080/forum/links/public_version.php
hxxp://cinemaallon.ru:8080/forum/links/column.php
hxxp://leberiasun.ru:8080/forum/links/column.php
hxxp://dimarikanko.ru:8080/forum/links/column.php
hxxp://delemiator.ru:8080/forum/links/column.php
hxxp://ganalionomka.ru:8080/forum/links/public_version.php
Dropped MD5s upon successful client-side exploitation:
hxxp://ganiopatia.ru:8080/forum/links/column.php – MD5: a8ccedc5fe10ea98cb84a8ad20901d8e – detected by 28 out of 44 antivirus scanners as Worm:Win32/Cridex.E
hxxp://dimarikanko.ru:8080/forum/links/column.php – MD5: a8ccedc5fe10ea98cb84a8ad20901d8e – detected by 28 out of 44 antivirus scanners as Worm:Win32/Cridex.E
hxxp://podarunoki.ru:8080/forum/links/column.php – MD5: a8ccedc5fe10ea98cb84a8ad20901d8e – detected by 28 out of 44 antivirus scanners as Worm:Win32/Cridex.E
hxxp://dimarikanko.ru:8080/forum/links/column.php – MD5: a8ccedc5fe10ea98cb84a8ad20901d8e – detected by 28 out of 44 antivirus scanners as Worm:Win32/Cridex.E
hxxp://delemiator.ru:8080/forum/links/column.php – MD5: 8229f69bc416cdca7f314f19fe7b4e18 – detected by 36 out of 44 antivirus scanners as Worm:Win32/Cridex.E
hxxp://ganalionomka.ru:8080/forum/links/public_version.php – MD5: 08389cb32629aeb9dcb178dfde9bf728 – detected by 31 out of 46 antivirus scanners as Worm:Win32/Cridex.E
hxxp://publicatorian.ru:8080/forum/links/public_version.php – MD5: b59e13c6a3c6c1ccd322ba39a7085f08 – detected by 25 out of 45 antivirus scanners as Worm:Win32/Cridex.E
Responding to these IPs (42.121.116.38 (AS37963); 202.180.221.186 (AS24496); 208.87.243.131 (AS40676) are also the following malicious domains:
ganiopatia.ru
pelamutrika.ru
francese.ru
podarunoki.ru
publicatorian.ru
cinemaallon.ru
pitoniamason.ru
leberiasun.ru
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.