British Airways customers, watch out!
Cybercriminals have resumed spamvertising fake British Airways themed E-receipts — we intercepted the same campaign back in October — in an attempt to trick its customers into executing the malicious attachment found in the emails.
More details:
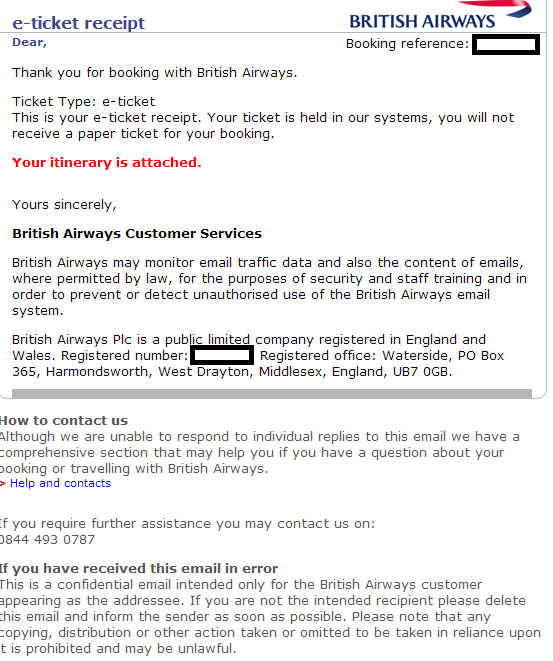
Sample screenshot of the spamvertised email:
Sample detection rate for the malicious attachment:
MD5: b46709cf7a6ff6071a6342eff3699bf0 – detected by 39 out of 46 antivirus scanners as Worm:Win32/Gamarue.I
Upon execution, it creates the following mutex on infected hosts:
SHIMLIB_LOG_MUTEX
It also initiates POST requests to the following IP:
87.255.51.229/ff/image.php
As well as DNS requests to the following hosts:
zzbb45nnagdpp43gn56.com – 87.255.51.229
a9h23nuian3owj12.com – 87.255.51.229
zzbg1zv329sbgn56.com – 87.255.51.229
www.update.microsoft.com – 65.55.185.26
ddbbzmjdkas.us
ddbbzmjdkas.us
The IPs are currently sinkholed by Abuse.ch.
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.