Certified Public Accountants (CPAs) are a common target for cybercriminals. Throughout 2012, we intercepted several campaigns directly targeting CPAs in an attempt to trick them into clicking on the malicious links found in the emails. Once they click on any of the links, they’re automatically exposed to the client-side exploits served by the latest version of the Black Hole Exploit Kit.
In this post, I’ll analyze one of the most recently spamvertised campaigns impersonating the American Institute of Certified Public Accountants, also known as AICPA.
More details:
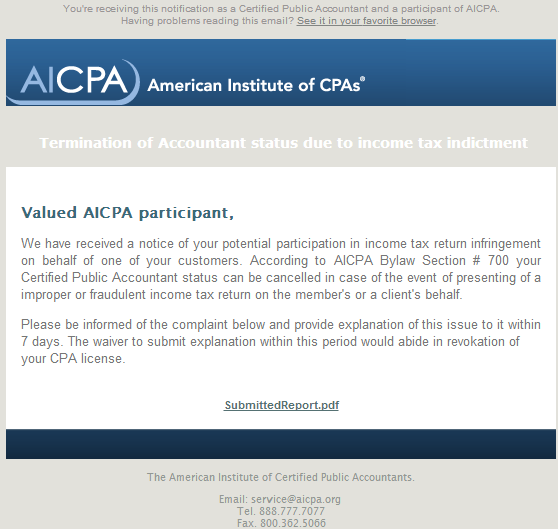
Sample screenshot of the spamvertised email:
Second screenshot of the spamvertised email from the same campaign:
Sample subjects: Tax return assistance contrivance; Suspension of your CPA license; Revocation of your CPA license; Your accountant license can be end off; Your accountant CPA License Expiration
Email message: Valued AICPA participant, We have received a notice of your potential participation in income tax return infringement on behalf of one of your customers. According to AICPA Bylaw Section # 700 your Certified Public Accountant status can be cancelled in case of the event of presenting of a improper or fraudulent income tax return on the member’s or a client’s behalf. Please be informed of the complaint below and provide explanation of this issue to it within 7 days. The waiver to submit explanation within this period would abide in revokation of your CPA license.
Sample compromised URLs participating in the campaign:
hxxp://acitcpatiala.com/components/com_ag_google_analytics2/aicpataxcompl.html
hxxp://wohnbau-rastatt.com/components/com_ag_google_analytics2/aicpataxcompl.html
hxxp://qebelemescidi.com/components/com_ag_google_analytics2/aicpataxcompl.html
hxxp://chooum.com/components/com_ag_google_analytics2/aicpataxcompl.html
hxxp://kentplus-temizlik.com/components/com_ag_google_analytics2/aicpataxcompl.html
hxxp://qebelemescidi.com/components/com_ag_google_analytics2/aicpataxcompl.html
hxxp://lexisdei.org/components/com_ag_google_analytics2/taxfraudalert.html
hxxp://javaautoparts.com/components/com_ag_google_analytics2/taxfraudalert.html
hxxp://lexisdei.org/components/com_ag_google_analytics2/taxfraudalert.html
hxxp://irbuild.com/components/com_ag_google_analytics2/taxfraudalert.html
hxxp://porsancristobal.com/components/com_ag_google_analytics2/taxfraudalert.html
hxxp://investrus.info/components/com_ag_google_analytics2/taxfraudalert.html
hxxp://facesittingextrememf.com/components/com_ag_google_analytics2/taxfraudalert.html
Sample client-side exploits serving URLs:
hxxp://ibertomoralles.org/detects/five-wise_leads_ditto.php
hxxp://eaglepointecondo.org/detects/denouncement-reports.php
hxxp://eaglepointecondo.co/detects/denouncement-reports.php
Sample malicious payload dropping URL:
hxxp://eaglepointecondo.org/detects/denouncement-reports.php?qf=1g:2v:33:2v:2w&ve=1o:32:2v:1n:2w:30:1m:1j:32:1m&y=1f&mf=i&om=y
Upon successful client-side exploitation, the campaign drops MD5: 5b7aafd9ab99aa2ec0e879a24610844a – detected by 31 out of 45 antivirus scanners as Worm:Win32/Cridex.E.
Once executed, the sample performs the following actions:
- Creates a batch script
- Accesses Firefox’s Password Manager local database
- Creates a thread in a remote process
- Installs a program to run automatically at logon
It also drops the following MD5 on the affected hosts: MD5: 3e2df81077283e5c9d457bf688779773 – detected by 27 out of 45 antivirus scanners as PWS:Win32/Fareit.
It also phones back to the following C&C servers:
hxxp://69.64.89.82:8080/DPNilBA/ue1elBAAAA/tlSHAAAAA/
132.248.49.112
173.192.229.36
64.120.193.112
89.221.242.217
174.143.174.136
209.51.221.247
We’ve also seen and profiled the same IP (132.248.49.112) in multiple previously analyzed malware campaigns:
- ‘Fwd: Scan from a Xerox W. Pro’ themed emails lead to Black Hole Exploit Kit
- Malicious ‘Security Update for Banking Accounts’ emails lead to Black Hole Exploit Kit
- Bogus Facebook ‘pending notifications’ themed emails serve client-side exploits and malware
- Bogus ‘Intuit Software Order Confirmations’ lead to Black Hole Exploit Kit
- Bogus ‘End of August Invoices’ themed emails serve malware and client-side exploits
- ‘Copies of Missing EPLI Policies’ themed emails lead to Black Hole Exploit Kit
- Spamvertised ‘Fwd: Scan from a Hewlett-Packard ScanJet’ emails lead to Black Hole exploit kit
- Cybercriminals impersonate Intuit Market, mass mail millions of exploits and malware serving emails
- Fake ‘UPS Delivery Confirmation Failed’ themed emails lead to Black Hole Exploit Kit
- Fake ‘Flight Reservation Confirmations’ themed emails lead to Black Hole Exploit Kit
- Multiple ‘Inter-company’ invoice themed campaigns serve malware and client-side exploits
- Malicious ‘Sendspace File Delivery Notifications’ lead to Black Hole Exploit Kit
- Cybercriminals spamvertise bogus ‘Microsoft License Orders’ serve client-side exploits and malware
- Spamvertised ‘Wire Transfer Confirmation’ themed emails lead to Black Hole exploit kit
- Cybercriminals impersonate UPS, serve client-side exploits and malware
Upon execution, the sample also creates the following mutexes:
LocalXMM000005D4
SHIMLIB_LOG_MUTEX
LocalXMM00000264
LocalXMQ426FB97F
LocalXMM000001D0
and the following Registry Keys:
REGISTRYUSERS-1-5-21-299502267-926492609-1801674531-500SoftwareMicrosoftWindows NTCBA6D3F36
REGISTRYUSERS-1-5-21-299502267-926492609-1801674531-500SoftwareMicrosoftWindows NTS9CC20790
Malicious domain names reconnaissance:
eaglepointecondo.org – 59.57.247.185
Name Server:NS1.AMISHSHOPPE.NET – 84.32.116.189 – Email: solaradvent@yahoo.com
Name Server:NS2.AMISHSHOPPE.NET – 211.27.42.138 – Email:
eaglepointecondo.co – 59.57.247.185
Name Server:NS1.AMISHSHOPPE.NET – 84.32.116.189 – Email: solaradvent@yahoo.com
Name Server:NS2.AMISHSHOPPE.NET – 211.27.42.138 – Email: solaradvent@yahoo.com
ibertomoralles.org – Email: rick.baxter@costcontrolsoftware.com
Responding to the same IP (59.57.247.185) in the time of posting this analysis are also the following malicious domains:
moid.pl
securityday.pl
pleansantwille.com
labpr.com
ibertomoralles.com
shopgreatvideonax.com
eaglepointecondo.co
zindt.net
naky.net
svictrorymedia.ru
ygsecured.ru
romoviebabenki.ru
robertokarlosskiy.su
africanbeat.net
incinteractive.net
lloydstsb-offshoren.com
sessionid0147239047829578349578239077.pl
We’ve already seen the same name servers (NS1.AMISHSHOPPE.NET; NS2.AMISHSHOPPE.NET) used in the following previously profiled campaigns, indicating that all of these campaigns have been launched by the same malicious party.
- Fake BBB (Better Business Bureau) Notifications lead to Black Hole Exploit Kit
- Spamvertised ‘Your Recent eBill from Verizon Wireless’ themed emails serve client-side exploits and malware
- Fake ‘Citi Account Alert’ themed emails lead to Black Hole Exploit Kit
Webroot SecureAnywhere users are proactively protected from these threats.
To find more about Dancho Danchev, follow him on Twitter.