Over the past 24 hours, cybercriminals resumed spamvertising fake Vodafone MMS themed emails, in an attempt to trick the company’s customers into executing the malicious attachment found in these emails.
More details:
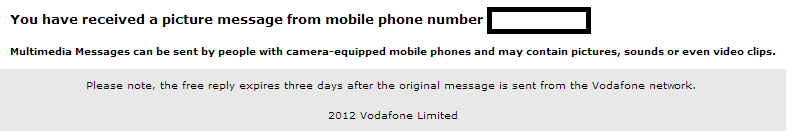
Sample screenshot of the spamvertised email:
Detection rate for the malicious executable:
MD5: bafebf4cdf640520e6266eb05b55d7c5 – detected by 21 out of 46 antivirus scanners as Trojan-Downloader.Win32.Andromeda.pfu.
Once executed, the sample creates the following Registry values:
SoftwareMicrosoftWindowsCurrentVersionRunSunJavaUpdateSched -> “C:Documents and SettingsAll Userssvchost.exe”
It also copies itself to other locations, and injects code in other processess.
We intercepted a similar campaign last year, indicating that, depending on the campaign in question, cybercriminals are not always interested in popping up on everyone’s radar with persistent and systematic spamvertising of campaigns using identical templates. Instead, some of their campaigns tend to have a rather short-lived life cycle. We believe this practice is entirely based on the click-through rates for malicious URLs and actual statistics on the number of people that executed the malicious samples.
Webroot SecureAnywhere users are proactively protected from these threats.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.